Jul 31, 2025Ravie LakshmananCyber Espionage / Community Safety
The Russian nation-state risk actor referred to as Secret Blizzard has been noticed orchestrating a brand new cyber espionage marketing campaign concentrating on international embassies situated in Moscow by way of an adversary-in-the-middle (AitM) assault on the Web Service Supplier (ISP) degree and delivering a customized malware dubbed ApolloShadow.
“ApolloShadow has the potential to put in a trusted root certificates to trick units into trusting malicious actor-controlled websites, enabling Secret Blizzard to keep up persistence on diplomatic units, doubtless for intelligence assortment,” the Microsoft Risk Intelligence crew mentioned in a report shared with The Hacker Information.
The exercise is assessed to be ongoing since no less than 2024, with the marketing campaign posing a safety threat to diplomatic personnel counting on native ISPs or telecommunications providers in Russia.
Secret Blizzard (previously Krypton), affiliated with the Russian Federal Safety Service, can also be tracked by the broader cybersecurity neighborhood underneath the monikers Blue Python, Iron Hunter, Pensive Ursa, Snake, SUMMIT, Uroburos, Turla, Venomous Bear, and Waterbug.
In December 2024, Microsoft and Lumen Applied sciences Black Lotus Labs disclosed the hacking group’s use of a Pakistan-based risk actor’s command-and-control (C2) infrastructure to hold out its personal assaults as a option to cloud attribution efforts.
The adversary has additionally been noticed piggybacking on malware related to different risk actors to ship its Kazuar backdoor heading in the right direction units situated in Ukraine.
The Home windows maker famous that the AitM place is probably going facilitated by lawful intercept and consists of the set up of root certificates underneath the guise of Kaspersky antivirus to acquire elevated entry to the system.
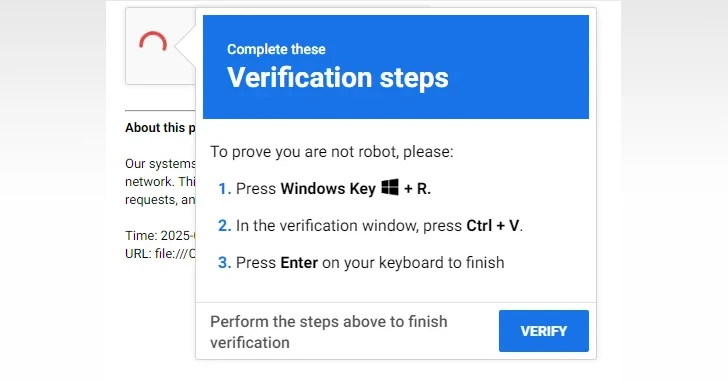
Preliminary entry is achieved by redirecting goal units to risk actor-controlled infrastructure by placing them behind a captive portal, resulting in the obtain and execution of the ApolloShadow malware.
“As soon as behind a captive portal, the Home windows Check Connectivity Standing Indicator is initiated—a official service that determines whether or not a tool has web entry by sending an HTTP GET request to hxxp://www.msftconnecttest[.]com/redirect, which ought to direct to msn[.]com,” Microsoft mentioned.
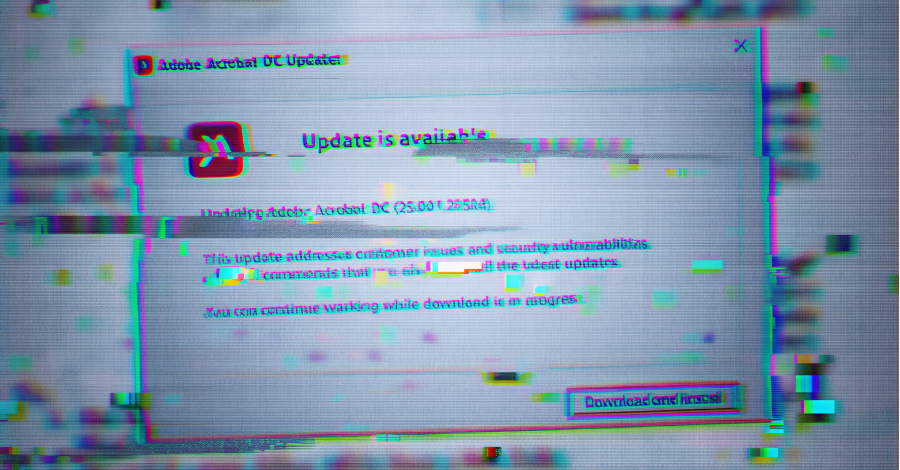
“As soon as the system opens the browser window to this tackle, the system is redirected to a separate actor-controlled area that doubtless shows a certificates validation error, which prompts the goal to obtain and execute ApolloShadow.”
The malware then beacons host data to the C2 server and runs a binary referred to as CertificateDB.exe ought to the gadget not be operating on default administrative settings, and retrieves as a second-stage payload an unknown Visible Fundamental Script.
Within the final step, the ApolloShadow course of launches itself once more and presents the consumer with a consumer entry management (UAC) pop-up window and instructs them to grant it the very best privileges out there to the consumer.
ApolloShadow’s execution path varies if the operating course of is already operating with enough elevated privileges, abusing them to set all networks to Non-public through registry profile modifications and create an administrative consumer with the username UpdatusUser and a hard-coded password, permitting persistent entry to the machine.
“This induces a number of modifications, together with permitting the host gadget to turn out to be discoverable, and enjoyable firewall guidelines to allow file sharing,” the corporate mentioned. “Whereas we didn’t see any direct makes an attempt for lateral motion, the principle motive for these modifications is more likely to scale back the issue of lateral motion on the community.”
As soon as this step is efficiently accomplished, victims are displayed a window exhibiting that the deployment of the digital certificates is in progress, inflicting two root certificates to be put in on the machine utilizing the certutil utility. Additionally dropped is a file referred to as “wincert.js” that enables Mozilla Firefox to belief the basis certificates.
To defend in opposition to Secret Blizzard exercise, diplomatic entities working in Moscow are urged to implement the precept of least privilege (PoLP), periodically overview privileged teams, and route all visitors via an encrypted tunnel to a trusted community or use a digital non-public community (VPN) service supplier.