Aug 01, 2025Ravie LakshmananMalware / Synthetic Intelligence
Cybersecurity researchers have flagged a malicious npm bundle that was generated utilizing synthetic intelligence (AI) and hid a cryptocurrency pockets drainer.
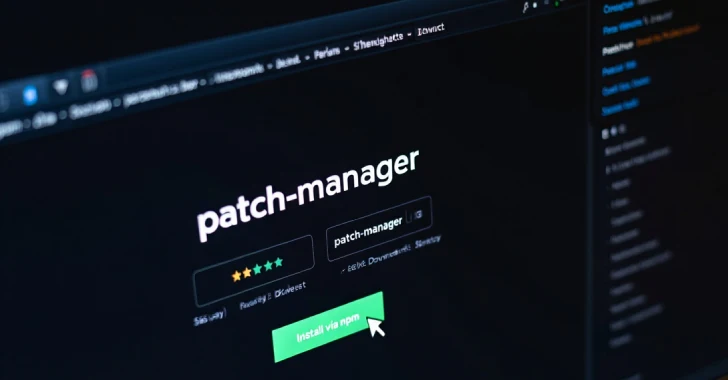
The bundle, @kodane/patch-manager, claims to supply “superior license validation and registry optimization utilities for high-performance Node.js purposes.” It was uploaded to npm by a consumer named “Kodane” on July 28, 2025. The bundle is now not accessible for obtain from the registry, however not earlier than it attracted over 1,500 downloads.
Software program provide chain safety firm Security, which found the library, mentioned the malicious options are marketed immediately within the supply code, calling it an “enhanced stealth pockets drainer.”
Particularly, the conduct is triggered as a part of a postinstall script that drops its payload inside hidden directories throughout Home windows, Linux, and macOS techniques, after which proceeds to hook up with a command-and-control (C2) server at “sweeper-monitor-production.up.railway[.]app.”
“The script generates a singular machine ID code for the compromised host and shares that with the C2 server,” Paul McCarty, head of analysis at Security, mentioned, noting that the C2 server lists two compromised machines.Within the npm ecosystem, postinstall scripts are sometimes missed assault vectors—they run robotically after a bundle is put in, that means customers might be compromised with out ever executing the bundle manually. This creates a harmful blind spot, particularly in CI/CD environments the place dependencies are up to date routinely with out direct human evaluation.
The malware is designed to scan the system for the presence of a pockets file, and if discovered, it proceeds to empty all funds from the pockets to a hard-coded pockets deal with on the Solana blockchain.
Whereas this isn’t the primary time cryptocurrency drainers have been recognized in open-source repositories, what makes @kodane/patch-manager stand out are clues that counsel the usage of Anthropic’s Claude AI chatbot to generate it.
This contains the presence of emojis, in depth JavaScript console logging messages, well-written and descriptive feedback, the README.md markdown file written in a method that is in keeping with Claude-generated markdown recordsdata, and Claude’s sample of calling code adjustments as “Enhanced.”
The invention of the npm bundle highlights “how risk actors are leveraging AI to create extra convincing and harmful malware,” McCarty mentioned.The incident additionally underlines rising issues in software program provide chain safety, the place AI-generated packages could bypass typical defenses by showing clear and even useful. This raises the stakes for bundle maintainers and safety groups, who now want to watch not simply identified malware, however more and more polished, AI-assisted threats that exploit trusted ecosystems like npm.