Could 13, 2025Ravie LakshmananZero-Day / Vulnerability
A Türkiye-affiliated menace actor exploited a zero-day safety flaw in an Indian enterprise communication platform known as Output Messenger as a part of a cyber espionage assault marketing campaign since April 2024.
“These exploits have resulted in a set of associated consumer information from targets in Iraq,” the Microsoft Risk Intelligence workforce mentioned. “The targets of the assault are related to the Kurdish navy working in Iraq, in step with beforehand noticed Marbled Mud focusing on priorities.”
The exercise has been attributed to a menace group it tracks as Marbled Mud (previously Silicon), which is also called Cosmic Wolf, Sea Turtle, Teal Kurma, and UNC1326. The hacking crew is believed to have been energetic since at the least 2017, though it wasn’t till two years later that Cisco Talos documented assaults focusing on private and non-private entities within the Center East and North Africa.
Early final yr, it was additionally recognized as focusing on telecommunication, media, web service suppliers (ISPs), data expertise (IT)-service suppliers, and Kurdish web sites within the Netherlands.
Microsoft has assessed with reasonable confidence that the menace actor has performed some kind of reconnaissance beforehand to find out if its targets are Output Messenger customers after which leverage the zero-day to distribute malicious payloads and exfiltrate information from targets.
The vulnerability in query is CVE-2025-27920, a listing traversal vulnerability affecting model 2.0.62 that permits distant attackers to entry or execute arbitrary recordsdata. The problem has been addressed by its developer Srimax as of late December 2024 with model 2.0.63. The corporate, nevertheless, makes no point out of the flaw being exploited within the wild in its advisory.
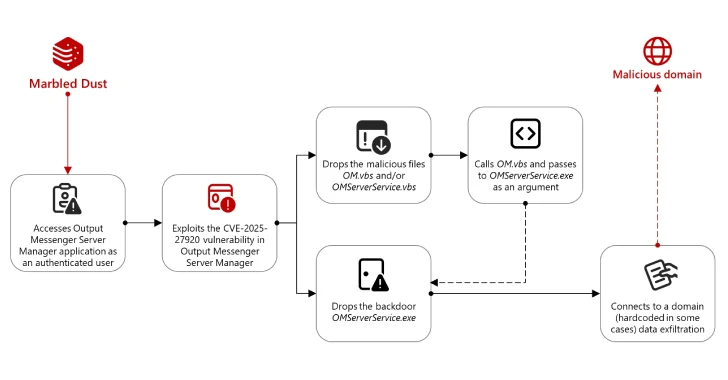
The assault chain begins with the menace actor getting access to the Output Messenger Server Supervisor utility as an authenticated consumer. It is believed that Marbled Mud makes use of strategies like DNS hijacking or typosquatted domains to intercept the credentials required for authentication.
The entry is then abused to gather the consumer’s Output Messenger credentials and exploit CVE-2025-27920 to drop payloads like “OM.vbs” and “OMServerService.vbs” to the server startup folder and “OMServerService.exe” to the server’s “Customers/public/movies” listing.
Within the subsequent part, the menace actor makes use of “OMServerService.vbs” to invoke “OM.vbs” and “OMServerService.exe,” the latter of which is a Golang backdoor that contacts a hard-coded area (“api.wordinfos[.]com”) for information exfiltration.
“On the shopper aspect, the installer extracts and executes each the reputable file OutputMessenger.exe and OMClientService.exe, one other Golang backdoor that connects to a Marbled Mud command-and-control (C2) area,” Microsoft famous.
“This backdoor first performs a connectivity test by way of a GET request to the C2 area api.wordinfos[.]com. If profitable, a second GET request is shipped to the identical C2 containing hostname data to uniquely establish the sufferer. The response from the C2 is then instantly executed utilizing the command ‘cmd /c’ which instructs the Home windows command immediate to run a particular command after which terminate.”
At one case concerned a sufferer system with Output Messenger shopper software program put in connecting to an IP tackle beforehand recognized as utilized by Marbled Mud for seemingly information exfiltration.
The tech large additionally famous that it found a second flaw, mirrored cross-site scripting (XSS) vulnerability in the identical model (CVE-2025-27921), though it mentioned it discovered no proof of it being weaponized in real-world assaults.
“This new assault indicators a notable shift in Marbled Mud’s functionality whereas sustaining consistency of their total method,” Microsoft mentioned. “The profitable use of a zero-day exploit suggests a rise in technical sophistication and will additionally counsel that Marbled Mud’s focusing on priorities have escalated or that their operational objectives have turn out to be extra pressing.”
Discovered this text fascinating? Observe us on Twitter and LinkedIn to learn extra unique content material we put up.