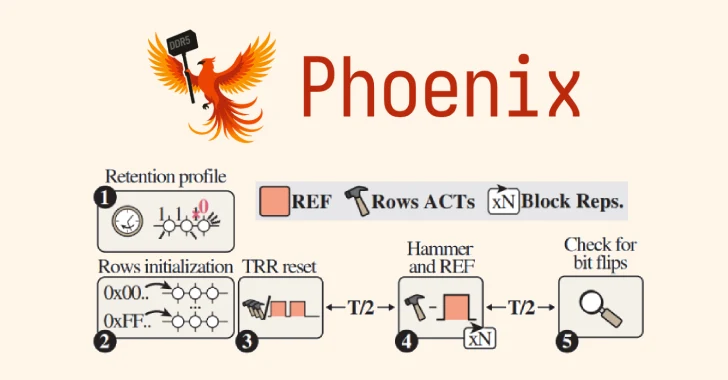
Aug 04, 2025Ravie LakshmananMalware / Browser Safety
Cybersecurity researchers are calling consideration to a brand new wave of campaigns distributing a Python-based info stealer known as PXA Stealer.
The malicious exercise has been assessed to be the work of Vietnamese-speaking cybercriminals who monetize the stolen information via a subscription-based underground ecosystem that automates the resale and reuse through Telegram APIs, in accordance with a joint report revealed by Beazley Safety and SentinelOne and shared with The Hacker Information.
“This discovery showcases a leap in tradecraft, incorporating extra nuanced anti-analysis strategies, non-malicious decoy content material, and a hardened command-and-control pipeline that frustrates triage and makes an attempt to delay detection,” safety researchers Jim Walter, Alex Delamotte, Francisco Donoso, Sam Mayers, Inform Hause, and Bobby Venal mentioned.
The campaigns have contaminated over 4,000 distinctive IP addresses spanning 62 international locations, together with South Korea, the US, the Netherlands, Hungary, and Austria. Knowledge captured through the stealer contains greater than 200,000 distinctive passwords, a whole bunch of bank card data, and greater than 4 million harvested browser cookies.
PXA Stealer was first documented by Cisco Talos in November 2024, attributing it to assaults focusing on authorities and training entities in Europe and Asia. It is able to harvesting passwords, browser autofill information, info from cryptocurrency wallets and monetary establishments.
Knowledge stolen by the malware utilizing Telegram as an exfiltration channel is fed into felony platforms like Sherlock, a purveyor of stealer logs, from the place downstream risk actors should buy the knowledge to interact in cryptocurrency theft or infiltrate organizations for follow-on functions, fueling a cybercriminal ecosystem that runs at scale.
Campaigns distributing the malware in 2025 have witnessed a gentle tactical evolution, with the risk actors using DLL side-loading strategies and elaborate staging layers in an effort to fly beneath the radar.
The malicious DLL takes care of conducting the remainder of the steps within the an infection sequence, finally paving the best way for the deployment of the stealer, however not earlier than taking steps to show a decoy doc, akin to a copyright infringement discover, to the sufferer.
The stealer is an up to date model boasting capabilities to extract cookies from Chromium-based internet browsers by injecting a DLL into working situations with an purpose to defeat app-bound encryption safeguards. It additionally plunders information from VPN shoppers, cloud command-line interface (CLI) utilities, linked fileshares, and purposes like Discord.
“PXA Stealer makes use of the BotIDs (saved as TOKEN_BOT) to determine the hyperlink between the primary bot and the varied ChatID (saved as CHAT_ID),” the researchers mentioned. “The ChatIDs are Telegram channels with numerous properties, however they primarily serve to host exfiltrated information and supply updates and notifications to the operators.”
“This risk has since matured right into a extremely evasive, multi-stage operation pushed by Vietnamese-speaking actors with obvious ties to an organized cybercriminal Telegram-based market that sells stolen sufferer information.”