A possible zero-day vulnerability in SonicWall’s Safe Cell Entry (SMA) VPNs and firewall home equipment is being actively exploited within the wild, enabling attackers to bypass multi-factor authentication (MFA) and deploy ransomware inside hours of the preliminary breach.
Safety companies, together with Huntress, Arctic Wolf, and Sophos, have reported a current surge in high-severity incidents focusing on these gadgets, indicating a crucial and ongoing risk to organizations that depend on them.
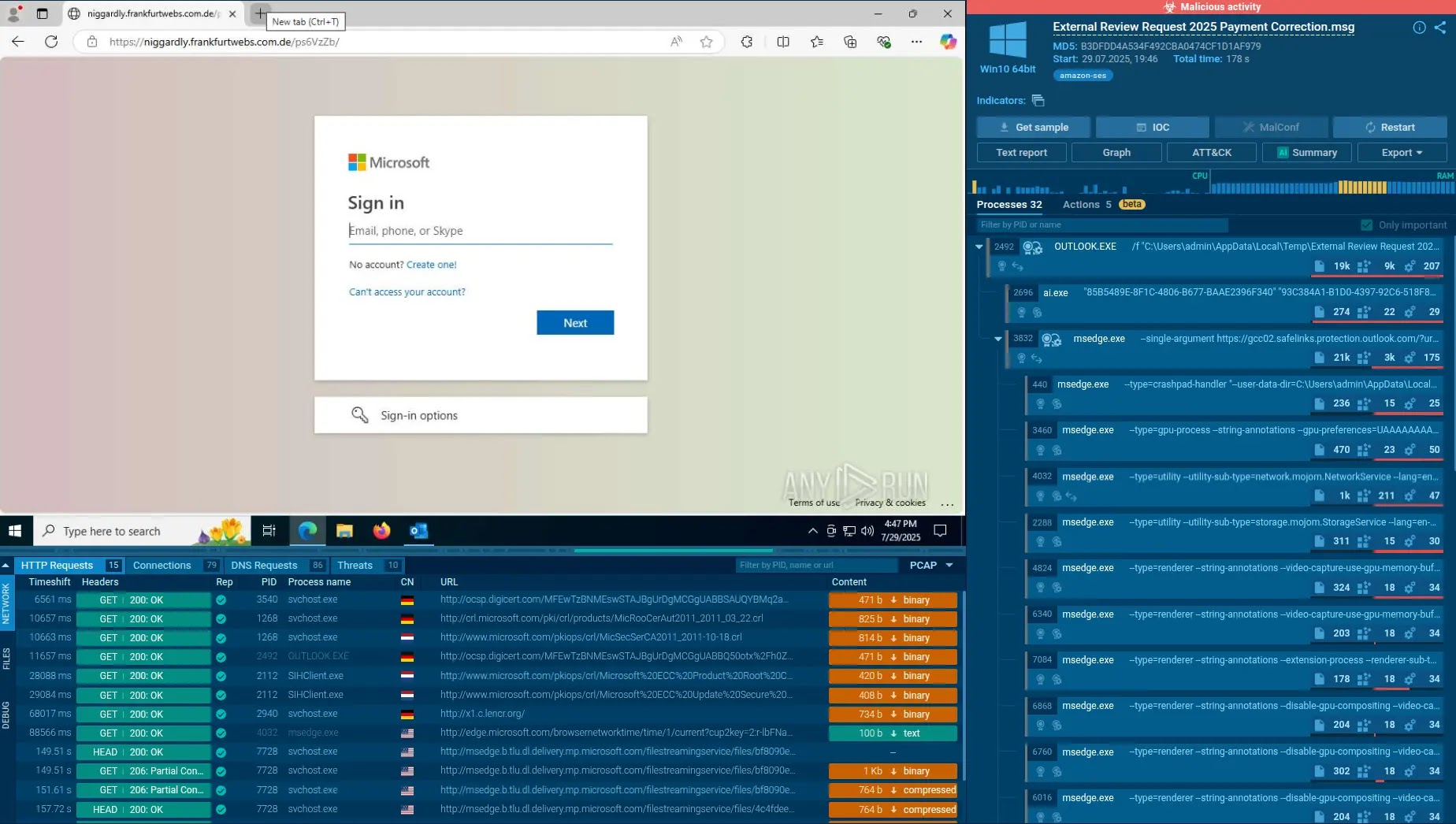
The assaults observe a swift and constant playbook, starting with a breach of the SonicWall equipment itself. Safety researchers at Huntress, who’ve been responding to a wave of those incidents since late July 2025, report that the pace and success of the assaults, even in opposition to environments with MFA enabled, strongly level to an unpatched vulnerability.
Compromised Accounts Timeline
As soon as risk actors acquire an preliminary foothold, they transfer quickly to compromise all the community. Attackers have been noticed instantly leveraging over-privileged service accounts, comparable to LDAP or administrative accounts utilized by the SonicWall gadget, to realize administrative entry.
To make sure persistent entry, they deploy instruments like Cloudflared tunnels and OpenSSH, successfully making a backdoor into the compromised community.
With elevated privileges, the attackers proceed with a mixture of automated scripts and hands-on methods to maneuver laterally. They’ve been seen utilizing WMI and PowerShell Remoting to navigate the community, dump credentials from Veeam Backup databases, and exfiltrate the Energetic Listing database (NTDS.dit) for offline password cracking.
Earlier than deploying the ultimate payload, the attackers methodically dismantle safety defenses. They use built-in Home windows instruments to disable Microsoft Defender and modify firewall guidelines to permit their very own distant entry.
The ultimate stage includes deleting Quantity Shadow Copies to stop simple system restoration, instantly adopted by the deployment of what has been recognized as Akira ransomware.
The tradecraft varies between assaults, suggesting that a number of risk actors could also be exploiting the identical vulnerability with totally different toolsets.
Noticed strategies embrace utilizing authentic instruments like Superior IP Scanner and WinRAR for reconnaissance and knowledge staging, alongside living-off-the-land binaries (LOLBins) and customized scripts. Attackers have additionally been caught creating new person accounts to take care of their presence on the community.
In response to this energetic risk, safety consultants are issuing pressing suggestions. Huntress strongly advises organizations to disable their SonicWall SSL VPN entry instantly till an official patch is launched.
If disabling the VPN will not be possible for enterprise operations, entry must be severely restricted to a whitelist of recognized, trusted IP addresses.
Moreover, it’s crucial to audit service accounts and guarantee they function beneath the precept of least privilege, as compromised high-privilege accounts are a key ingredient of the assault chain. Organizations are additionally urged to hunt for the revealed Indicators of Compromise (IOCs) inside their environments to detect any indicators of a breach.
Indicator TypeDescription or ExampleAttacker IP Addresses42.252.99[.]5945.86.208[.]24077.247.126[.]239104.238.205[.]105104.238.220[.]216181.215.182[.]64193.163.194[.]7193.239.236[.]149194.33.45[.]155Malicious Executablesw.exe (Akira ransomware)win.exe (ransomware)C:ProgramDatawinrar.exe (WinRAR)C:ProgramDataOpenSSHa.msi (OpenSSH installer)C:Program FilesOpenSSHsshd.exe (SSH exfil)C:programdatasshcloudflared.exe (Cloudflare tunnel)C:Program FilesFileZilla FTP Clientfzsftp.exe (FileZilla FTP)C:ProgramData1.bat (unknown script)C:ProgramData2.bat (unknown script)Hash (SHA-256)d080f553c9b1276317441894ec6861573fa64fb1fae46165a55302e782b1614d (w.exe)ASN/CIDR InfrastructureAS24863 – LINK-NET – 45.242.96.0/22AS62240 – Clouvider – 45.86.208.0/22AS62240 – Clouvider – 77.247.126.0/24AS23470 – ReliableSite LLC – 104.238.204.0/22AS23470 – ReliableSite LLC – 104.238.220.0/22AS174 – COGENT-174 – 181.215.182.0/24AS62240 – Clouvider – 193.163.194.0/24AS62240 – Clouvider – 193.239.236.0/23AS62240 – Clouvider – 194.33.45.0/24Created Person AccountsbackupSQLlockadminPasswords UsedPassword123$Msnc?42daVRT83g$%ce
Combine ANY.RUN TI Lookup along with your SIEM or SOAR To Analyses Superior Threats -> Strive 50 Free Trial Searches