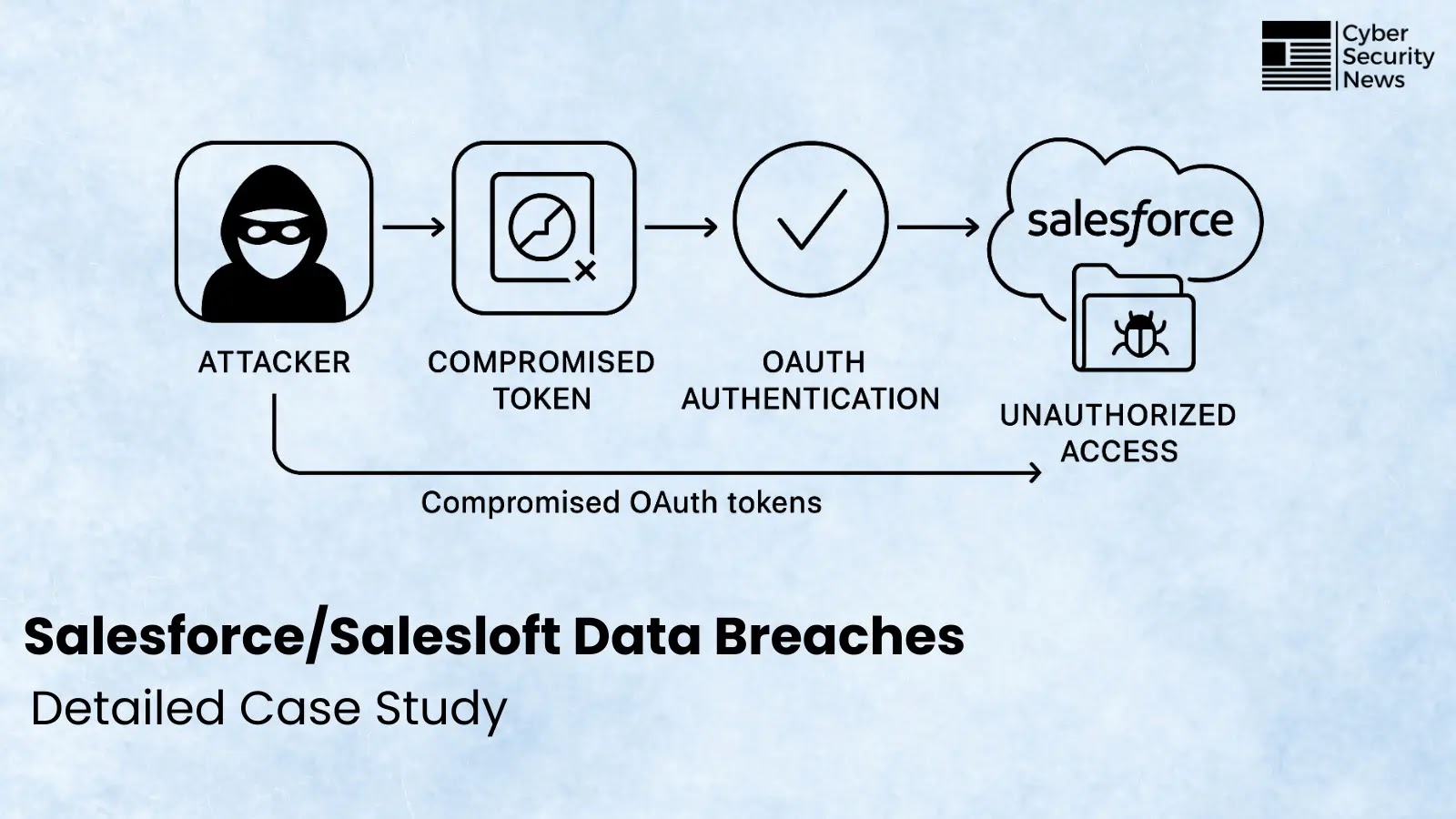
OpenAI has formally launched ChatGPT-5, a brand new technology of its AI agent that introduces a complicated, unified system designed to be quicker, extra clever, and considerably extra helpful for real-world purposes.
This launch marks a major evolution from its predecessors, providing a set of fashions tailor-made for various duties and complexities.
On the core of GPT-5 is a novel structure that includes two main fashions: gpt-5-main and gpt-5-thinking. The gpt-5-main mannequin, the successor to GPT-4o, is engineered for velocity and effectivity, dealing with the vast majority of person queries.
For more difficult issues that demand deeper reasoning, the system seamlessly shifts to gpt-5-thinking, the successor to OpenAI’s o3 mannequin.
GPT‑4o → gpt-5-main
GPT‑4o-mini → gpt-5-main-mini
OpenAI o3 → gpt-5-thinking
OpenAI o4-mini → gpt-5-thinking-mini
GPT‑4.1-nano → gpt-5-thinking-nano
OpenAI o3 Professional → gpt-5-thinking-pro
This dynamic allocation is managed by a real-time router that intelligently analyzes the context of a dialog, its complexity, and any particular person directions, similar to prompting the AI to “assume onerous about this.”
The router repeatedly learns and refines its decision-making primarily based on person interactions, together with which mannequin customers swap to and the desire charges for responses, guaranteeing it turns into extra environment friendly over time. To handle excessive demand, smaller “mini” variations of every mannequin are deployed to deal with queries as soon as utilization limits are reached.
The brand new GPT-5 household extends past these core fashions, providing specialised variations for builders and superior customers. The API offers direct entry to gpt-5-thinking, its mini counterpart, and a good quicker gpt-5-thinking-nano model.
For ChatGPT customers searching for most energy, gpt-5-thinking-pro is out there, leveraging parallel computing for enhanced efficiency.
Past architectural upgrades, GPT-5 boasts vital efficiency enhancements. OpenAI has made notable strides in decreasing hallucinations, bettering the mannequin’s capacity to comply with advanced directions, and minimizing sycophantic or overly agreeable responses.
Efficiency has been particularly upgraded in three of ChatGPT’s most typical use instances: writing, coding, and well being, reads the discharge notes.
With these superior capabilities come heightened security measures. All GPT-5 fashions are educated with “safe-completions,” a brand new strategy to stop the technology of disallowed content material.
Acknowledging its energy, OpenAI has proactively labeled the gpt-5-thinking mannequin as “Excessive functionality” within the organic and chemical domains beneath its Preparedness Framework.
Equip your SOC with full entry to the newest menace information from ANY.RUN TI Lookup that may Enhance incident response -> Get 14-day Free Trial