A complicated new ransomware household referred to as Charon has emerged within the cybersecurity panorama, focusing on organizations within the Center East’s public sector and aviation business with superior persistent risk (APT) strategies sometimes reserved for nation-state actors.
The ransomware marketing campaign represents a regarding evolution in cybercriminal operations, combining stealth, precision, and damaging capabilities to maximise impression on sufferer organizations.
The risk actors behind Charon exhibit exceptional technical sophistication by using DLL sideloading strategies that intently mirror techniques beforehand documented in Earth Baxia campaigns, which have traditionally targeted on authorities sectors.
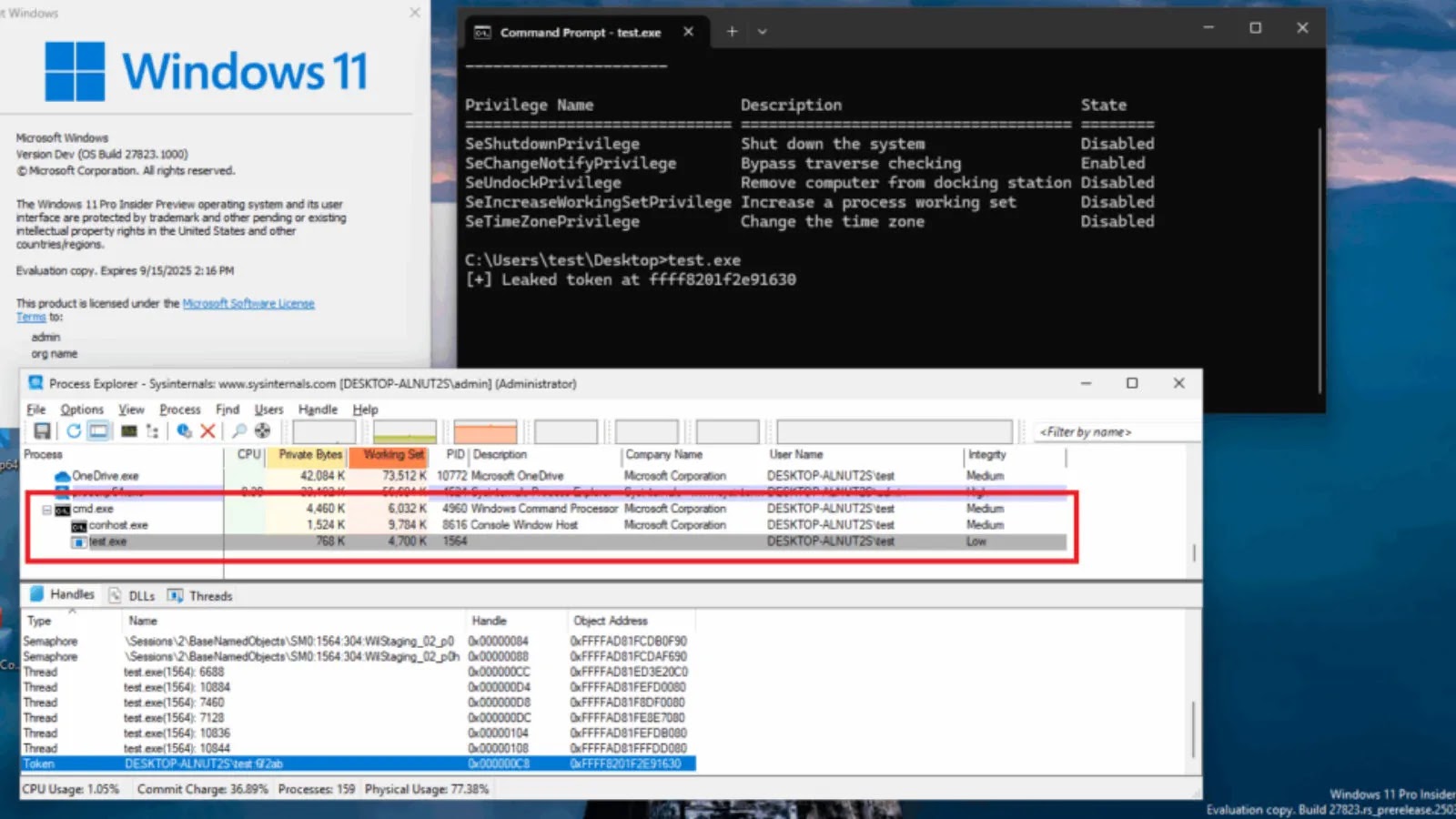
The assault chain begins with the execution of a reliable Edge.exe binary, initially named cookie_exporter.exe, which is then abused to sideload a malicious Dynamic Hyperlink Library (DLL) file named msedge.dll, internally designated as “SWORDLDR.”
Development Micro researchers recognized this marketing campaign via forensic investigation after initially lacking a crucial element referred to as DumpStack.log of their telemetry.
Upon restoration and evaluation of this file, they found it contained encrypted shellcode that, when decrypted, revealed the Charon ransomware payload.
The ransomware’s customized ransom notice particularly references sufferer organizations by identify, confirming this as a focused operation quite than an opportunistic assault.
Charon’s custom-made ransom notice (Supply – Development Micro)
The malware’s deployment technique includes a classy multistage payload extraction method. The SWORDLDR element masses the seemingly benign DumpStack.log file, which really incorporates a number of layers of encrypted shellcode.
After decryption of the primary layer, an intermediate payload emerges with embedded configuration information particularly indicating the usage of svchost.exe for course of injection, as proven within the recovered code construction.
Superior Evasion and Encryption Mechanisms
Charon’s technical structure reveals a number of superior capabilities designed to evade detection and maximize encryption effectivity.
The ransomware creates a mutex named “OopsCharonHere” to forestall a number of cases from working concurrently.
Execution move of the Charon ransomware assault (Supply – Development Micro)
Earlier than initiating encryption, it systematically disables security-related providers and terminates lively processes, together with antivirus and endpoint safety software program.
The malware employs a hybrid cryptographic scheme combining Curve25519 elliptic curve cryptography with the ChaCha20 stream cipher.
It generates a 32-byte random non-public key utilizing Home windows’ cryptographic features, then creates a public key mixed with a hardcoded public key embedded within the binary to ascertain a shared secret.
This refined encryption method contains partial file encryption methods primarily based on file measurement, with smaller information receiving full encryption whereas bigger information have strategic chunks encrypted at particular positions.
Maybe most regarding is Charon’s inclusion of anti-EDR capabilities derived from the general public Darkish-Kill undertaking.
The ransomware makes an attempt to drop a driver as WWC.sys and register it because the “WWC” service, although evaluation revealed this element stays dormant in present variants, suggesting ongoing improvement for future variations.
Increase your SOC and assist your staff shield your small business with free top-notch risk intelligence: Request TI Lookup Premium Trial.