A classy social engineering marketing campaign by the EncryptHub risk group that mixes impersonation techniques with technical exploitation to compromise company networks.
The Russian-linked cybercriminals are posing as IT help workers and utilizing Microsoft Groups requests to ascertain distant entry, finally deploying malicious payloads by a beforehand unknown Home windows vulnerability.
The assault begins with risk actors claiming to be from inner IT departments and sending Microsoft Groups connection requests to focused staff.
As soon as victims settle for the request and set up a distant session, the attackers information them by executing PowerShell instructions that seem authentic however really obtain and run malicious scripts.
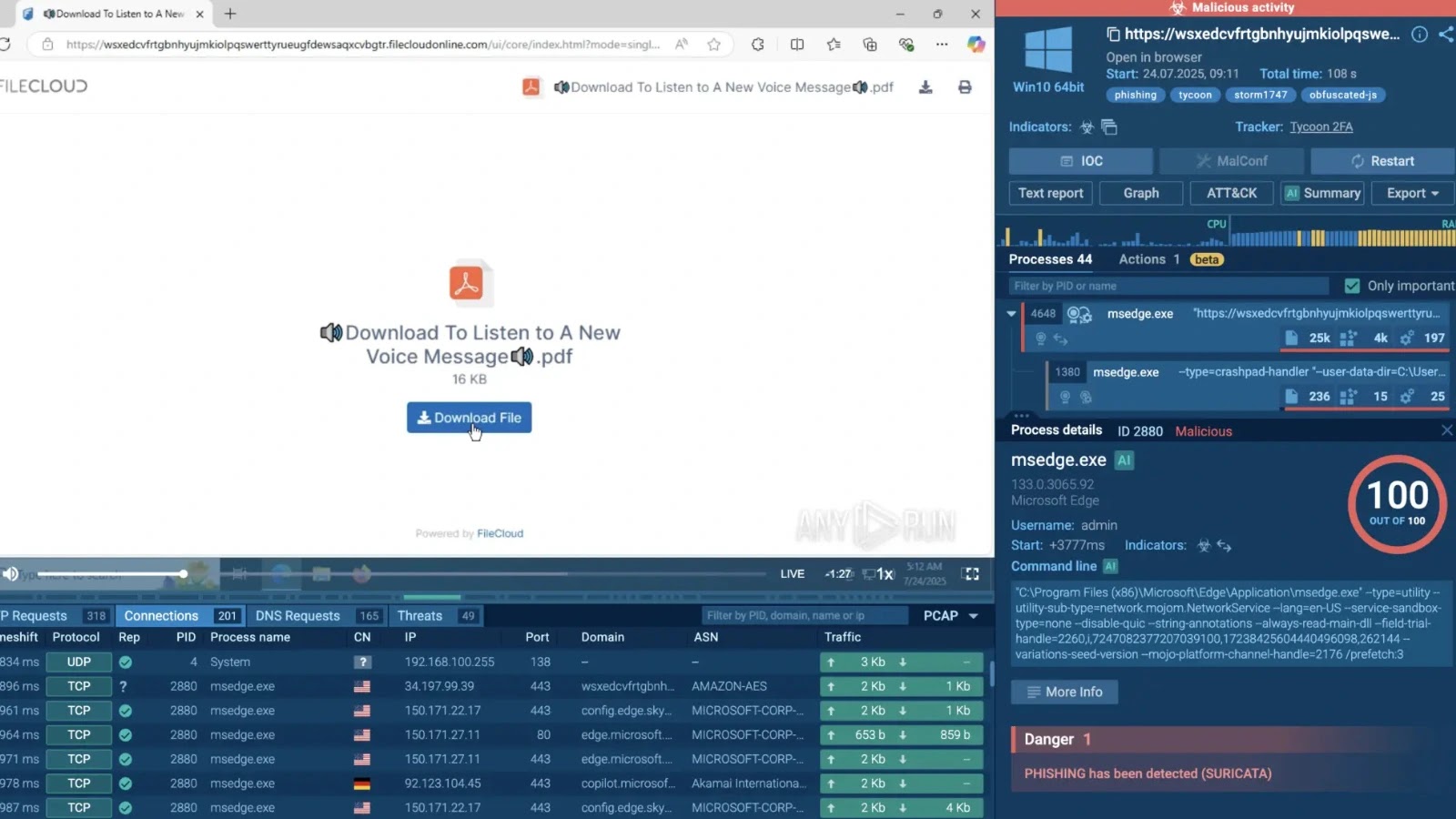
The preliminary command executed bypasses Home windows safety insurance policies and downloads a PowerShell script referred to as “runner.ps1” from attacker-controlled domains akin to cjhsbam[.]com.
This script is designed to use CVE-2025-26633, a vulnerability in Microsoft’s Administration Console framework dubbed “MSC EvilTwin”.
Microsoft Groups Requests Drop Malware
The MSC EvilTwin vulnerability permits attackers to execute malicious Microsoft Console (.msc) recordsdata by manipulating how the system masses these administrative instruments.
The exploit works by dropping two .msc recordsdata with similar names – one authentic and one malicious – in several directories. When the authentic file is executed, the system inadvertently masses the malicious model from an alternate location, particularly the MUIPath listing.
Malware Execution
“The malicious file is positioned in a distinct listing, particularly in MUIPath, usually within the en-US folder. When the authentic msc file is run, it triggers the mmc[.]exe course of.
As a result of MSC EvilTwin vulnerability, mmc.exe first checks for a file with the identical title within the MUIPath listing,” defined Trustwave researchers.
After profitable exploitation, the malware establishes persistence on contaminated machines and maintains steady communication with command-and-control servers.
The system receives AES-encrypted instructions which can be decrypted regionally and executed utilizing PowerShell, granting attackers complete distant management capabilities.
Among the many payloads deployed is Fickle Stealer, a PowerShell-based data stealer designed to extract delicate recordsdata, harvest system data, and steal cryptocurrency pockets knowledge.
The malware additionally generates pretend browser site visitors to well-liked web sites, serving to disguise malicious command-and-control communications as regular community exercise.
EncryptHub, additionally tracked as LARVA-208 and Water Gamayun, has been energetic since mid-2024 and represents a well-resourced Russian cybercriminal operation.
The group has compromised over 618 organizations worldwide as of February 2025, focusing on sectors together with Web3 builders and gaming platforms.
The risk actors have demonstrated refined operational capabilities, together with the abuse of authentic platforms for malware distribution.
Researchers found that EncryptHub has been utilizing Courageous Help, the assistance platform for the Courageous internet browser, to host malicious ZIP archives containing their payloads.
This system is especially regarding as importing recordsdata to Courageous Help usually requires established accounts with add permissions.
Past the preliminary Microsoft Groups social engineering, EncryptHub has developed an increasing arsenal of customized instruments.
Assault Chain
These embrace SilentCrystal, a Golang-compiled loader that mirrors PowerShell script performance, and a SOCKS5 proxy backdoor that operates in each consumer and server modes.
The group has additionally created pretend video conferencing platforms, akin to RivaTalk, to lure victims into downloading malicious MSI installers. These platforms require entry codes to obtain software program, creating a further layer of legitimacy whereas hindering safety evaluation.
CVE-2025-26633 was formally disclosed as a zero-day vulnerability in March 2025, although associated assault samples had been noticed within the wild as early as February 2025. Microsoft has since launched safety patches, however the vulnerability continues to be actively exploited in opposition to unpatched techniques.
The vulnerability carries a CVSS rating of seven.0, indicating excessive severity, and has been added to the CISA Recognized Exploited Vulnerabilities catalog, underscoring its essential nature for federal companies and enterprise environments.
The marketing campaign highlights the persistent effectiveness of social engineering assaults mixed with technical exploitation. “Social engineering stays probably the most efficient instruments in a cybercriminal’s arsenal, and the rising risk group EncryptHub has hopped proper on the bandwagon,” famous Trustwave researchers.
Cybersecurity consultants suggest implementing multi-layered protection methods, together with rapid patching of CVE-2025-26633, enhanced monitoring of Microsoft Administration Console actions, and complete person consciousness coaching centered on social engineering techniques.
Organizations also needs to limit distant entry capabilities and implement strict verification procedures for IT help interactions.
The EncryptHub marketing campaign demonstrates how fashionable risk actors proceed to evolve their techniques, combining trusted communication platforms like Microsoft Groups with refined technical exploits to attain their goals.
IoCs
Enhance your SOC and assist your crew shield what you are promoting with free top-notch risk intelligence: Request TI Lookup Premium Trial.