A classy new phishing marketing campaign concentrating on Gmail customers by way of a multi-layered assault that makes use of professional Microsoft Dynamics infrastructure to bypass safety measures and steal login credentials.
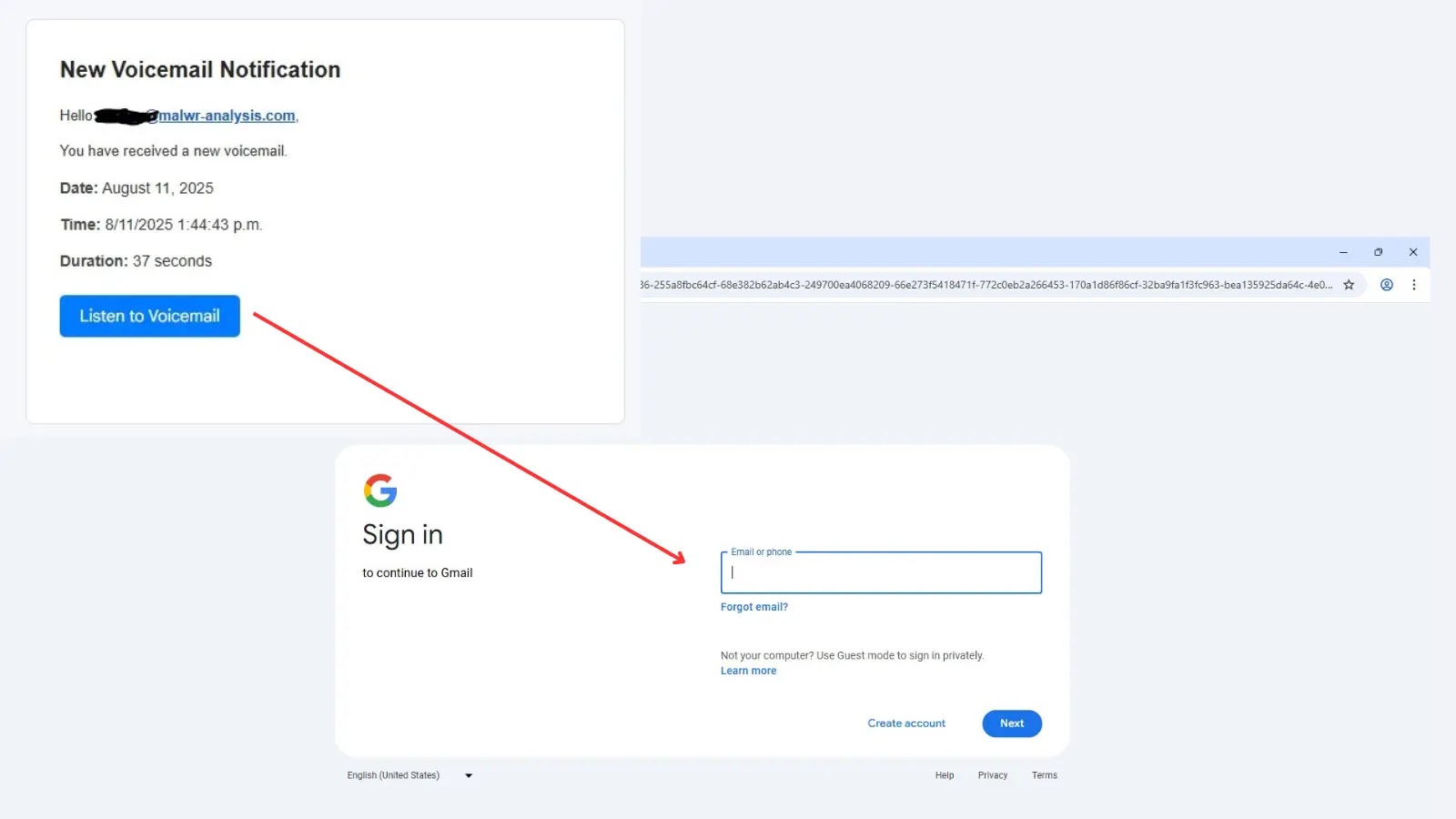
The assault begins with misleading “New Voice Notification” emails that seem to return from professional voicemail companies. These emails include spoofed sender data and have distinguished “Take heed to Voicemail” buttons that redirect victims by way of a fancy chain of compromised web sites.
Voice mail Phishing
The phishing operation employs a very intelligent preliminary vector, utilizing Microsoft’s professional Dynamics advertising and marketing platform (assets-eur.mkt.dynamics.com) to host the primary stage of the assault.
This system offers instant credibility and helps evade e-mail safety filters that sometimes flag suspicious domains.
After clicking the malicious hyperlink, victims are redirected to a CAPTCHA web page hosted on horkyrown[.]com, a website registered in Pakistan.
The CAPTCHA serves as a trust-building mechanism, creating the phantasm of professional safety measures whereas truly being a part of the assault infrastructure.
The ultimate stage presents customers with a pixel-perfect duplicate of Gmail’s login web page, full with Google branding and authentic-looking interface parts.
The pretend login kind captures each main credentials and superior safety measures, together with two-factor authentication codes, backup codes, and safety questions.
Superior Evasion Strategies
Safety analyst Anurag noticed that the malicious JavaScript powering the pretend login web page employs refined obfuscation strategies.
The code makes use of AES encryption to cover its true performance and consists of anti-debugging options that redirect customers to professional Google login pages when developer instruments are opened.
Pretend Login Web page
The assault additionally leverages a number of redirection layers and cross-site requests to servers in Russia (purpxqha[.]ru), indicating a fancy worldwide infrastructure designed to evade detection and complicate forensic evaluation.
As soon as victims enter their data, the malicious script systematically captures and exfiltrates all entered knowledge by way of encrypted channels. The system is designed to deal with numerous Gmail safety features, together with:
Main e-mail and password mixtures
SMS and voice name verification codes
Google Authenticator tokens
Backup restoration codes
Various e-mail addresses
Safety query responses
The stolen credentials are instantly transmitted to attacker-controlled servers, permitting for fast account compromise earlier than victims understand they’ve been focused.
This marketing campaign represents a big evolution in phishing strategies, combining social engineering with professional infrastructure abuse and superior technical evasion strategies.
The usage of Microsoft’s Dynamics platform significantly demonstrates how attackers are leveraging trusted companies to boost their credibility.
Gmail customers ought to stay vigilant for unsolicited voicemail notifications and confirm the authenticity of login requests by way of official channels.
Organizations ought to implement further e-mail safety measures and educate customers about these evolving risk vectors.
The area horkyrown[.]com has been recognized as the first assault infrastructure, registered by way of Onamae[.]com with publicly seen registrant data linking to Karachi, Pakistan.
Safety groups are suggested to dam this area and monitor for related campaigns utilizing professional advertising and marketing platforms as preliminary compromise vectors.
Customers who imagine they could have been focused ought to instantly change their Google account passwords and evaluation current account exercise.
Increase your SOC and assist your staff shield your online business with free top-notch risk intelligence: Request TI Lookup Premium Trial.