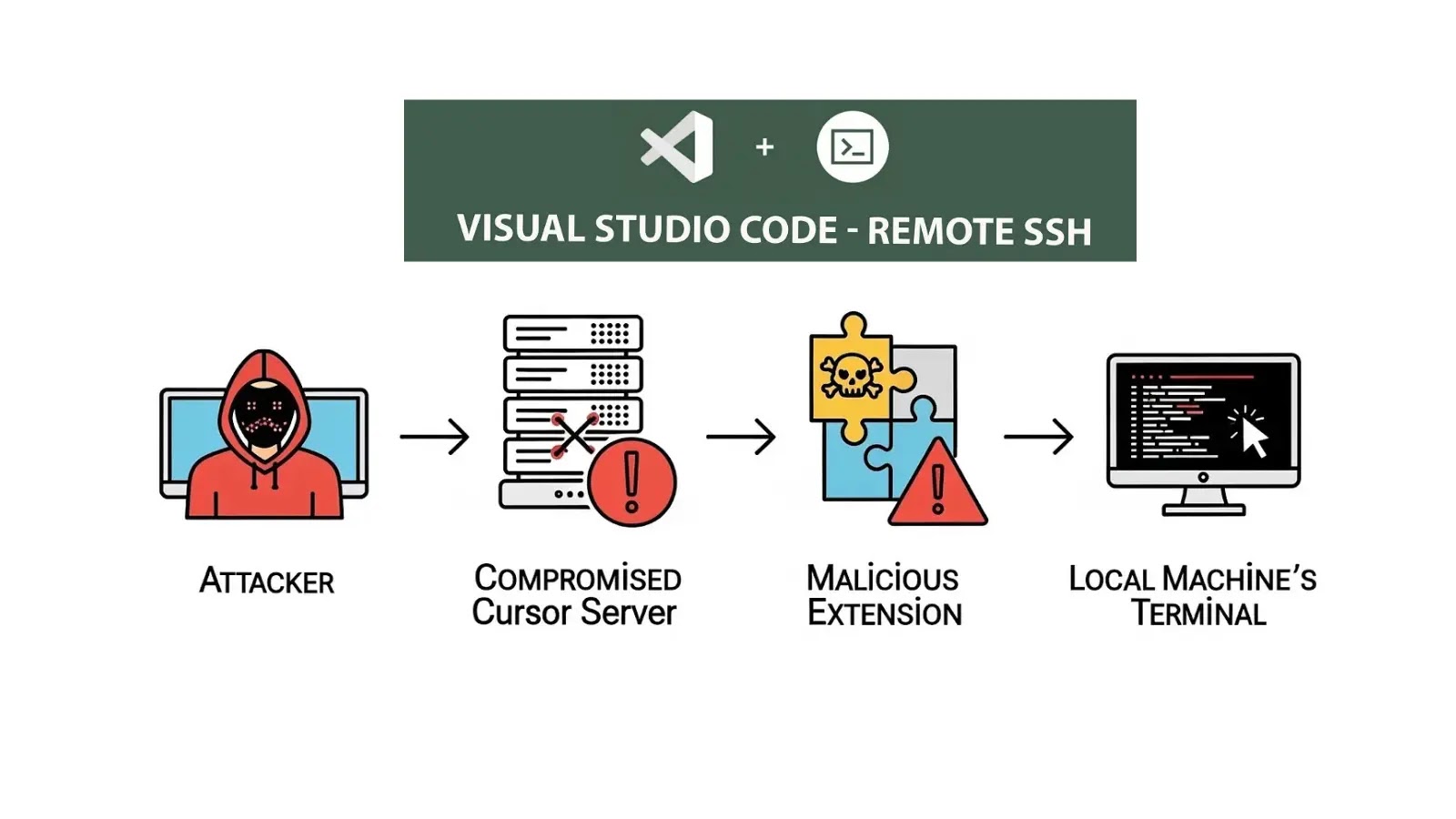
A important safety vulnerability has been found in Microsoft’s VS Code Distant-SSH extension that permits attackers to execute malicious code on builders’ native machines via compromised distant servers.
Safety researchers have demonstrated how this assault, dubbed “Vibe Hacking,” exploits the inherent belief relationship between distant improvement environments and native machines, affecting each VS Code and well-liked forks like Cursor.
The vulnerability stems from a harmful false impression amongst builders who consider distant improvement environments present full isolation.
Key Takeaways1. VS Code Distant-SSH extension permits attackers to execute malicious code on builders’ native machines.2. Attackers use built-in instructions to open native terminals and mechanically run arbitrary code.3. Exposing their workstations to compromise when connecting to untrusted servers.
Nevertheless, as soon as a server is compromised, attackers can simply pivot to the developer’s native machine via the Distant-SSH extension’s built-in performance.
Exploiting Constructed-in Instructions
Calif reviews that the assault leverages two particular VS Code instructions that function throughout the default configuration settings.
Malicious extensions on compromised servers can execute the workbench.motion.terminal.newLocal command to open a terminal instantly on the developer’s native machine, bypassing the distant setting totally.
Assault Chain
As soon as the native terminal is established, attackers deploy the workbench.motion.terminal.sendSequence command to ship arbitrary textual content sequences to the terminal.
By appending a newline character, the malicious code executes mechanically as if the developer pressed Enter. This method successfully transforms the trusted improvement setting right into a command and management channel, reads the report.
The assault works seamlessly as a result of the Distant-SSH extension inherently trusts communications from the distant server.
When builders hook up with what they consider is an remoted sandbox setting, they unknowingly expose their native machines to potential compromise.
Mitigation Methods
Microsoft has acknowledged these dangers on the Distant-SSH extension market web page, warning that “a compromised distant might use the VS Code Distant connection to execute code in your native machine”.
Nevertheless, this warning has not prevented widespread adoption of distant improvement practices, notably for AI agent deployment and testing.
Safety researchers counsel implementing consumer approval mechanisms when distant extensions try and open native terminals or ship keystrokes to energetic terminals.
Monitoring the ~/.cursor-server listing for unauthorized modifications can present restricted safety, although this method provides minimal safety if servers are absolutely compromised.
The vulnerability highlights the necessity for secure-by-default designs in improvement instruments that don’t depend on customers making advanced belief selections.
As distant improvement continues rising in reputation, addressing these basic safety points turns into more and more important for shielding developer workstations from refined provide chain assaults.
Safely detonate suspicious recordsdata to uncover threats, enrich your investigations, and minimize incident response time. Begin with an ANYRUN sandbox trial →