DragonForce represents a complicated and quickly evolving ransomware operation that has emerged as a major risk within the cybersecurity panorama since late 2023.
Working below a Ransomware-as-a-Service (RaaS) mannequin, this group has demonstrated distinctive adaptability by leveraging leaked ransomware builders from infamous households like LockBit 3.0 and Conti to create personalized assault variants.
The group has efficiently focused high-profile victims throughout a number of sectors, together with authorities entities, retail giants, and demanding infrastructure, with notable assaults towards the Ohio Lottery, Palau authorities, and main UK retailers like Marks & Spencer.
Their operations mix superior technical capabilities with skilled enterprise practices, providing associates as much as 80% of ransom funds whereas offering complete assault infrastructure and help providers.
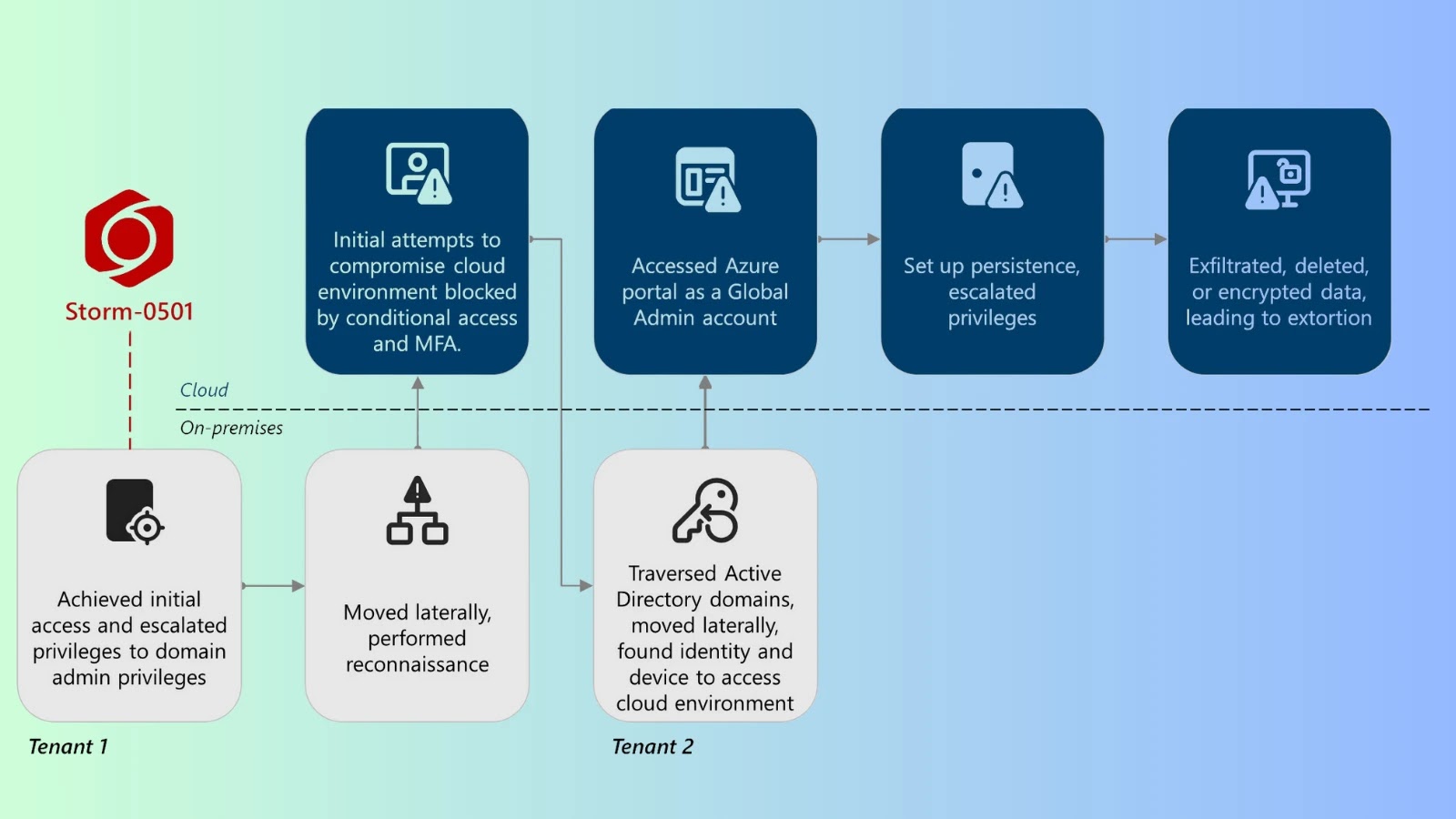
Ransomware assault movement. (Supply: cybersecuritynews.com)
Introduction to DragonForce Ransomware
DragonForce first appeared in December 2023 with the launch of their “DragonLeaks” darkish internet portal, shortly establishing themselves as a formidable participant within the ransomware ecosystem.
The group’s origins hint again to attainable connections with DragonForce Malaysia, a hacktivist collective, although the present operation has developed right into a purely profit-driven enterprise.
By 2025, DragonForce has matured into a complicated RaaS platform that draws each displaced associates from dismantled ransomware operations and freelance risk actors searching for strong infrastructure.
The group operates two distinct ransomware variants primarily based on leaked supply code from established households. Their preliminary variant utilized the leaked LockBit 3.0 (Black) builder, permitting them to quickly deploy efficient ransomware with out creating advanced encryption mechanisms from scratch.
In July 2024, DragonForce launched a second variant primarily based on the Conti V3 codebase, offering associates with enhanced customization capabilities. This dual-variant strategy demonstrates the group’s technical sophistication and dedication to offering associates with various assault choices.
The group’s enterprise mannequin displays fashionable cybercrime traits, providing a complete platform that features assault administration instruments, automated options, and customizable builders.
Associates can tailor ransomware samples by disabling focused security measures, configuring encryption parameters, and personalizing ransom notes.
In early 2025, DragonForce expanded its choices by introducing a white-label ransomware service, enabling associates to rebrand payloads below different names for added charges.
Assault Vectors and Preliminary Entry Methods
DragonForce employs a number of subtle vectors to realize preliminary entry to focus on networks, demonstrating the group’s understanding of various organizational vulnerabilities.
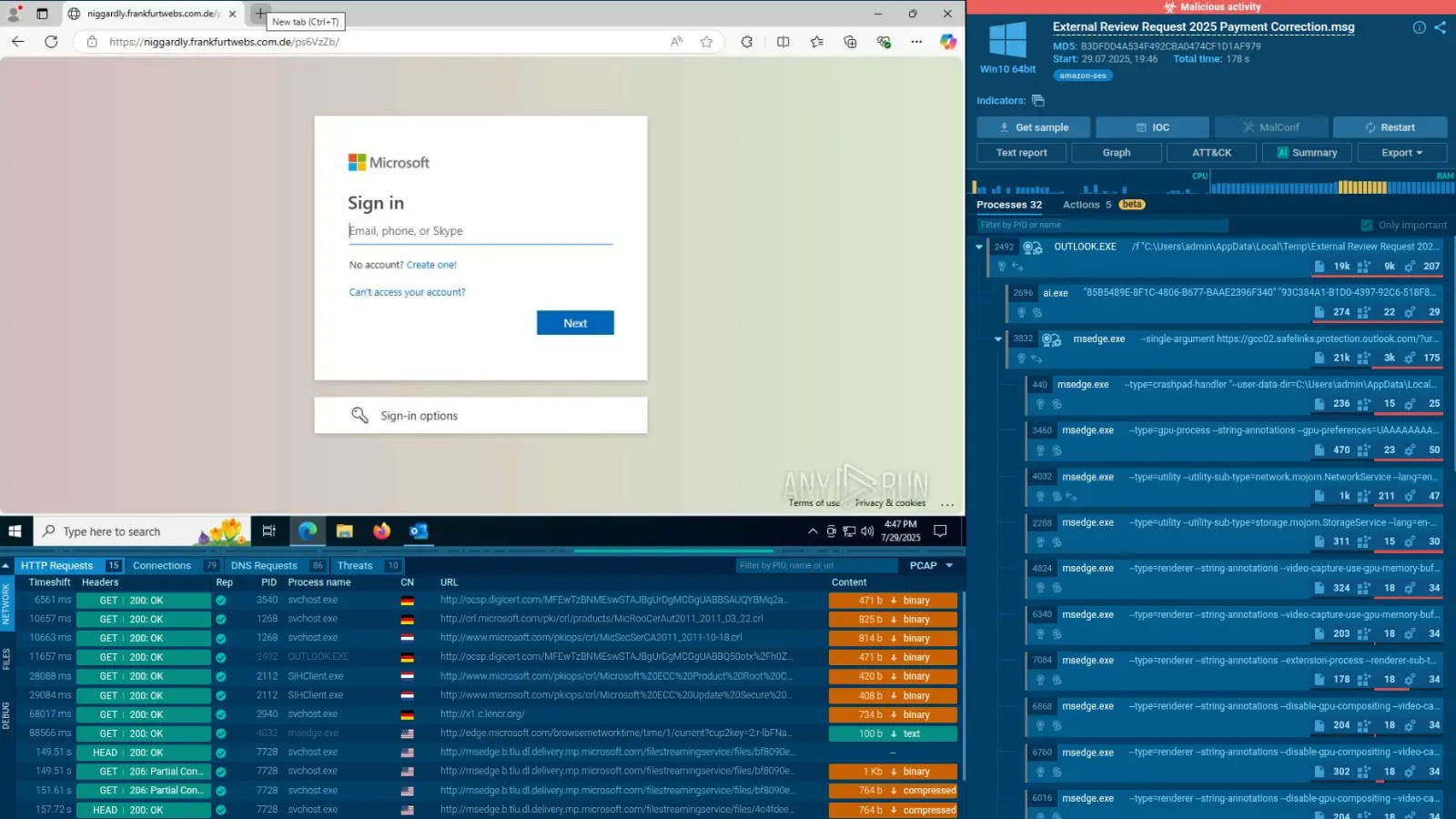
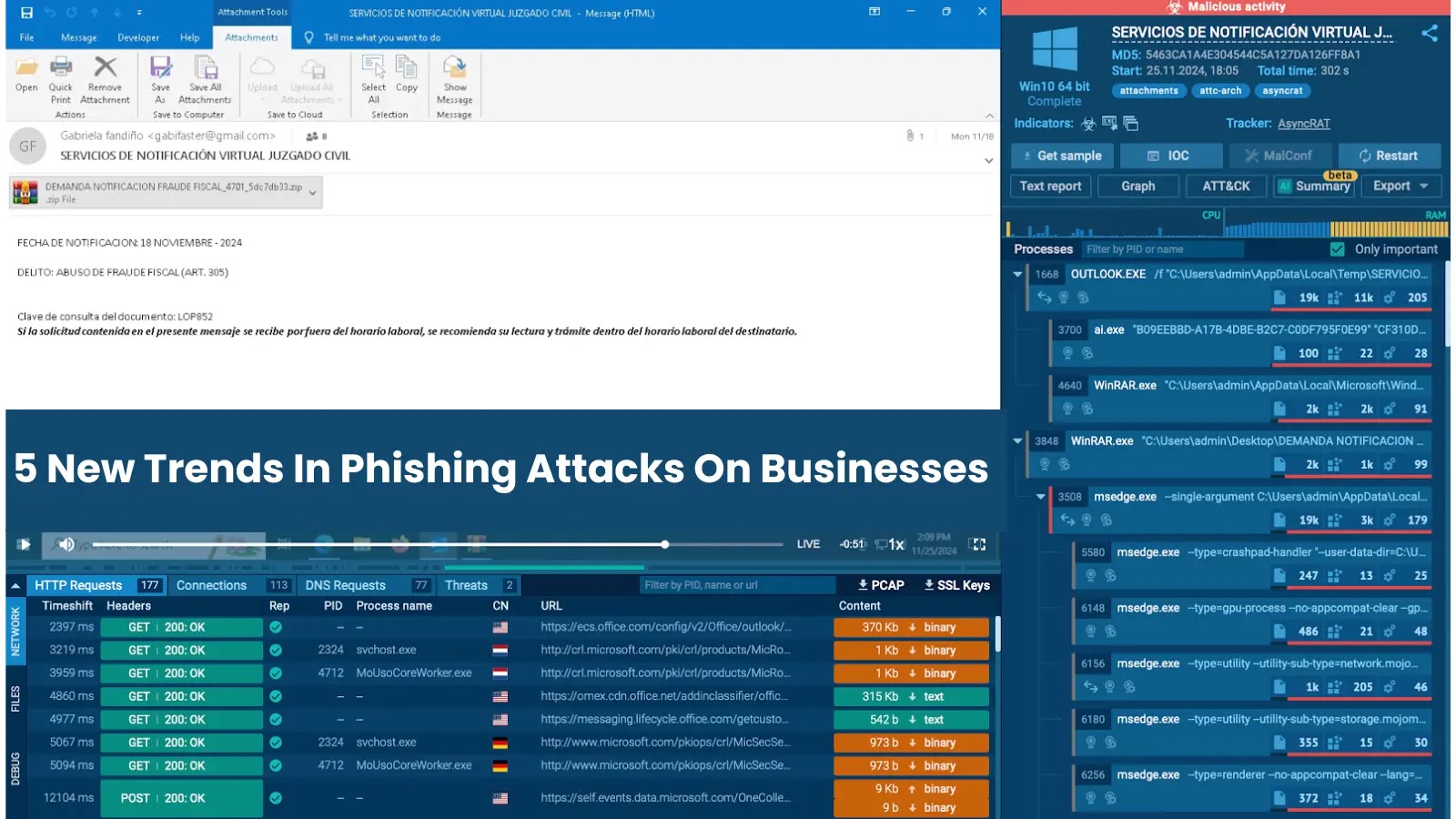
Phishing campaigns stay a major assault vector, with operators crafting convincing spear-phishing emails containing malicious attachments or hyperlinks that deploy ransomware payloads when executed by unsuspecting customers.
These campaigns typically goal particular people inside organizations utilizing social engineering strategies to extend success charges.
Exploitation of recognized vulnerabilities represents one other important assault vector, with DragonForce operators actively concentrating on unpatched programs.
The group has particularly been related to exploiting a number of high-impact vulnerabilities, together with CVE-2021-44228 (Log4Shell), CVE-2023-46805 (Ivanti Join Safe Authentication Bypass), CVE-2024-21412 (Microsoft Home windows SmartScreen Bypass), CVE-2024-21887 (Ivanti Join Safe Command Injection), and CVE-2024-21893 (Ivanti Join Safe Path Traversal).
DragonForce associates systematically goal organizations with poorly secured distant entry infrastructure, leveraging stolen or weak credentials to determine a persistent community presence.
The group additionally exploits trusted relationships, as demonstrated in a latest incident the place attackers gained entry via distant administration software program put in by a earlier internet hosting firm that was by no means correctly eliminated.
In some instances, DragonForce operators have gained preliminary entry by exploiting compromised managed service supplier (MSP) relationships, permitting them to maneuver laterally throughout a number of consumer environments via trusted connections.
This method amplifies the affect of particular person breaches by offering entry to quite a few organizations via a single compromise level.
Distant Desktop Protocol (RDP) and VPN assaults represent important preliminary entry strategies, with operators conducting credential stuffing assaults and brute-force operations towards uncovered providers.
Cyber Kill Chain. (Supply: cybersecuritynews.com)
Ways, Methods, and Procedures (TTPs)
DragonForce’s operational methodology follows the MITRE ATT&CK framework throughout a number of techniques, demonstrating a complicated understanding of enterprise community compromise strategies.
Preliminary AccessT1190Exploit Public-Dealing with ApplicationExploits CVE-2021-44228 (Log4Shell), CVE-2023-46805, CVE-2024-21412, CVE-2024-21887, CVE-2024-21893HighMediumInitial AccessT1078Valid AccountsUses stolen/weak RDP and VPN credentials, brute power assaults on distant entry servicesHighLowInitial AccessT1566.001Spearphishing AttachmentDeploys ransomware via malicious e-mail attachments concentrating on particular individualsHighMediumInitial AccessT1566.003Spearphishing by way of ServiceConducts vishing (voice phishing) campaigns alongside e-mail phishingMediumHighInitial AccessT1199Trusted RelationshipExploits compromised MSP relationships and former internet hosting firm accessMediumHighExecutionT1204.002Malicious FileSocial engineering customers to execute ransomware payloads, strikes information to System32HighLowExecutionT1059.001PowerShellUses PowerShell for command execution, payload deployment, and system reconnaissanceHighMediumExecutionT1053.005Scheduled Job/JobCreates scheduled duties for persistence and automatic executionMediumLowPersistenceT1574.011Services File Permissions WeaknessInstalls AnyDesk distant entry instrument for persistent backdoor accessHighMediumPersistenceT1053.005Scheduled Job/JobEstablishes scheduled duties to take care of persistence throughout rebootsMediumLowPersistenceT1547.001Registry Run Keys / Startup FolderModifies registry Run keys to make sure malware execution at startupMediumLowPrivilege EscalationT1134Access Token ManipulationDuplicates SYSTEM-level entry tokens utilizing DuplicateTokenEx() APIHighHighPrivilege EscalationT1068Exploitation for Privilege EscalationLeverages recognized vulnerabilities for escalation to administrator privilegesMediumMediumDefense EvasionT1027Obfuscated Recordsdata or InformationEmbeds Chinese language textual content signatures, makes use of code obfuscation techniquesHighHigh
Indicators of Compromise (IoCs)
Safety groups ought to monitor for particular indicators related to DragonForce campaigns to allow early detection and response.
Community indicators embody command and management server IP addresses: 2[.]147[.]68[.]96, 185[.]59[.]221[.]75, and 69[.]4[.]234[.]20. Notably, early marketing campaign infrastructure was recognized in Iran, suggesting worldwide collaboration or infrastructure rental.
IoC TypeIndicatorDescriptionThreat LevelDetection MethodIP Tackle (C&C)2.147.68.96Command and Management serverHighNetwork monitoring, firewall logsIP Tackle (C&C)185.59.221.75Command and Management serverHighNetwork monitoring, firewall logsIP Tackle (C&C)69.4.234.20Command and Management serverHighNetwork monitoring, firewall logsFile Hash (SHA256)b9bba02d18bacc4bc8d9e4f70657d381568075590cc9d0e7590327d854224b32DragonForce ransomware executable hashCriticalFile integrity monitoring, antivirusFile Hash (SHA256)ba1be94550898eedb10eb73cb5383a2d1050e96ec4df8e0bf680d3e76a9e2429DragonForce payload hashCriticalFile integrity monitoring, antivirusFile Hash (SHA256)d626eb0565fac677fdc13fb0555967dc31e600c74fbbd110b744f8e3a59dd3f9DragonForce variant hashCriticalFile integrity monitoring, antivirusFile PathC:UsersPublicDocumentsWinupdate.exeExfiltration instrument locationHighFile system monitoring, EDRFile PathC:WindowsSystem32Winupdate.exeAlternative exfiltration instrument pathHighFile system monitoring, EDRFile PathC:UsersPubliclog.logSystem data log fileMediumFile system monitoringFile PathC:WindowsSystem32Common payload deployment directoryMediumDirectory monitoringFilenameWinupdate.exeData exfiltration utility (GoLang)HighProcess monitoring, EDRFilenameFileSeek.exeFile discovery reconnaissance toolMediumProcess monitoringFilenameREADME.txtRansom word filenameLowFile system monitoringFilenameSystemBCSOCKS5 backdoor for persistenceHighNetwork monitoring, course of monitoringFile Extension.dragonforce_encryptedEncrypted file extensionMediumFile system monitoringDomain (.onion)z3wqggtxft7id3ibr7srivv5gjof5fwg76slewnzwwakjuf3nlhukdid.onionDragonLeaks leak siteHighNetwork monitoring, DNS logsDomain (.onion)3pktcrcbmssvrnwe5skburdwe2h3v6ibdnn5kbjqihsg6eu6s6b7ryqd.onionAlternative leak website domainHighNetwork monitoring, DNS logs
The Marks & Spencer incident in April 2025 brought on estimated losses of £300 million and months-long operational disruption, with attackers sending direct emails to the CEO demanding ransom funds.
These instances illustrate DragonForce’s functionality to focus on each authorities infrastructure and personal sector organizations with devastating effectiveness, emphasizing the important want for complete cybersecurity measures and incident response planning.
Discover this Story Attention-grabbing! Comply with us on LinkedIn and X to Get Extra Instantaneous Updates.