Aug 21, 2025Ravie LakshmananVulnerability / Software program Safety
Commvault has launched updates to handle 4 safety gaps that may very well be exploited to attain distant code execution on inclined cases.
The listing of vulnerabilities, recognized in Commvault variations earlier than 11.36.60, is as follows –
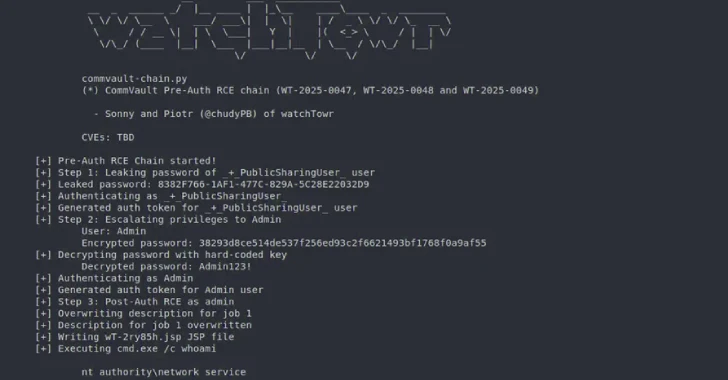
CVE-2025-57788 (CVSS rating: 6.9) – A vulnerability in a recognized login mechanism permits unauthenticated attackers to execute API calls with out requiring consumer credentials
CVE-2025-57789 (CVSS rating: 5.3) – A vulnerability through the setup part between set up and the primary administrator login that enables distant attackers to use the default credentials to achieve admin management
CVE-2025-57790 (CVSS rating: 8.7) – A path traversal vulnerability that enables distant attackers to carry out unauthorized file system entry via a path traversal challenge, leading to distant code execution
CVE-2025-57791 (CVSS rating: 6.9) – A vulnerability that enables distant attackers to inject or manipulate command-line arguments handed to inner parts as a result of inadequate enter validation, leading to a sound consumer session for a low-privilege position
watchTowr Labs researchers Sonny Macdonald and Piotr Bazydlo have been credited with discovering and reporting the 4 safety defects in April 2025. All of the flagged vulnerabilities have been resolved in variations 11.32.102 and 11.36.60. Commvault SaaS resolution just isn’t affected.
In an evaluation revealed Wednesday, the cybersecurity firm mentioned risk actors may trend these vulnerabilities into two pre-authenticated exploit chains to attain code execution on inclined cases: One that mixes CVE-2025-57791 and CVE-2025-57790, and the opposite that strings CVE-2025-57788, CVE-2025-57789, and CVE-2025-57790.
It is price noting that the second pre-auth distant code execution chain turns into profitable provided that the built-in admin password hasn’t been modified since set up.
The disclosure comes practically 4 months after watchTowr Labs reported a essential Commvault Command Middle flaw (CVE-2025-34028, CVSS rating: 10.0) that would enable arbitrary code execution on affected installations.
A month later, the U.S. Cybersecurity and Infrastructure Safety Company (CISA) added the vulnerability to its Identified Exploited Vulnerabilities (KEV) catalog, citing proof of lively exploitation within the wild.