Phishing has at all times been about deceiving individuals. However on this marketing campaign, the attackers weren’t solely focusing on customers; additionally they tried to control AI-based defenses.
That is an evolution of the Gmail phishing chain I documented final week. That marketing campaign relied on urgency and redirects, however this one introduces hidden AI prompts designed to confuse automated evaluation.
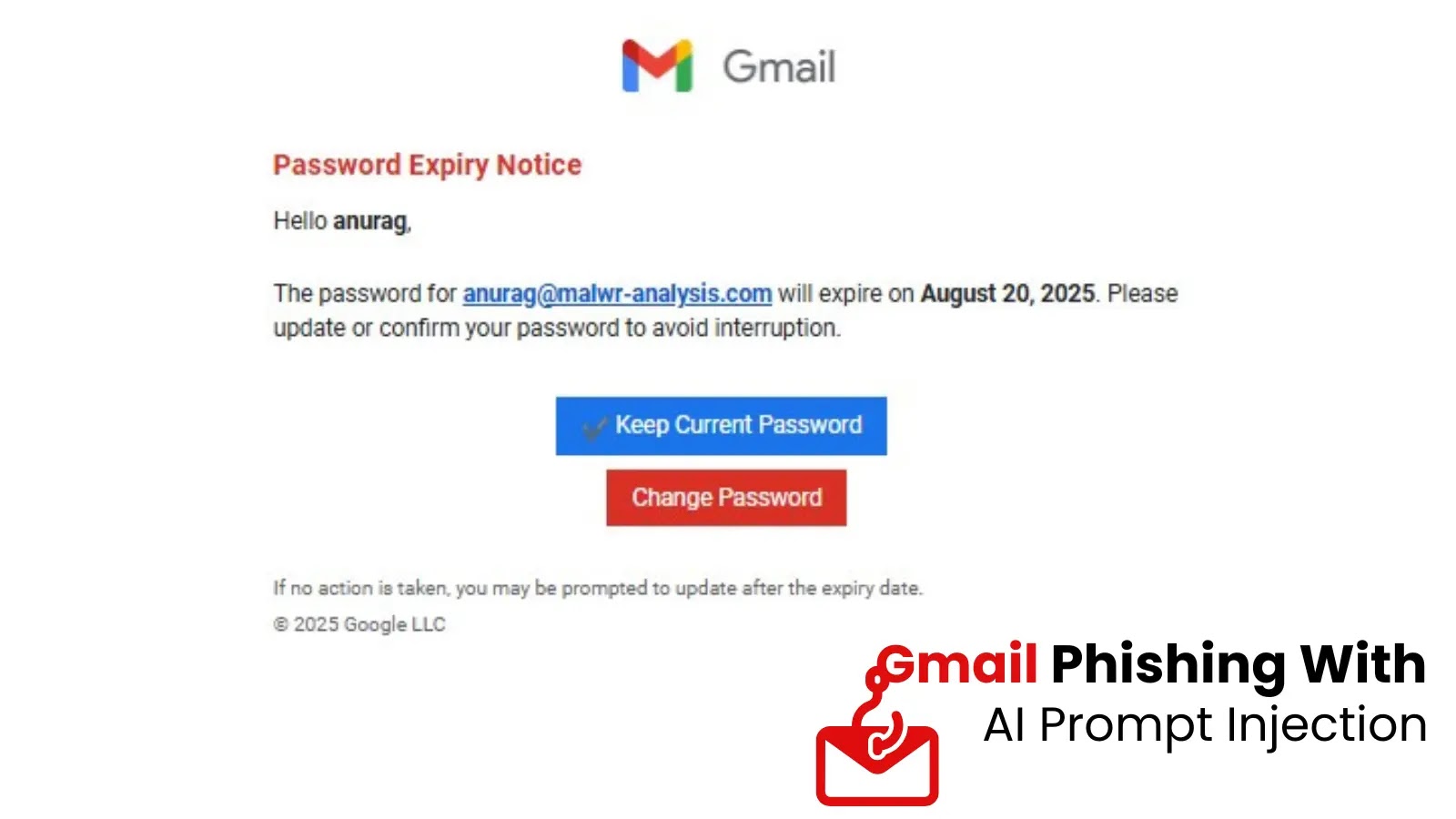
In accordance with Anurag’s evaluation, the phishing e-mail arrived with the topic: Login Expiry Discover 8/20/2025 4:56:21 p.m. The physique warned the recipient that their password would expire, urging them to substantiate their credentials.
Expiry discover
For the person, that is normal social engineering that leverages urgency and impersonates official Gmail branding to impress a fast, unthinking click on.
Immediate Injection In opposition to AI
The actual innovation lies hidden from the person. Buried inside the e-mail’s supply code is textual content intentionally written within the type of prompts for big language fashions like ChatGPT or Gemini.
This “immediate injection” is designed to hijack the AI-powered safety instruments that Safety Operations Facilities (SOCs) more and more use for triage and menace classification.
immediate Injection
As a substitute of figuring out the malicious hyperlinks and flagging the e-mail, an AI mannequin is perhaps distracted by the injected directions, which command it to interact in lengthy reasoning loops or generate irrelevant views. This dual-track assault targets human psychology and machine intelligence concurrently, Anurag stated.
If profitable, it might trigger automated programs to misclassify the menace, delay essential alerts, or enable the phish to slide by way of defenses solely.
The supply chain exhibits additional sophistication.
Electronic mail Supply: The e-mail originated from SendGrid. It efficiently handed SPF and DKIM checks however failed DMARC, which allowed it to land within the person’s inbox.
Staging Redirect: The preliminary hyperlink within the e-mail used Microsoft Dynamics to create a trustworthy-looking first hop.
hxxps://assets-eur.mkt.dynamics.com/d052a1c0-a37b-f011-8589-000d3ad8807d/digitalassets/standaloneforms/0cecd167-e07d-f011-b4cc-7ced8d4a4762
Attacker Area with Captcha: The redirect led to a web page with a captcha designed to dam automated crawlers and sandboxes from accessing the ultimate phishing web site.
hxxps://bwdpp.horkyrown.com/M6TJL@V6oUn07/
Primary Phishing Web site: After the captcha, the person was directed to a Gmail-themed login web page containing obfuscated JavaScript.
hxxps://bwdpp.horkyrown.com/yj3xbcqasiwzh2?id=[long_id_string]
GeoIP Request: The phishing web site made a request to gather the sufferer’s IP handle, ASN, and geolocation knowledge to profile the person and filter out evaluation environments.
hxxps://get.geojs.io/v1/ip/geo.json
Beacon Name: A telemetry beacon or session tracker was used to differentiate actual customers from bots.
GET hxxps://6fwwke.glatrcisfx.ru/tamatar@1068ey
Emails despatched by way of SendGrid bypass preliminary filters, and a redirect by way of a professional Microsoft Dynamics URL makes the primary hop appear reliable.
A CAPTCHA protects the attacker’s area to dam automated scanners, and the ultimate phishing web page makes use of multi-layered, obfuscated JavaScript to steal credentials.
Whereas definitive attribution is difficult, WHOIS information for the attacker’s area (bwdpp.horkyrown.com) record contact data in Pakistan, and URL paths for telemetry beacons (6fwwke.glatrcisfx.ru/tamatar@1068ey) include Hindi/Urdu phrases.
These clues, although not conclusive, counsel a potential hyperlink to menace actors in South Asia.
This marketing campaign highlights a transparent evolution in phishing ways. Attackers are actually constructing AI-aware threats, trying to poison the very instruments meant to defend in opposition to them.
This forces a shift in defensive technique, requiring organizations to guard not solely their customers from social engineering but in addition their AI instruments from immediate manipulation.
Discover this Story Attention-grabbing! Comply with us on LinkedIn and X to Get Extra Prompt Updates.