When each minute counts, it’s necessary to have entry to recent menace intelligence on the tip of your finger. That’s what all high-performing SOC groups have in frequent. Study the place to get related menace knowledge free of charge and the right way to triage incidents in seconds utilizing it.
Getting & Making use of Free Risk Intelligence
Enriching your indicators with menace intelligence is a course of that shouldn’t be missed. It equips SOCs with knowledge and instruments for the achievement of key targets of safety groups, similar to:
Acceleration of alert triage
Detection fee development
Discount of alert fatigue
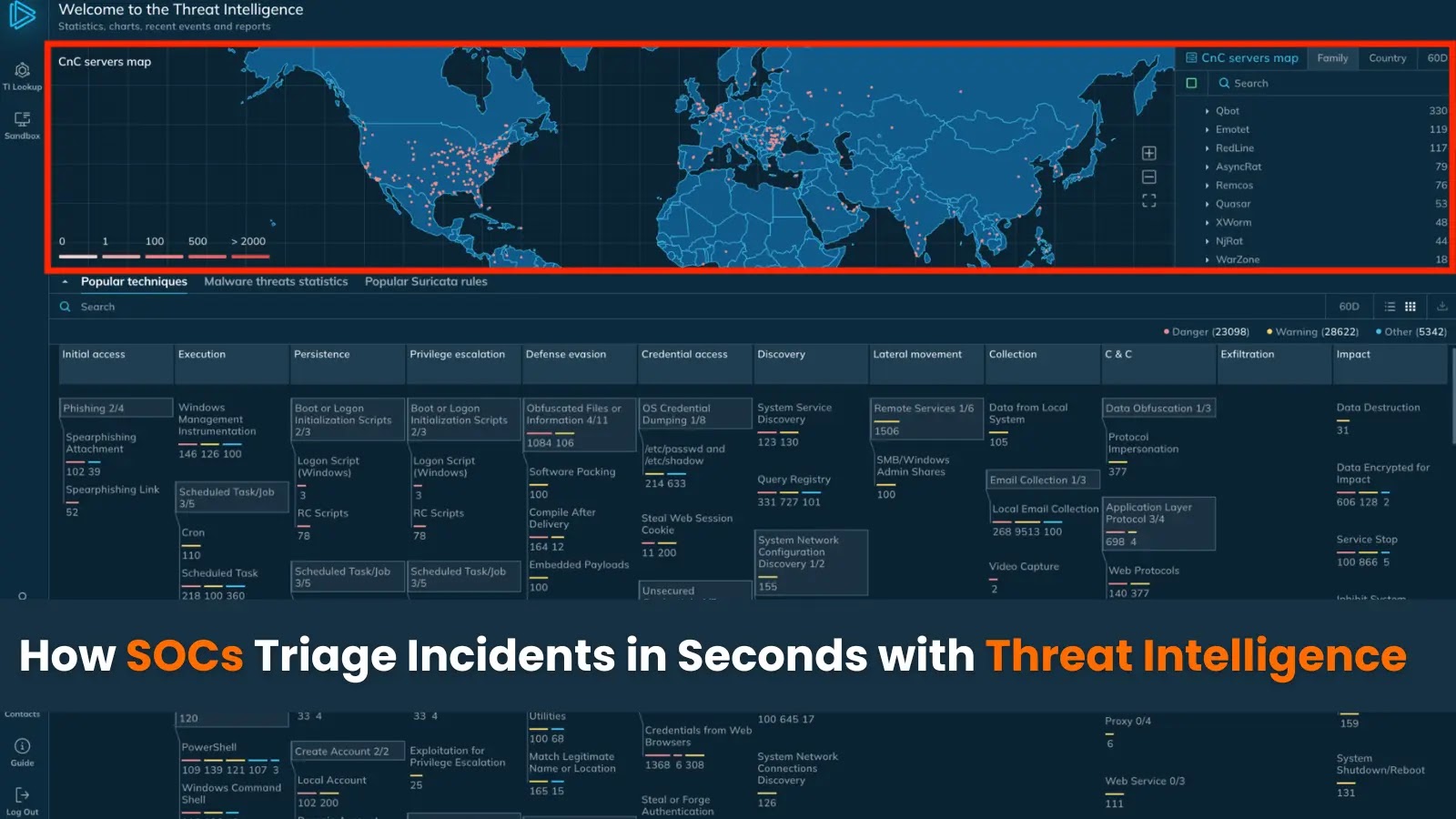
Step one to soak up this route is to discover a dependable supply of knowledge on assaults, which could be shortly and effortlessly accessed throughout triage. For that, you’ll be able to strive Risk Intelligence Lookup, a searchable database of menace intel.
Foremost web page of ANY.RUN’s TI Lookup
By accumulating knowledge from public malware investigations carried out by over 15,000 SOC groups and 500,000 particular person researchers, it makes precious indicators and their context obtainable to you.
Because of this in a single easy question, you’ll be able to faucet into thousands and thousands of malware analyses to determine and enrich your indicators, in addition to discover new ones for updates of proactive protection methods. As an illustration, throughout alert triage, you’ll be able to confirm a suspicious area with a TI Lookup question like this:
domainName:”technologyenterdo.store”
TI Lookup’s conclusion on the question and record of analyses for additional investigation
Virtually immediately you’ll be given the reply: the indicator is malicious. Extra information could be present in ANY.RUN Sandbox. That’s the place TI Lookup’s knowledge comes from, so every indicator you will discover there may be tied with a corresponding evaluation session.
For proactive investigation of present threats in your location, strive a compound search like this to gather IOCs and replace detection guidelines upfront:
threatName:”tycoon” AND submissionCountry:”de”
Search outcomes for Tycoon threats submitted in Germany
It consists of the identify of the menace (Tycoon) and the brief identify of the nation it was detected in (de—Germany). Moments after you enter it, TI Lookup will return the overview of becoming threats and as much as 20 current evaluation periods carried out in ANY.RUN’s Interactive Sandbox. Use this information for proactive detection of potential threats and renewal of detection methods.
TI Lookup shares hyperlinks to related ANY.RUN sandbox periods like this one
Different use instances of Risk Intelligence Lookup embrace checking not solely domains, but in addition IPs and file hashes, in addition to monitoring threats by TTPs through interactive MITRE ATT&CK matrix. By means of them, TI Lookup brings important enhancements to SOC efficiency charges:
Deeper and Sooner Risk Investigations: Uncover wealthy knowledge by linking artifacts to real-world assault patterns and reduce MTTR by understanding menace conduct and TTPs.
Stronger Proactive Protection: Monitor related threats and keep forward of them by making smarter detection guidelines in SIEM, IDS/IPS, and EDR.
Higher SOC Experience: Shut the information hole in your crew—analysts can examine malware and adversary TTPs inside the interactive sandbox and MITRE ATT&CK matrix.
Obtain quicker, data-fueled triage and response -> Enrich IOCs free of charge
Premium Entry to Risk Intel for Enterprises
The use instances described above can be found within the free model of TI Lookup. This may be sufficient to simplify and speed up your menace investigation. However in case you’re on the lookout for an enterprise-grade resolution with limitless performance, take into account attempting TI Lookup Premium.
It unlocks entry to additional question operators and over 40 parameters, all obtainable evaluation periods, non-public searches and YARA search. With these options, you’ll be able to create extra superior requests and see all menace knowledge there may be. The paid model of TI Lookup may also be built-in utilizing API and SDK for an automatic and easy workflow.
Automated, Actual-Time Detection: Correlate alerts towards in depth IOCs, IOBs, and IOAs, whereas integrating TI Lookup with SIEM, TIP, or SOAR platforms for steady monitoring.
Precision Looking & Investigation: Construct and search customized YARA guidelines in ANY.RUN’s database, and refine investigations with 40+ parameters and superior operators.
Proactive Risk Consciousness: Automate alerts for particular IOCs or behaviors, and leverage professional TI Stories to remain forward of evolving malware developments throughout industries.
Unlock Premium menace intelligence -> Attempt TI Lookup