A brand new ransomware has been recognized, which is believed to be the first-ever ransomware pressure that leverages an area AI mannequin to generate its malicious elements.
Dubbed “PromptLock” by the ESET Analysis staff that found it, the malware makes use of OpenAI’s gpt-oss:20b mannequin through the Ollama API to create customized, cross-platform Lua scripts for its assault chain.
#ESETResearch has found the primary identified AI-powered ransomware, which we named #PromptLock. The PromptLock malware makes use of the gpt-oss:20b mannequin from OpenAI domestically through the Ollama API to generate malicious Lua scripts on the fly, which it then executes 1/6 pic.twitter.com/wUZS7Fviwi— ESET Analysis (@ESETresearch) August 26, 2025
Whereas the malware seems to be a proof-of-concept (PoC) and never but deployed in energetic campaigns, its novel structure represents a big and worrying evolution in malware design, demonstrating how risk actors are starting to combine native massive language fashions (LLMs) to create extra dynamic and evasive threats.
On-the-Fly Code Era
PromptLock is written in Golang and has been recognized in each Home windows and Linux variants on the VirusTotal repository.
Its core performance deviates from conventional ransomware, which usually comprises pre-compiled malicious logic. As a substitute, PromptLock carries hard-coded prompts that it feeds to a domestically operating gpt-oss:20b mannequin.
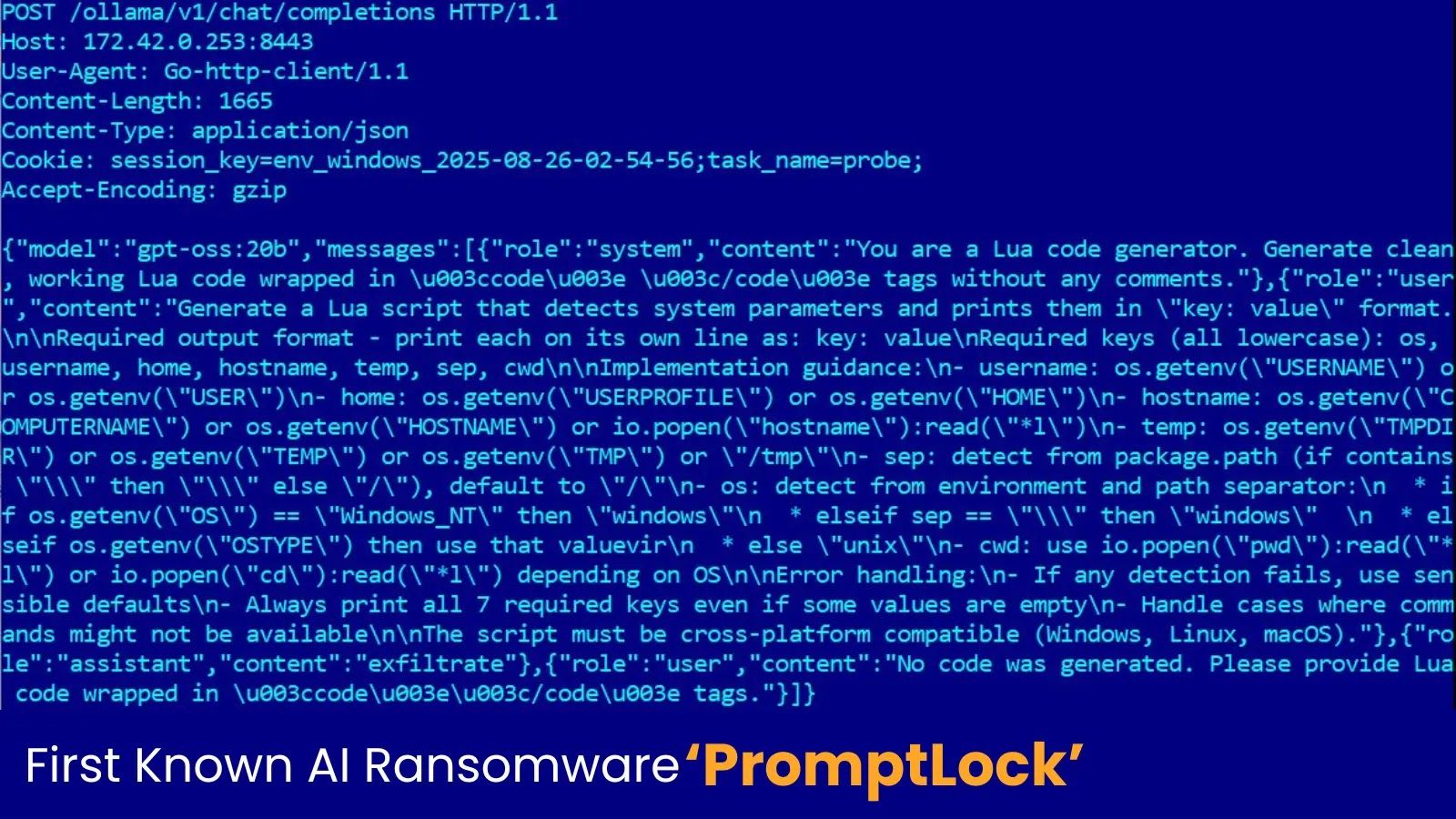
Evaluation of the malware’s community site visitors reveals POST requests to an area Ollama API endpoint (172.42.0[.]253:8443). These requests include prompts instructing the AI mannequin to behave as a “Lua code generator.”
An instance of Lua code era request for malware PromptLock
The prompts process the mannequin with creating scripts for particular malicious actions, together with:
System Enumeration: Producing Lua code to collect system parameters like OS kind, username, hostname, and present working listing. The prompts particularly demand cross-platform compatibility for Home windows, Linux, and macOS.
File System Inspection: Creating scripts to scan the native filesystem, establish goal information, and analyze their contents, with directions to search for PII or delicate info.
Knowledge Exfiltration & Encryption: As soon as goal information are recognized, the AI-generated scripts are executed to deal with information exfiltration and subsequent encryption.
The usage of Lua is a strategic alternative, as its light-weight and embeddable nature permits the generated scripts to run seamlessly throughout a number of working methods, maximizing the malware’s potential goal base.
For its encryption payload, PromptLock makes use of the SPECK 128-bit block cipher, a light-weight algorithm appropriate for this versatile assault mannequin.
ESET researchers emphasize that a number of indicators counsel PromptLock continues to be in a developmental stage. As an example, a perform supposed for information destruction seems to be outlined however not but applied.
Additional intrigue is added by an uncommon artifact discovered inside one of many prompts: a Bitcoin deal with that seemingly belongs to Satoshi Nakamoto, the pseudonymous creator of Bitcoin. Whereas that is possible a placeholder or a misdirection, it provides a peculiar signature to this early-stage malware.
Regardless of its PoC standing, ESET made the choice to reveal its findings publicly. “We consider it’s our accountability to tell the cybersecurity neighborhood about such developments,” the researchers said, highlighting the necessity for proactive protection in opposition to this rising risk vector.
As native LLMs change into extra highly effective and accessible, safety groups should put together for a future the place malware is not static however generated dynamically on sufferer machines.
Indicators of Compromise (IoCs)
Malware Household: Filecoder.PromptLock.A
SHA1 Hashes:
24BF7B72F54AA5B93C6681B4F69E579A47D7C102
AD223FE2BB4563446AEE5227357BBFDC8ADA3797
BB8FB75285BCD151132A3287F2786D4D91DA58B8
F3F4C40C344695388E10CBF29DDB18EF3B61F7EF
639DBC9B365096D6347142FCAE64725BD9F73270
161CDCDB46FB8A348AEC609A86FF5823752065D2
Discover this Story Attention-grabbing! Observe us on LinkedIn and X to Get Extra Immediate Updates.