Microsoft Risk Intelligence has launched an in depth report exposing a major evolution in ransomware assaults, pioneered by the financially motivated menace actor Storm-0501.
The group has shifted from conventional on-premises ransomware to a extra harmful, cloud-native technique that includes knowledge exfiltration and destruction, basically altering the character of ransomware threats for companies working in hybrid cloud environments.
Not like standard assaults that encrypt information on native servers and demand fee for a decryption key, Storm-0501’s new methodology is much extra devastating.
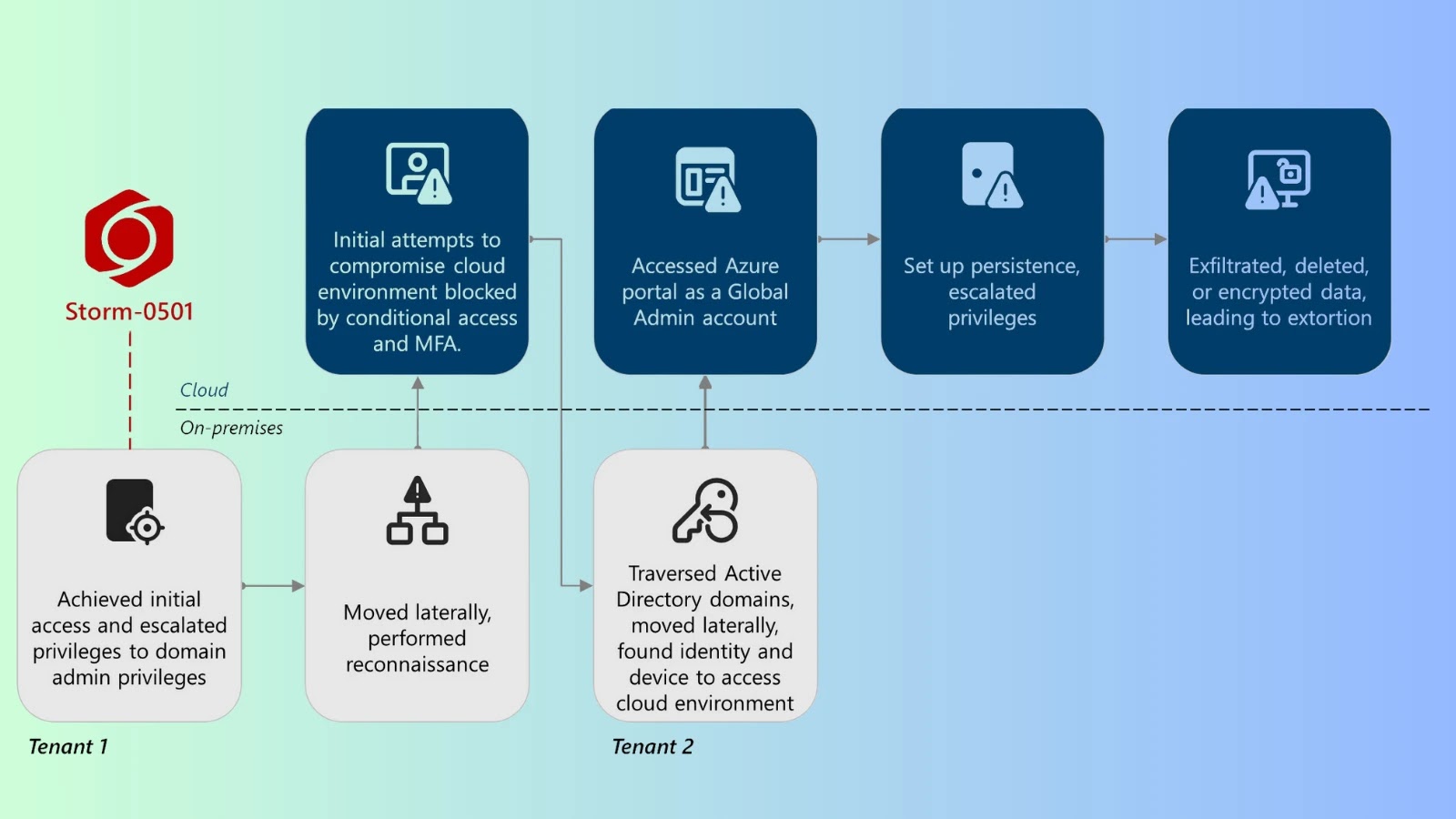
Overview of Storm-0501 cloud-based ransomware assault chain.
The group leverages cloud-native capabilities to first exfiltrate huge volumes of delicate knowledge, then systematically destroys the unique knowledge and any backups inside the sufferer’s cloud atmosphere earlier than demanding a ransom.
This “steal-and-destroy” tactic eliminates the potential of restoration from native backups and locations immense stress on sufferer organizations.
The assault chain, as detailed by Microsoft, is a classy mix of on-premises and cloud infiltration. It typically begins with a compromise of an organization’s native Lively Listing.
From this foothold, the attackers pivot to the cloud, focusing on Microsoft Entra ID (previously Azure AD). Their main goal is to discover a high-privilege account, equivalent to a World Administrator, that lacks sturdy safety, significantly multi-factor authentication (MFA).
In a current marketing campaign analyzed by Microsoft, Storm-0501 recognized a synced, non-human World Administrator account and not using a registered MFA methodology.
Storm-0501 Assault Chain
The attackers reset the account’s password on-premises, which then synchronized to the cloud. By taking up this account, they have been capable of enroll their very own MFA machine, bypassing present safety insurance policies and gaining full management over the cloud area.
With top-level administrative entry, the attackers elevate their privileges inside Azure to develop into an “Proprietor” of all of the group’s cloud subscriptions.
They then provoke a discovery section to map out important belongings, together with knowledge shops and backups. Following discovery, they exfiltrate the information utilizing cloud instruments like AzCopy.
The ultimate influence section is swift and catastrophic. Storm-0501 initiates a mass-deletion of Azure assets, together with storage accounts, digital machine snapshots, and restoration vaults.
For knowledge protected by useful resource locks or immutability insurance policies, the attackers first try and disable these protections. If unsuccessful, they resort to encrypting the remaining knowledge with a key they management after which deleting the important thing, rendering the knowledge completely inaccessible. The extortion demand is then sometimes delivered through Microsoft Groups utilizing a compromised account.
To fight these threats, Microsoft is urging organizations to undertake a multi-layered protection technique. Key suggestions embrace imposing phishing-resistant MFA for all customers, training the precept of least privilege, and guaranteeing privileged accounts are cloud-native and secured.
Microsoft additionally highlights the significance of utilizing built-in cloud security measures like Microsoft Defender for Cloud, making use of useful resource locks to important belongings, and enabling immutability and soft-delete insurance policies on storage and key vaults to forestall irreversible knowledge loss.
Storm-0501, beforehand identified for assaults on U.S. faculty districts and the healthcare sector, continues to show its proficiency in navigating complicated hybrid environments, underscoring the pressing want for companies to adapt their safety posture for the cloud period.
Discover this Story Attention-grabbing! Comply with us on LinkedIn and X to Get Extra Instantaneous Updates.