A complicated phishing marketing campaign has been recognized, the place menace actors impersonate IT helpdesk personnel by way of Groups’ exterior communication options, exploiting the platform’s default configuration to bypass conventional electronic mail safety measures and acquire unauthorized screen-sharing and remote-control capabilities.
The assaults leverage Groups’ exterior collaboration options, that are enabled by default in Microsoft 365 tenants, permitting attackers to provoke contact with organizational customers with out prior authentication.
Key Takeaways1. Default Groups settings allow direct IT helpdesk impersonation assaults, bypassing electronic mail safety.2. Voice calls keep away from safety warnings, resulting in display screen sharing and distant entry.3. Monitor ChatCreated/MessageSent logs for exterior .onmicrosoft.com domains.
This basic design alternative has created an unprecedented assault floor that mixes social engineering with reputable platform performance to devastating impact.
Voice Name Phishing and Distant Management
In keeping with Axon Group reviews, Cybercriminals have developed a number of subtle assault vectors inside the Microsoft Groups ecosystem, every exploiting completely different points of the platform’s communication capabilities.
The first assault technique entails one-on-one chat phishing, the place attackers use compromised Groups accounts or create malicious Entra ID tenants with .onmicrosoft.com domains – Microsoft’s default fallback domains for enterprise accounts with out customized area configurations.
The technical implementation begins with menace actors conducting reconnaissance by way of Groups’ person search performance, which permits exterior customers to confirm goal electronic mail addresses and ensure message supply capabilities.
When profitable, attackers can provoke direct communication, although Microsoft has applied safety warnings, together with “exterior communication warning” pop-ups and “potential phishing warning messages” that seem primarily based on algorithmic menace detection.
Nevertheless, attackers have found strategies to bypass these safety measures by way of voice name phishing (vishing).
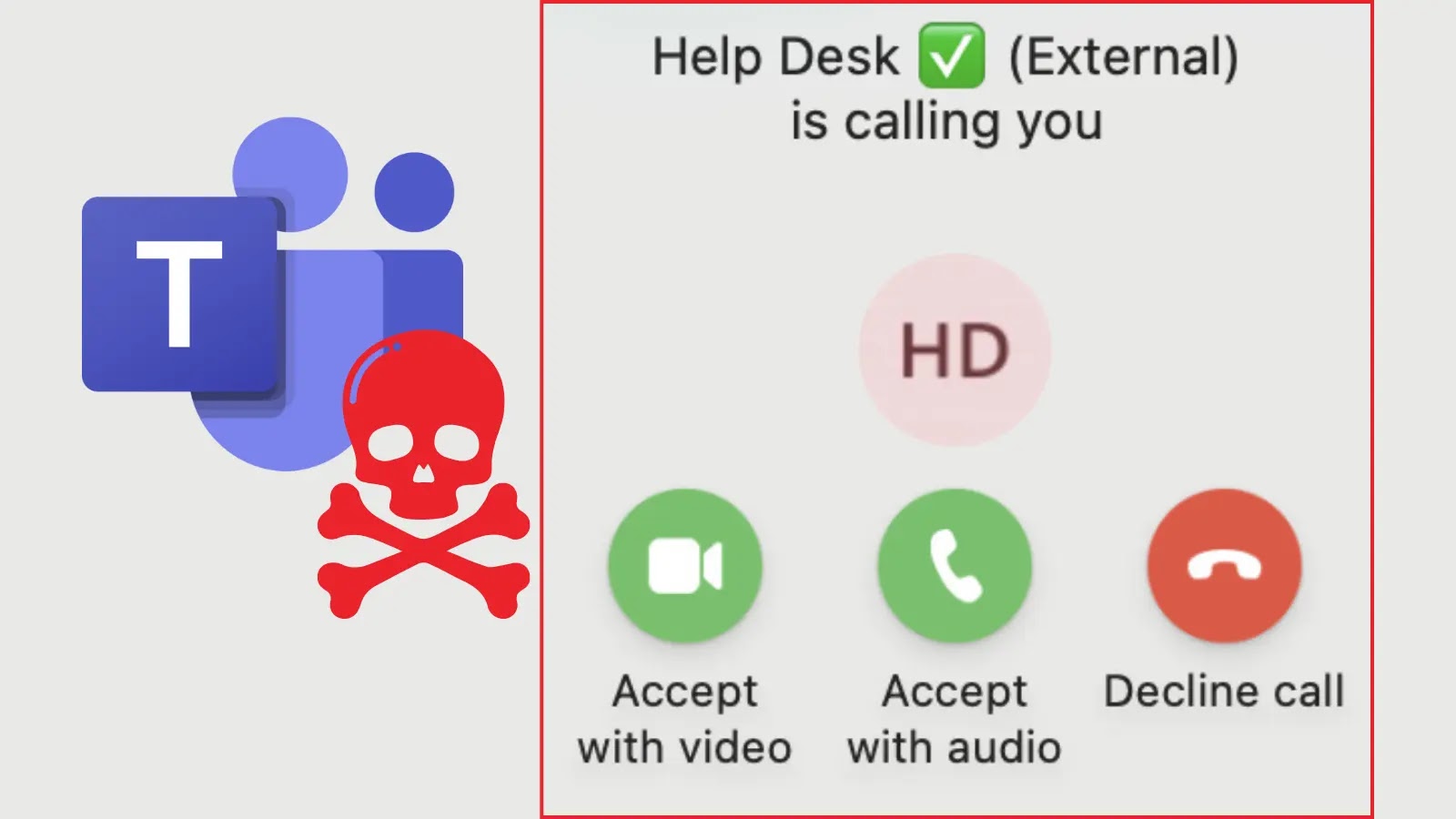
Pretend IT Helpdesk calling sufferer inside Microsoft Groups
In contrast to text-based communications, voice calls from exterior Groups customers generate no warning pop-ups, making a seamless assault vector.
As soon as belief is established by way of voice communication, attackers request display screen sharing permissions, enabling them to watch sufferer actions and doubtlessly information them by way of malicious actions.
Content material sharing configuration on Microsoft Groups
Probably the most regarding improvement entails distant management capabilities. Whereas Microsoft has applied safety controls that disable the “Give Management” and “Request Management” choices by default for exterior contributors, organizations which have modified these settings face important publicity, in keeping with the Axon Group.
Attackers can doubtlessly acquire full distant entry to sufferer workstations by way of Groups’ built-in distant management options, eliminating the necessity for conventional Distant Monitoring and Administration (RMM) instruments like QuickAssist or AnyDesk.
Detection Methodologies
Safety groups can establish these assaults by way of particular Microsoft 365 audit log entries that function digital forensic artifacts.
The first indicators embody ChatCreated occasions that set up new “OneOnOne” chats between attackers and victims, containing essential metadata together with Chat Thread IDs, sender show names, electronic mail addresses, and Group IDs for each events.
MessageSent logs complement ChatCreated entries by offering sender IP addresses and embedded URL info, although message content material itself is just not logged.
Further forensic indicators embody UserAccepted occasions when victims click on “Settle for” buttons in exterior sender pop-ups, and TeamsImpersonationDetected occasions triggered by Microsoft’s model impersonation detection algorithms.
Superior menace searching requires monitoring for particular M365 audit log patterns, together with ChatCreated operations with participant_info:has_foreign_tenant_users = true and communication_type = “OneOnOne” parameters.
As menace actors proceed refining these strategies, organizations should implement complete monitoring of Groups audit logs, person education schemes centered on IT helpdesk impersonation ways, and restrictive exterior communication insurance policies to mitigate this evolving menace panorama.
Discover this Story Attention-grabbing! Comply with us on LinkedIn and X to Get Extra On the spot Updates.