Aug 29, 2025Ravie LakshmananThreat Intelligence / Malware
Amazon on Friday stated it flagged and disrupted what it described as an opportunistic watering gap marketing campaign orchestrated by the Russia-linked APT29 actors as a part of their intelligence gathering efforts.
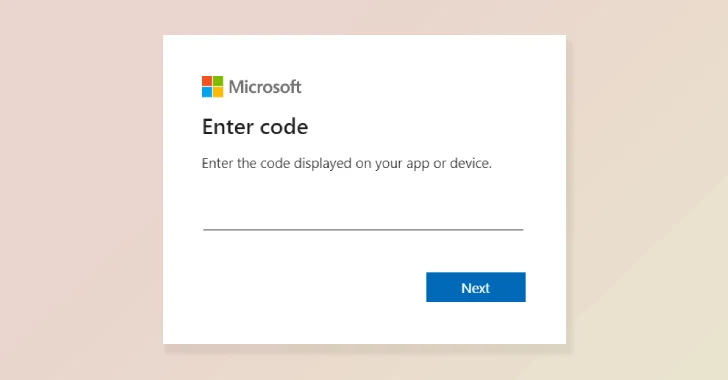
The marketing campaign used “compromised web sites to redirect guests to malicious infrastructure designed to trick customers into authorizing attacker-controlled gadgets by Microsoft’s system code authentication movement,” Amazon’s Chief Info Safety Officer CJ Moses stated.
APT29, additionally tracked as BlueBravo, Cloaked Ursa, CozyLarch, Cozy Bear, Earth Koshchei, ICECAP, Midnight Blizzard, and The Dukes, is the identify assigned to a state-sponsored hacking group with ties to Russia’s International Intelligence Service (SVR).
In current months, the prolific risk actor has been linked to assaults leveraging malicious Distant Desktop Protocol (RDP) configuration information to focus on Ukrainian entities and exfiltrate delicate information.
Because the begin of the 12 months, the adversarial collective has been noticed adopting numerous phishing strategies, together with system code phishing and system be part of phishing, to acquire unauthorized entry to Microsoft 365 accounts.
As just lately as June 2025, Google stated it noticed a risk cluster with affiliations to APT29 weaponizing a Google account characteristic referred to as application-specific passwords to achieve entry to victims’ emails. The extremely focused marketing campaign was attributed to UNC6293.
The most recent exercise recognized by Amazon’s risk intelligence group underscores the risk actor’s continued efforts to reap credentials and collect intelligence of curiosity, whereas concurrently sharpening their tradecraft.
“This opportunistic method illustrates APT29’s continued evolution in scaling their operations to forged a wider web of their intelligence assortment efforts,” Moses stated.
The assaults concerned APT29 compromising numerous reputable web sites and injecting JavaScript that redirected roughly 10% of tourists to actor-controlled domains, comparable to findcloudflare[.]com, that mimicked Cloudflare verification pages to provide an phantasm of legitimacy.
In actuality, the tip objective of the marketing campaign was to entice victims into coming into a reputable system code generated by the risk actor right into a sign-in web page, successfully granting them entry to their Microsoft accounts and information. This system was detailed by each Microsoft and Volexity again in February 2025.
The exercise can be noteworthy for incorporating numerous evasion methods, comparable to Base64 encoding to hide malicious code, setting cookies to forestall repeated redirects of the identical customer, and shifting to new infrastructure when blocked.
“Regardless of the actor’s makes an attempt emigrate to new infrastructure, together with a transfer off AWS to a different cloud supplier, our group continued monitoring and disrupting their operations,” Moses stated. “After our intervention, we noticed the actor register extra domains comparable to cloudflare.redirectpartners[.]com, which once more tried to lure victims into Microsoft system code authentication workflows.”