Sep 02, 2025The Hacker NewsData Privateness / SaaS Safety
The Harsh Truths of AI Adoption
MITs State of AI in Enterprise report revealed that whereas 40% of organizations have bought enterprise LLM subscriptions, over 90% of staff are actively utilizing AI instruments of their every day work. Equally, analysis from Harmonic Safety discovered that 45.4% of delicate AI interactions are coming from private e mail accounts, the place staff are bypassing company controls fully.
This has, understandably, led to loads of issues round a rising “Shadow AI Economic system”. However what does that imply and the way can safety and AI governance groups overcome these challenges?
Contact Harmonic Safety to be taught extra about Shadow AI discovery and imposing your AI utilization coverage.
AI Utilization Is Pushed by Workers, Not Committees
Enterprises incorrectly view AI use as one thing that comes top-down, outlined by their very own visionary enterprise leaders. We now know that is unsuitable. Most often, staff are driving adoption from the underside up, typically with out oversight, whereas governance frameworks are nonetheless being outlined from the highest down. Even when they’ve enterprise-sanctioned instruments, they’re typically eschewing these in favor of different newer instruments which can be better-placed to enhance their productiveness.
Except safety leaders perceive this actuality, uncover and govern this exercise, they’re exposing the enterprise to important dangers.
Why Blocking Fails
Many organizations have tried to fulfill this problem with a “block and wait” technique. This method seeks to limit entry to well-known AI platforms and hope adoption slows.
The truth is totally different.
AI is not a class that may be simply fenced off. From productiveness apps like Canva and Grammarly to collaboration instruments with embedded assistants, AI is woven into practically each SaaS app. Blocking one instrument solely drives staff to a different, typically via private accounts or dwelling gadgets, leaving the enterprise blind to actual utilization.
This isn’t the case for all enterprises, in fact. Ahead-leaning safety and AI governance groups wish to proactively perceive what staff are utilizing and for what use instances. They search to know what is occurring and assist their staff use the instruments as securely as potential.
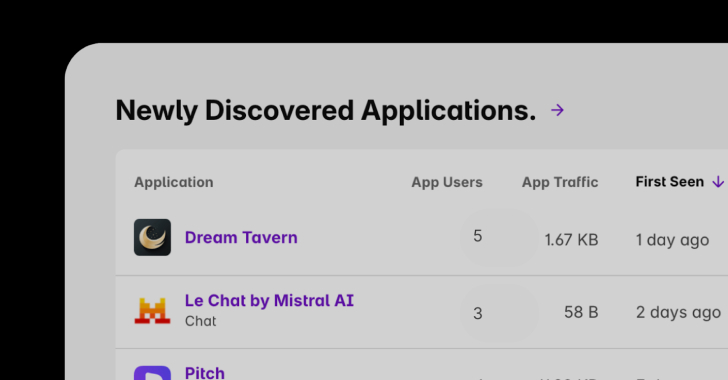
Shadow AI Discovery as a Governance Crucial
An AI asset stock is a regulatory requirement and never a nice-to-have. Frameworks just like the EU AI Act explicitly mandate organizations to keep up visibility into the AI techniques in use, as a result of with out discovery there isn’t any stock, and with out a listing there could be no governance. Shadow AI is a key part of this.
Completely different AI instruments pose totally different dangers. Some could quietly prepare on proprietary knowledge, others could retailer delicate data in jurisdictions like China, creating mental property publicity. To adjust to laws and defend the enterprise, safety leaders should first uncover the total scope of AI utilization, spanning sanctioned enterprise accounts and unsanctioned private ones.
As soon as armed with this visibility, organizations can separate low-risk use instances from these involving delicate knowledge, regulated workflows, or geographic publicity. Solely then can they implement significant governance insurance policies that each defend knowledge and allow worker productiveness.
How Harmonic Safety Helps
Harmonic Safety permits this method by delivering intelligence controls for worker use of AI. This consists of steady monitoring of Shadow AI, with off-the-shelf danger assessments for every software.
As a substitute of counting on static block lists, Harmonic supplies visibility into each sanctioned and unsanctioned AI use, then applies sensible insurance policies based mostly on the sensitivity of the information, the function of the worker, and the character of the instrument.
Meaning a advertising staff is likely to be permitted to place particular data into particular instruments for content material creation, whereas HR or authorized groups are restricted from utilizing private accounts for delicate worker data. That is underpinned by fashions that may determine and classify data as staff share the information. This allows groups to implement AI insurance policies with the mandatory precision.
The Path Ahead
Shadow AI is right here to remain. As extra SaaS functions embed AI, unmanaged use will solely increase. Organizations that fail to deal with discovery right this moment will discover themselves unable to control tomorrow.
The trail ahead is to control it intelligently, somewhat than block it. Shadow AI discovery provides CISOs the visibility they should defend delicate knowledge, meet regulatory necessities, and empower staff to securely reap the benefits of AI’s productiveness advantages.
Harmonic Safety is already serving to enterprises take this subsequent step in AI governance.
For CISOs, it is not a query of whether or not staff are utilizing Shadow AI…it is whether or not you may see it.
Discovered this text fascinating? This text is a contributed piece from one among our valued companions. Comply with us on Google Information, Twitter and LinkedIn to learn extra unique content material we put up.