A complicated community of Ukrainian-based autonomous methods has emerged as a big cybersecurity risk, orchestrating large-scale brute-force and password-spraying assaults towards SSL VPN and RDP infrastructure.
Between June and July 2025, these malicious networks launched a whole lot of hundreds of coordinated assaults over durations lasting as much as three days, focusing on essential enterprise distant entry methods.
The marketing campaign includes a fancy internet of interconnected networks, primarily centered round three Ukrainian autonomous methods: FDN3 (AS211736), VAIZ-AS (AS61432), and ERISHENNYA-ASN (AS210950), together with a Seychelles-based community TK-NET (AS210848).
These networks had been strategically allotted in August 2021 and have since engaged in systematic infrastructure manipulation, regularly exchanging IPv4 prefixes to evade blocklisting efforts and preserve operational continuity.
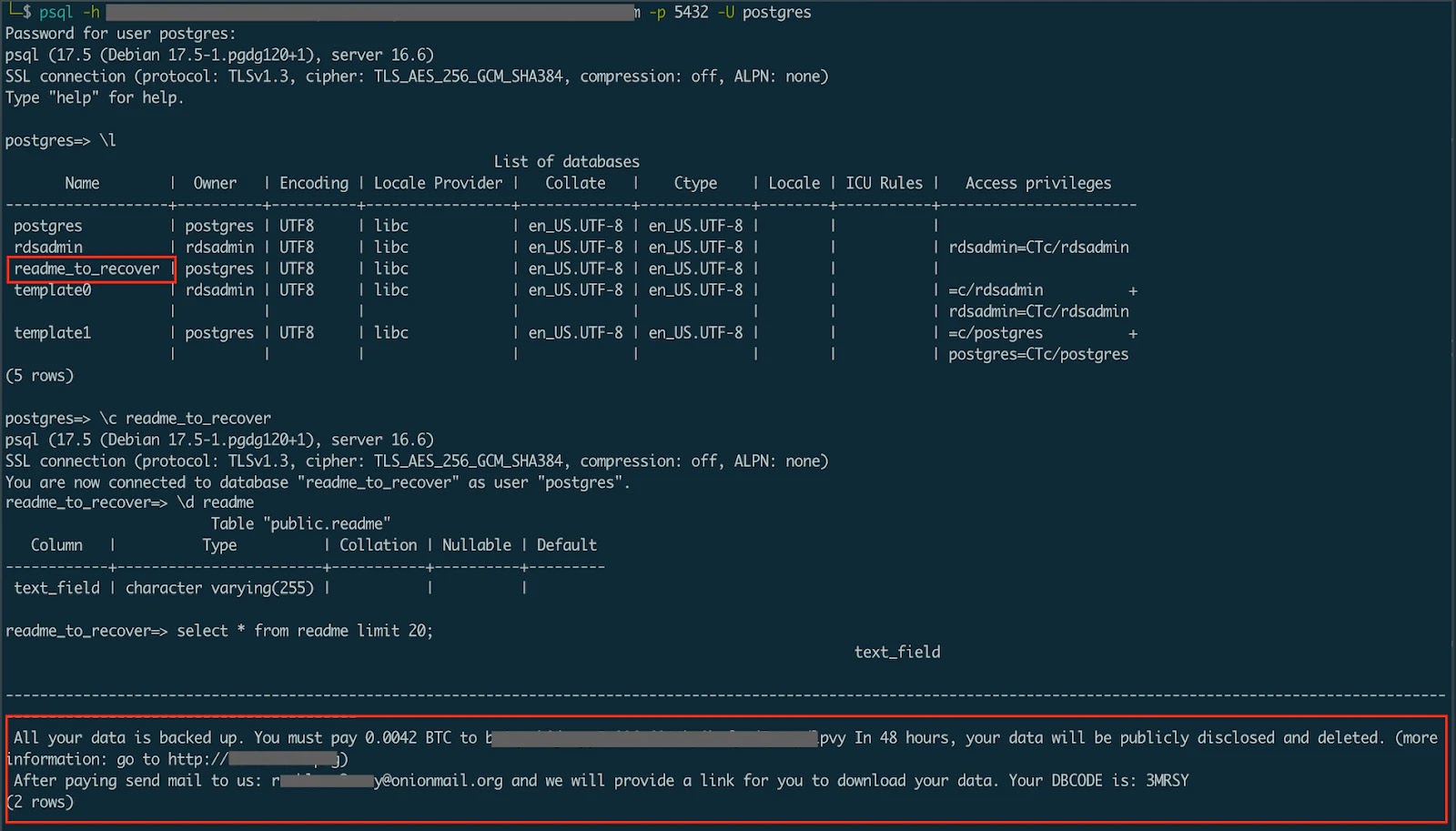
Intrinsec researchers recognized this risk infrastructure by means of intensive monitoring of honeypot networks, revealing assault patterns that peaked at over 1.3 million particular person makes an attempt throughout a three-day interval in July 2025.
The attackers demonstrated subtle coordination, with a number of IP addresses concurrently launching similar assault patterns towards uncovered VPN endpoints and Distant Desktop Protocol companies.
The legal infrastructure operates by means of partnerships with established bulletproof internet hosting suppliers, most notably IP Quantity Inc. (AS202425), a Seychelles-based entrance firm created by Ecatel’s operators.
This association supplies the Ukrainian networks with each anonymity and resilience, permitting them to take care of operations regardless of legislation enforcement consideration and business blocklisting efforts.
Community Infrastructure and Assault Mechanics
The technical structure of those assaults reveals cautious planning and useful resource allocation. The first assault vector makes use of coordinated IP ranges, with prefix 88.210.63.0/24 serving as a focus for probably the most intensive campaigns.
Structure summarizing the hyperlinks shared between the above-mentioned entities (Supply – Intrinsec)
Evaluation of assault logs exhibits exactly synchronized activation patterns, with particular person IP addresses producing between 108,000 and 113,000 assault makes an attempt every throughout peak operations.
The attackers make use of password spraying methods somewhat than conventional brute-force strategies, making an attempt widespread passwords throughout massive volumes of accounts to keep away from account lockout mechanisms.
This method proves notably efficient towards organizations with weak password insurance policies or insufficient price limiting on authentication endpoints.
The campaigns particularly goal Fortinet, Palo Alto, and Cisco VPN home equipment, aiming to ascertain high-privilege preliminary entry factors that may bypass conventional endpoint detection and response options.
Community visitors evaluation reveals that the infrastructure maintains persistent command-and-control communications by means of Amadey malware panels hosted throughout the identical autonomous methods.
A number of C2 servers stay energetic, together with 185.156.72.96 with 126 energetic bot connections and 185.156.72.97 sustaining 122 compromised endpoints, indicating profitable post-exploitation actions past the preliminary entry makes an attempt.
Enhance your SOC and assist your workforce shield your corporation with free top-notch risk intelligence: Request TI Lookup Premium Trial.