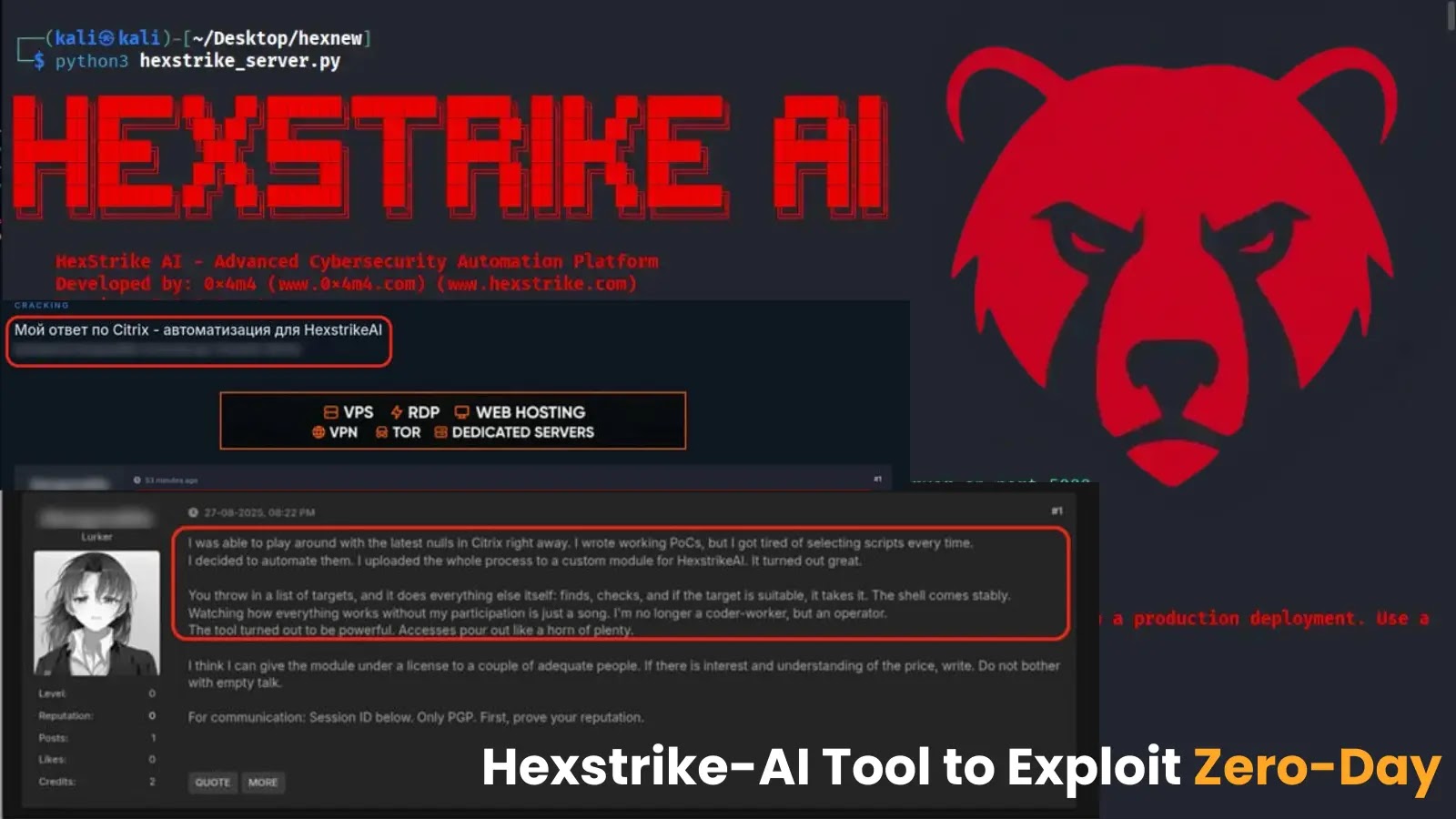
Risk actors are quickly weaponizing Hexstrike-AI, a not too long ago launched AI-powered offensive safety framework, to scan for and exploit zero-day CVEs in underneath ten minutes.
Initially marketed as an offensive safety framework for pink groups, Hexstrike-AI’s structure has already been repurposed by malicious operators inside hours of its public launch.
Key Takeaways1. Hexstrike-AI automates zero-day exploits in underneath 10 minutes.2. It hyperlinks LLMs to 150+ instruments for resilient workflows.3. Quickly weaponized towards Citrix CVEs, driving pressing AI-driven defenses.
Hexstrike-AI Automates Exploits in Minutes
Checkpoint’s current evaluation reveals how synthetic intelligence (AI) can handle and simplify complicated assaults by coordinating many specialised brokers. This AI-driven system helps automate multi-step assaults extra effectively.
With Hexstrike-AI, that concept has change into operational. The framework stands on a FastMCP server core, binding large-language fashions (Claude, GPT, Copilot) to over 150 safety instruments through MCP decorators.
AI brokers can invoke standardized features reminiscent of nmap_scan(goal, choices) and execute_exploit(cve_id, payload) with out human micromanagement.
Darkish-web chatter confirmed that risk actors are testing Webshell deployments towards the freshly disclosed Citrix NetScaler ADC and Gateway CVEs CVE-2025-7775, CVE-2025-7776, and CVE-2025-8424 inside hours of disclosure.
Hexstrike-AI’s MCP orchestration layer interprets high-level instructions, reminiscent of “exploit NetScaler,” into sequenced technical workflows.
Every stage of reconnaissance, memory-handling exploitation, persistence through webshell, and exfiltration is dealt with by specialised MCP brokers, guaranteeing retry logic and automatic resilience.
CheckPoint noticed that, to the underground posts, operators achieved unauthenticated distant code execution on weak home equipment and dropped internet shells in underneath ten minutes.
Darkish internet posts discussing HexStrike AI, shortly after its launch
The structure of Hexstrike-AI implements:
Abstraction Layer: Interprets imprecise operator intent into exact operate calls.
MCP Brokers: Autonomous servers bridging LLMs with instruments, orchestrating every part from nmap_scan and hydra_brute to customized NetScaler exploit modules.
Automation & Resilience: Constructed-in retry loops and failure restoration guarantee chained operations proceed with out human intervention.
Intent-to-Execution Translation: The execute_command API dynamically constructs and executes workflows primarily based on intent strings.
This mannequin mirrors educational projections of AI orchestration driving next-gen cyberattacks—now crystallized in Hexstrike-AI’s code.
Citrix’s August 26 advisories revealed three important NetScaler vulnerabilities. Historically, exploiting such reminiscence and access-control flaws demanded skilled reverse engineering and exploit writing.
Darkish internet submit claiming to have efficiently exploited Citrix CVEs utilizing HexStrike AI
Hexstrike-AI collapses that barrier, enabling parallelized scanning of 1000’s of IPs and dynamic adaptation of exploit parameters till success.
The time-to-exploit for CVE-2025-7775 has already been decreased from weeks to minutes, with webshell-equipped home equipment showing on underground markets.
Mitigations
Organizations should quicken patching cycles and implement adaptive, AI-driven detection programs.
Static signatures alone is not going to suffice towards quickly orchestrated assaults. Monitoring dark-web intelligence for early indicators, implementing segmentation and least-privilege fashions, and integrating autonomous response playbooks are important.
Defenders should sustain with the expansion of AI-powered offenses by means of telemetry correlation and machine-speed patch validation.
Discover this Story Fascinating! Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates.