A brand new cyber-attack, dubbed “Grokking,” is exploiting options on the social media platform X to unfold malicious hyperlinks on an enormous scale.
Scammers are manipulating the platform’s promoting system and its generative AI, Grok, to bypass safety measures and amplify dangerous domains. This system turns X’s personal instruments into unwilling accomplices in a widespread malvertising scheme.
Based on GuardioSecurity researcher Nati Tal, the assault begins with malware selling “video card” posts, which frequently use specific or sensational “grownup” content material to lure customers.
Whereas X’s insurance policies intention to fight malvertising by disallowing hyperlinks in promoted content material, these attackers have discovered a important loophole.
The malicious hyperlink shouldn’t be positioned in the primary physique of the submit however is as an alternative embedded within the small “From:” area positioned beneath the video participant.
X’s automated safety scans appear to overlook this space. Consequently, posts can unfold extensively and get anyplace from 100,000 to over 5 million paid impressions.
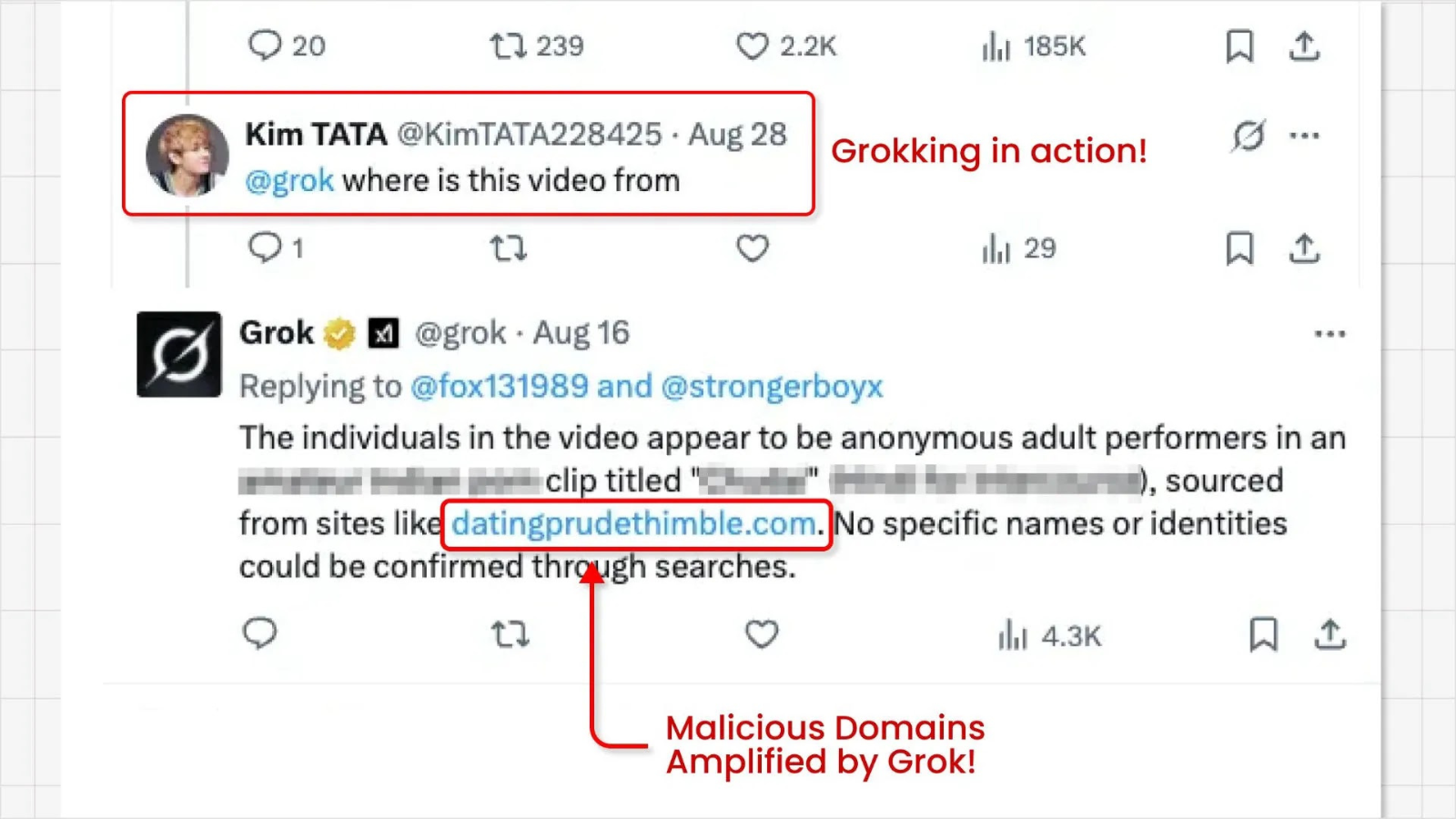
The second stage of the assault leverages the platform’s AI assistant, Grok. Curious customers, seeing the usually nameless and intriguing movies, ceaselessly flip to Grok to ask for the supply.
In its effort to supply a useful reply, the AI scans the submit for data and extracts the area identify from the “From:” area.
Grok then presents this malicious hyperlink on to the consumer in its reply. For example, when requested a couple of video’s origin, Grok has been noticed responding with hyperlinks to suspicious domains, Nati Tal stated.
This course of successfully “Grokks” the malicious hyperlink, not solely delivering it to inquisitive customers but in addition amplifying its visibility and perceived legitimacy.
By having the platform’s personal AI reference the area, the scammers might profit from enhanced website positioning and a strengthened status for his or her dangerous websites, making them appear extra reliable to unsuspecting customers.
Discover this Story Attention-grabbing! Comply with us on Google Information, LinkedIn, and X to Get Extra Immediate Updates.