A complicated malware marketing campaign, dubbed “GPUGate,” abuses Google Advertisements and GitHub’s repository construction to trick customers into downloading malicious software program.
The Arctic Wolf Cybersecurity Operations Middle, the assault chain makes use of a novel method to evade safety evaluation by leveraging a pc’s Graphics Processing Unit (GPU).
The marketing campaign seems to be the work of a Russian-speaking menace actor and is actively focusing on IT professionals in Western Europe.
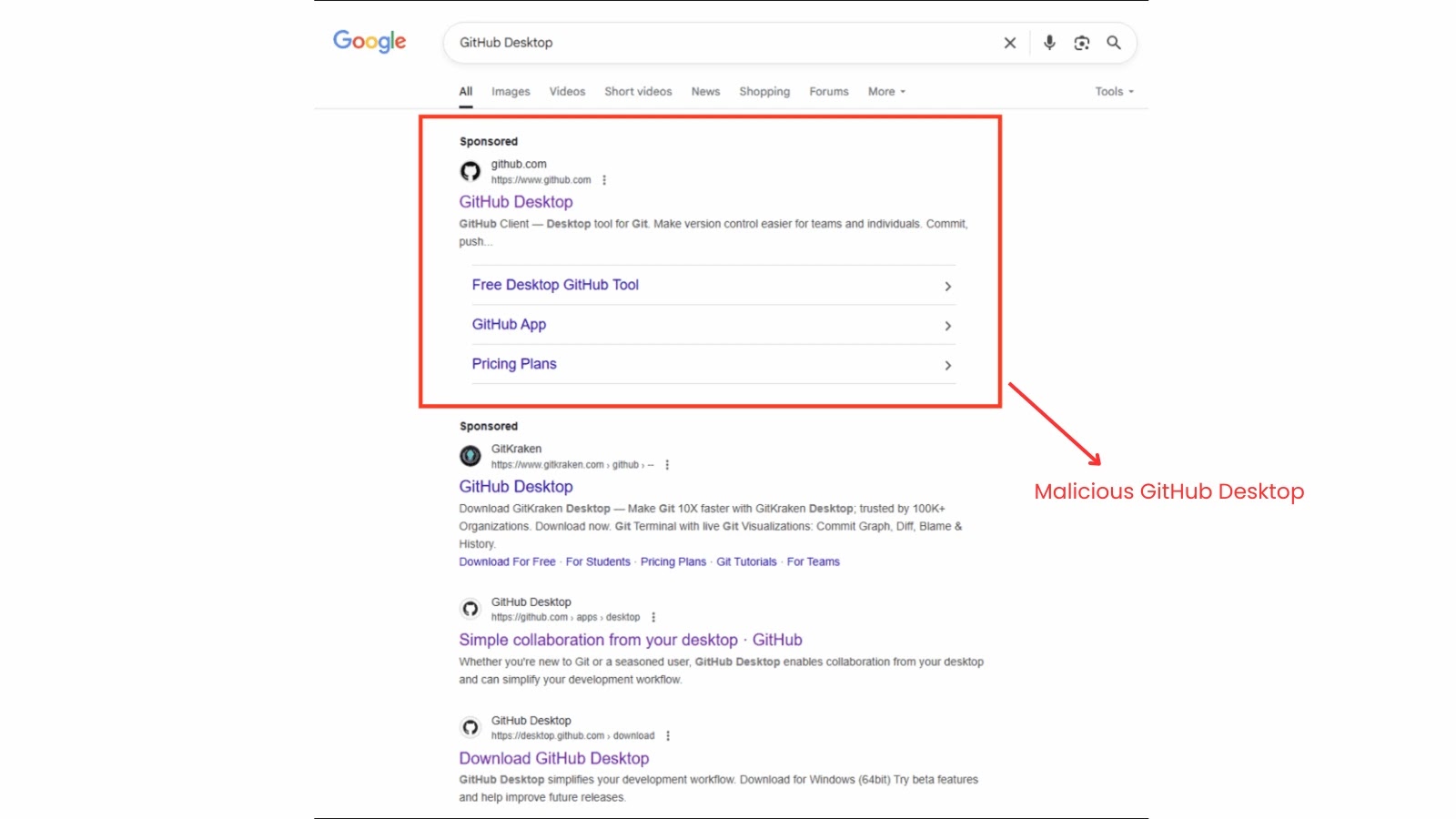
The assault begins with malicious promoting, the place attackers place a sponsored advert on the prime of Google search outcomes for phrases like “GitHub Desktop.” This advert directs customers to what seems to be a professional GitHub web page.
Google search outcomes for GitHub Desktop
In actuality, the hyperlink results in a particular, manipulated “commit” web page inside a repository. This web page appears to be like genuine, retaining the repository’s title and metadata, however comprises altered obtain hyperlinks that time to an attacker-controlled area.
This “belief bridge” exploits the person’s confidence in each Google and GitHub to ship the malicious payload.
What makes GPUGate notably notable is its distinctive evasion technique. The preliminary installer is a big 128 MB file, designed to bypass safety sandboxes that always have file measurement limits.
weaponized GitHub Desktop
Its most modern function is a GPU-gated decryption routine. The malware will solely decrypt its malicious payload if it detects an actual, bodily GPU with a tool title longer than ten characters, Arctic Wolf stated.
It is a deliberate tactic to thwart evaluation, because the digital machines and sandboxes utilized by safety researchers usually have generic, brief GPU names or no GPU in any respect. On such techniques, the payload stays encrypted and inert.
The first objective of this marketing campaign is to achieve preliminary entry to organizational networks for malicious actions, together with credential theft, knowledge exfiltration, and ransomware deployment.
By focusing on builders and IT employees, people prone to search instruments like GitHub Desktop, the attackers purpose for victims with elevated community privileges.
As soon as executed, the malware makes use of a PowerShell script to achieve administrative rights, create scheduled duties for persistence, and add exclusions to Home windows Defender to keep away from detection. The marketing campaign has been energetic since not less than December 2024 and represents an evolving and vital menace.
Discover this Story Attention-grabbing! Observe us on Google Information, LinkedIn, and X to Get Extra On the spot Updates.