Each SOC analyst is aware of the frustration. Your SIEM generates a whole lot, generally 1000’s of alerts every day.
Every alert calls for consideration, however with restricted time and sources, how do you prioritize successfully? Investigating every alert in isolation leaves groups reactive, overwhelmed, and in the end weak to classy assaults that mix into the background noise.
The Alert Triage Dilemma: Drowning in Knowledge, Ravenous for Context
The problem isn’t simply quantity; it’s context. An IP handle flagged in your community may appear innocuous till you uncover it’s been actively concentrating on firms in your business for weeks.
A file hash that seems benign might be a part of a broader marketing campaign that’s already compromised your rivals. With out this broader intelligence image, even expert analysts function with one hand tied behind their again.
Menace actors can set up persistence, exfiltrate information, and disappear inside hours, generally minutes. Your detection capabilities have to match this velocity, figuring out threats not simply precisely, however instantly upon first contact.
That is the place the idea of collective protection turns into invaluable. Whereas your group could also be seeing a selected indicator for the primary time, the worldwide safety group could have encountered it repeatedly.
The problem lies in accessing this collective information in actionable, real-time codecs that combine seamlessly into your present workflows. That is the problem that providers like ANY.RUN’s Menace Intelligence Lookup settle for.
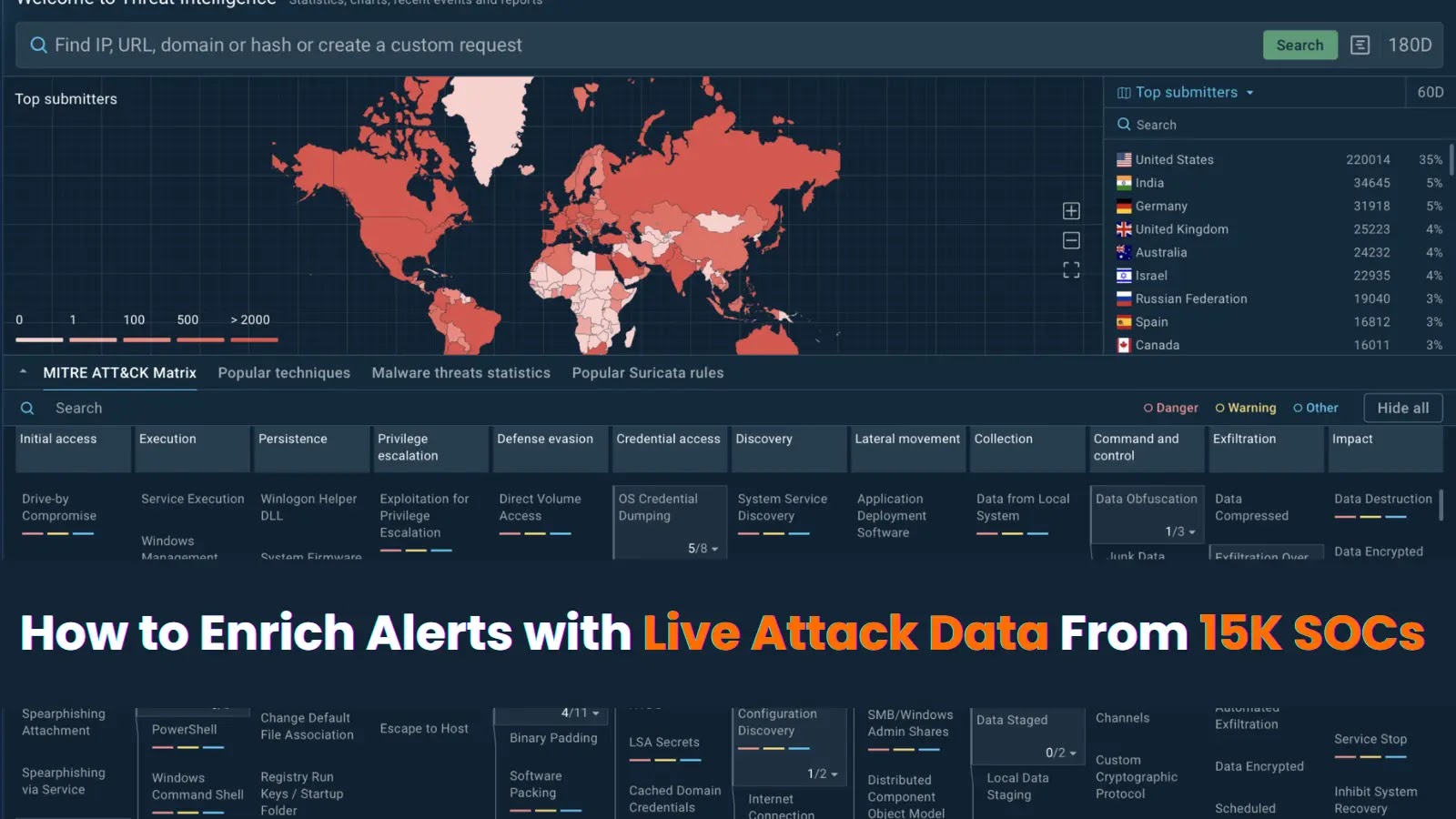
Menace Intelligence Lookup predominant web page: search IOCs, discover TTPs, use YARA guidelines
Business as a Goal: You’re Not Alone in Their Crosshairs
Attackers hardly ever goal particular person firms in isolation. They aim industries, provide chains, and geographic areas. For those who’re in monetary providers and your rivals are beneath assault, you’re possible subsequent.
For those who’re a healthcare supplier and related organizations in your area are being compromised, think about your self on borrowed time.
Menace actors make investments important sources in understanding particular business verticals, creating specialised instruments and methods optimized for specific enterprise environments.
As soon as they’ve honed their strategy in opposition to one goal in your sector, they’ll systematically apply these confirmed strategies throughout related organizations.
Why Outdoors Incident Knowledge Is Priceless
Intelligence about assaults in opposition to business friends isn’t simply attention-grabbing context. It’s predictive intelligence.
When analysts perceive the whole scope of ongoing campaigns in opposition to their sector, they will proactively hunt for early indicators relatively than anticipate assaults to completely manifest of their surroundings.
Your SOC sees what occurs in your community. However attackers are reusing domains, IPs, samples, and behaviors throughout many victims.
Accessing incident information from different firms offers you a shortcut: as a substitute of spending hours determining if an alert is malicious, you may examine immediately in opposition to real-world assault information.
ANY.RUN Menace Intelligence Lookup: Immediate IOC Validation
With Menace Intelligence Lookup, SOC analysts can:
Enter an IOC (hash, IP, area, URL, or file).
Immediately see whether or not it appeared in real-world assaults noticed throughout 1000’s of SOCs.
Get context comparable to malware household, habits, and timestamps of exercise.
Validate whether or not an alert factors to an actual, ongoing risk — or simply background noise
This shifts alert triage from handbook, time-consuming validation to quick, assured decision-making backed by dwell assault proof.
Begin utilizing TI Lookup without cost to make fast selections on potential threats: Signal as much as begin.
The supply of the risk information explorable by TI Lookup is ANY.RUN’s Interactive Sandbox.
It’s used every day by over 15,000 SOCs worldwide: analysts at these organizations detonate suspicious recordsdata, examine malware habits, and analyze assault campaigns utilizing ANY.RUN’s cloud-based surroundings. This creates an unprecedented repository of dwell assault intelligence.
For risk analysts and hunters, ANY.RUN’s Menace Intelligence Lookup supplies:
Quicker triage: Immediately affirm whether or not an alert IOC is tied to a dwell assault.
Decreased fatigue: Minimize hours of handbook investigation by checking IOCs in seconds.
Increased detection confidence: Spot adversaries utilizing the identical infrastructure elsewhere.
Higher looking: Pivot on associated IOCs and uncover hidden connections in your surroundings.
Collective protection: Leverage the insights of 15,000 SOCs worldwide to strengthen your individual.
TI Lookup in Motion: Tips on how to Use It
ANY.RUN’s Menace Intelligence Lookup is out there on a free plan with restricted search parameters permitting to finish primary analyst duties.
Let’s take the above-mentioned use case to see the way it works: a doubtful IP handle detected in your system. Look it up and get an prompt verdict:
An IP lookup outcomes with a fast verdict and extra IOCs
We are able to see that the IP has been flagged as malicious and has been noticed in most up-to-date incidents. For extra context, we will change to the “Analyses” tab and rapidly uncover that it belongs to Agent Tesla adware:
destinationIP:”173.254.31.34″
Malware samples analyzed within the Sandbox, discovered by IP search
Premium Capabilities for Superior Safety Operations
When you find yourself prepared for a level-up, the Premium plan transforms TI Lookup right into a complete safety intelligence platform:
Superior Search Operations: Over 40 search parameters with complicated operators (AND, OR, NOT) allow exact risk looking and investigation workflows.
Full Assault Visibility: Entry to all accessible evaluation classes relatively than simply the 20 most up-to-date, offering complete historic context.
Personal Intelligence: Conduct confidential searches and investigations with out visibility to different customers, defending delicate safety operations.
Steady Monitoring: Search Updates characteristic supplies automated alerts when new threats match your specified standards, guaranteeing your group stays forward of rising campaigns.
Knowledgeable Evaluation: TI Studies from ANY.RUN’s analyst group ship strategic insights on assault developments and risk actor actions throughout industries.
Right here is an instance of a lookup search question you need to use on Premium plan: extra search parameters (registryKey, registryValue) and operators (NOT) can be found; over 500 sandbox classes discovered in order that an analyst can observe sure malware habits.
registryKey:”Run$” AND registryValue:”.url$” NOT threatName:”darkvision”
Malware samples demonstrating sure habits discovered by way of TI Lookup
Request full entry to TI Lookup for actionable risk investigation: Contact ANY.RUN now
Embrace the Energy of Collective Protection
The trendy risk panorama calls for a basic shift from remoted protection to collective intelligence. No single group, no matter dimension or sources, can match the excellent risk visibility that emerges from world collaboration.
ANY.RUN’s Menace Intelligence Lookup represents this collaborative strategy in motion: prompt entry to intelligence derived from 15,000 SOCs struggling to investigate and perceive energetic threats.
In a world the place attackers share methods, instruments, and targets throughout the worldwide risk panorama, defenders should reply with equal coordination and real-time intelligence sharing.
ANY.RUN’s Menace Intelligence Lookup supplies the speedy entry infrastructure to make this collective protection sensible and operational.