A safety vulnerability has been discovered within the Google Drive Desktop software for Home windows. It permits a logged-in consumer on a shared machine to entry one other consumer’s Drive recordsdata utterly with no need their credentials.
This vulnerability stems from a damaged entry management mechanism in how the applying handles cached knowledge.
Whereas Google Drive is broadly trusted for its safety and comfort by thousands and thousands for storing delicate knowledge, this vulnerability challenges these assumptions.
The problem lies throughout the app’s native caching system, generally known as DriveFS, which fails to correctly isolate cached recordsdata between totally different consumer profiles on a Home windows system.
Vulnerability And Exploitation
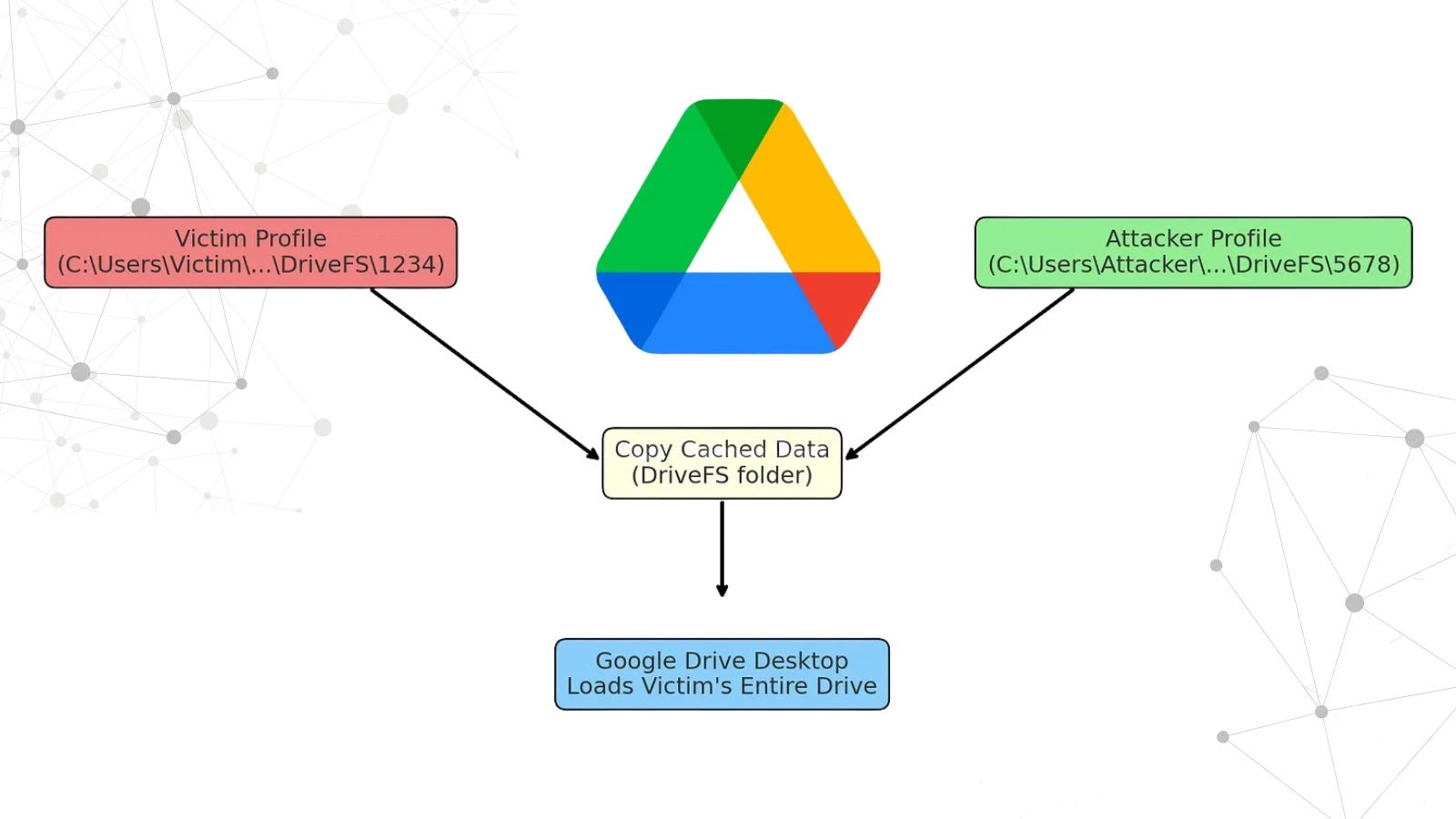
In line with Abdelghani Alhijawi, the Google Drive Desktop app caches synchronized recordsdata in an area listing (DriveFS).
Resulting from improper isolation, an attacker can entry a sufferer’s cached DriveFS folder, copy its contents, and exchange their very own DriveFS folder with the sufferer’s knowledge.
Upon restarting the applying, Google Drive hundreds the sufferer’s complete drive, together with “My Drive” and “Shared Drives,” as if it belonged to the attacker, with none re-authentication prompts.
Google Drive Desktop Home windows Vulnerability
This exploit instantly contravenes basic safety ideas:
Zero Belief: The appliance incorrectly trusts the copied cache with out verifying the consumer identification.
Encryption at Relaxation: Cached recordsdata aren’t individually encrypted for every consumer, permitting them to be reused throughout totally different accounts.
Re-authentication: The appliance doesn’t require a password or any type of re-login when a special consumer’s cache is loaded.
This vulnerability presents a basic insider menace state of affairs, significantly harmful in environments with shared workstations like workplaces, universities, or co-working areas.
An worker or any consumer on a shared system can covertly copy one other particular person’s Drive cache, having access to delicate recordsdata comparable to contracts, monetary information, HR paperwork, or proprietary supply code, Abdelghani Alhijawi mentioned.
The potential for knowledge exfiltration, modification, or deletion is substantial, posing dangers of privateness violations, compliance failures beneath rules like GDPR and HIPAA, and important reputational injury.
Insider threats are a recognized and expensive drawback, accounting for 22% of safety breaches in line with the 2024 Verizon DBIR and costing firms a median of $15.38 million yearly, as reported by a 2022 Ponemon/IBM examine.
The vulnerability locations the Google Drive Desktop app out of alignment with main world safety requirements like NIST SP 800-53, ISO 27001, and SOC 2.
These frameworks mandate strict knowledge isolation, least privilege entry, encryption of knowledge at relaxation, and strong session administration all of that are compromised by this flaw.
The researcher who found the difficulty reported it to Google’s vulnerability program however was informed, “This isn’t thought of a safety bug.”
This response is regarding, because the flaw represents a failure to stick to Zero Belief ideas and leaves customers uncovered to important dangers.
Suggestions For Customers
Till Google addresses this problem, customers and organizations are suggested to take precautions:
Keep away from utilizing Google Drive Desktop on shared or multi-user computer systems.
Implement strict permissions on separate Home windows consumer profiles.
Use the applying solely on devoted and managed endpoints to attenuate insider menace dangers.
In the end, the duty for securing consumer knowledge lies with the service supplier.
By failing to implement per-user encryption, requiring re-authentication for cached periods, and adhering to Zero Belief ideas, Google Drive Desktop at the moment falls in need of important safety expectations.
Discover this Story Fascinating! Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates.