FastNetMon, a distinguished supplier of DDoS detection options, introduced this week that it had recognized and helped mitigate a record-breaking distributed denial-of-service (DDoS) assault.
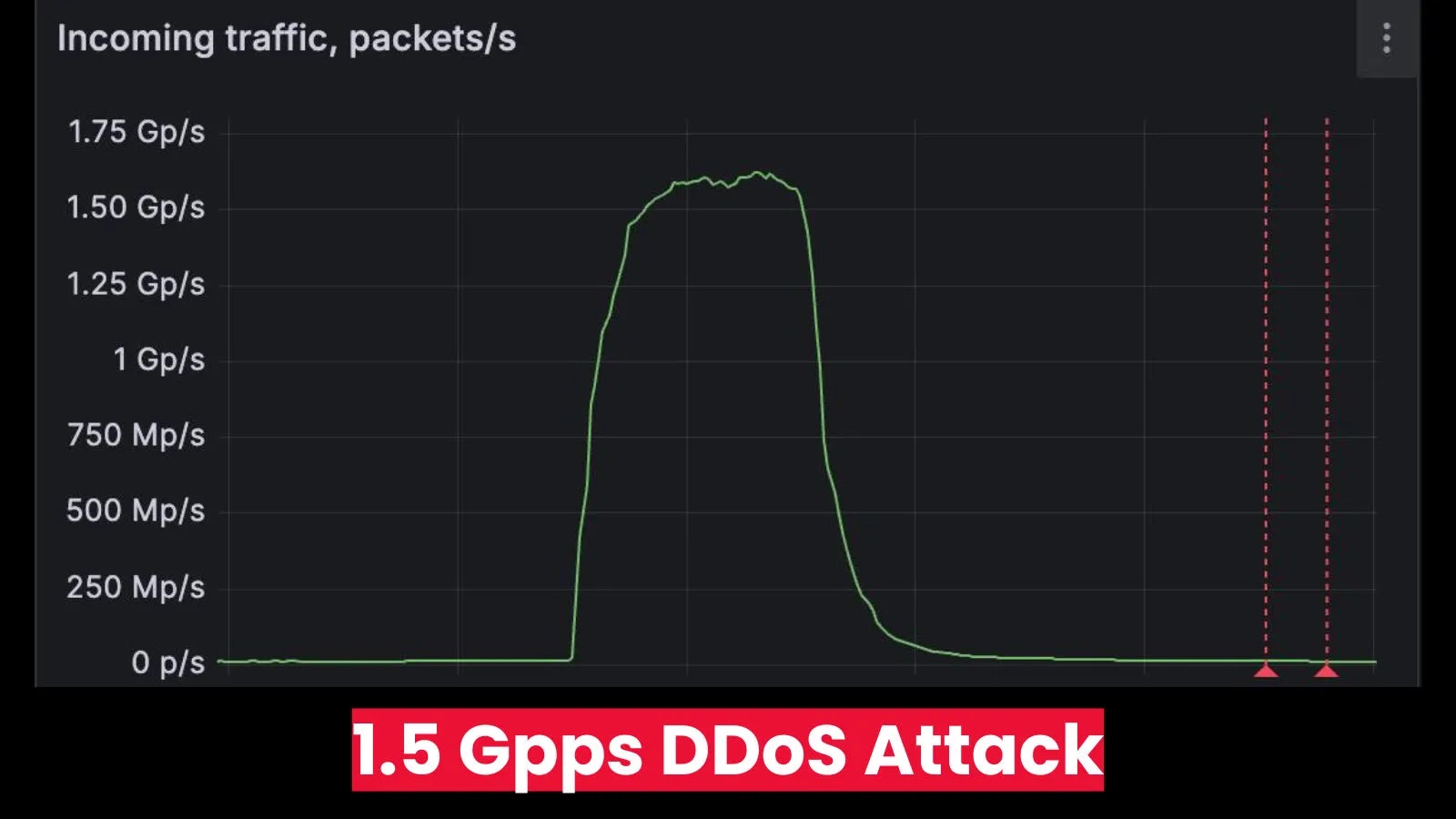
The assault focused a serious DDoS scrubbing vendor situated in Western Europe, pushing packet-forwarding charges to an astonishing 1.5 billion packets per second (1.5 Gpps).
This incident stands as one of the vital intense packet-rate floods ever publicly disclosed. The assault was primarily a UDP flood, a normal methodology utilized by menace actors to overwhelm a goal’s sources.
The malicious site visitors originated from an unlimited and globally distributed botnet of compromised customer-premises gear (CPE).
DDoS Assault
This community of hijacked gadgets included on a regular basis electronics similar to IoT devices and routers, unfold throughout greater than 11,000 distinctive networks world wide.
By harnessing a lot of gadgets, the attackers had been in a position to generate a crippling quantity of site visitors directed at a single goal, sarcastically, an organization that makes a speciality of defending in opposition to such occasions.
This huge packet flood comes simply days after Cloudflare reported mitigating a separate, colossal 11.5 Tbps DDoS assault, signaling a transparent and worrying escalation within the capabilities of cybercriminals.
Whereas that assault targeted on bandwidth quantity (bits per second), the FastNetMon incident highlights a special however equally harmful vector: packet quantity (packets per second).
Excessive packet-per-second charges are designed to exhaust the {hardware} and software program sources of community gear like routers and firewalls, which might solely course of a finite variety of packets at any given time, no matter their bandwidth.
“This occasion is a part of a harmful pattern,” said Pavel Odintsov, Founding father of FastNetMon. He warned of the rising menace panorama the place tens of 1000’s of insecure shopper gadgets may be weaponized into highly effective, coordinated assault instruments.
The system, which employs extremely optimized C++ algorithms for real-time community site visitors evaluation, routinely recognized the anomalous flood inside seconds of its launch.
This speedy alert enabled the seller to activate its mitigation protocols, efficiently stopping any important disruption to its companies and defending its infrastructure from being overwhelmed.
The incident highlights the essential significance of high-speed, automated detection in an period of more and more subtle DDoS threats.
Discover this Story Fascinating! Comply with us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates.