Sep 11, 2025Ravie LakshmananArtificial Intelligence / Cell Safety
Google on Tuesday introduced that its new Google Pixel 10 telephones assist the Coalition for Content material Provenance and Authenticity (C2PA) commonplace out of the field to confirm the origin and historical past of digital content material.
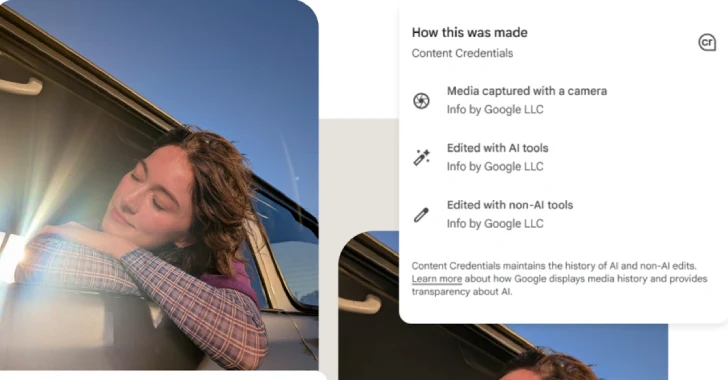
To that finish, assist for C2PA’s Content material Credentials has been added to Pixel Digital camera and Google Photographs apps for Android. The transfer, Google stated, is designed to additional digital media transparency.
C2PA’s Content material Credentials are a tamper-evident, cryptographically signed digital manifest offering verifiable provenance for digital content material corresponding to photographs, movies, or audio information. The metadata sort, in accordance with Adobe, serves as a “digital vitamin label,” giving details about the creator, the way it was made, and if it was generated utilizing synthetic intelligence (AI).
“The Pixel Digital camera app achieved Assurance Degree 2, the best safety ranking at present outlined by the C2PA Conformance Program,” Google’s Android Safety and C2PA Core groups stated. “Assurance Degree 2 for a cellular app is at present solely doable on the Android platform.”
“Pixel 10 telephones assist on-device trusted time-stamps, which ensures photographs captured along with your native digital camera app might be trusted after the certificates expires, even when they have been captured when your machine was offline.”
The potential is made doable utilizing a mix of Google Tensor G5, Titan M2 safety chip, and hardware-backed security measures constructed into the Android working system.
Google stated it has carried out C2PA to be safe, verifiable, and usable offline, thereby making certain that provenance knowledge is reliable, the method isn’t personally identifiable, and works even when the machine isn’t linked to the web.
That is achieved utilizing –
Android Key Attestation to permit Google C2PA Certification Authorities (CAs) to confirm that they’re speaking with a real bodily machine
{Hardware}-backed Android Key Attestation certificates that embrace the package deal identify and signing certificates related to the app that requested the technology of the C2PA signing key to confirm the request originated from a trusted, registered app
Producing and storing C2PA declare signing keys utilizing Android StrongBox within the Titan M2 safety chip for tamper-resistance
Nameless, hardware-backed attestation to certify new cryptographic keys generated on-device with out understanding who’s utilizing it
Distinctive certificates to signal every picture, making it “cryptographically inconceivable” to deanonymize the creator
On-device, offline Time-Stamping Authority (TSA) part inside the Tensor chip to generate cryptographically-signed time-stamps when the digital camera’s shutter is pressed
“C2PA Content material Credentials are usually not the only resolution for figuring out the provenance of digital media,” Google stated. “They’re, nevertheless, a tangible step towards extra media transparency and belief as we proceed to unlock extra human creativity with AI.”