A brand new kernel deal with leak vulnerability has been found within the newest variations of Home windows 11 (24H2) and Home windows Server 2022 (24H2).
The flaw, recognized as CVE-2025-53136, was satirically launched by a Microsoft patch supposed to repair a separate vulnerability, CVE-2024-43511.
In accordance with Crowdfense, the brand new bug undermines latest safety enhancements in Home windows, offering a dependable methodology for attackers to bypass Kernel Deal with Area Structure Randomization (KASLR), a important protection mechanism.
In latest updates, notably beginning with the 24H2 variations of Home windows 11 and Home windows Server 2022, Microsoft took vital steps to harden the working system kernel in opposition to assaults.
The corporate restricted entry to kernel base addresses by limiting features like NtQuerySystemInformation().
This variation meant that solely extremely privileged processes might retrieve this data, successfully neutralizing a typical method utilized by attackers to bypass KASLR and making it a lot tougher to use kernel vulnerabilities.
Nonetheless, evaluation of the October 2024 patch for CVE-2024-43511, a Time-of-check Time-of-use (TOCTOU) race situation vulnerability, revealed a important error.
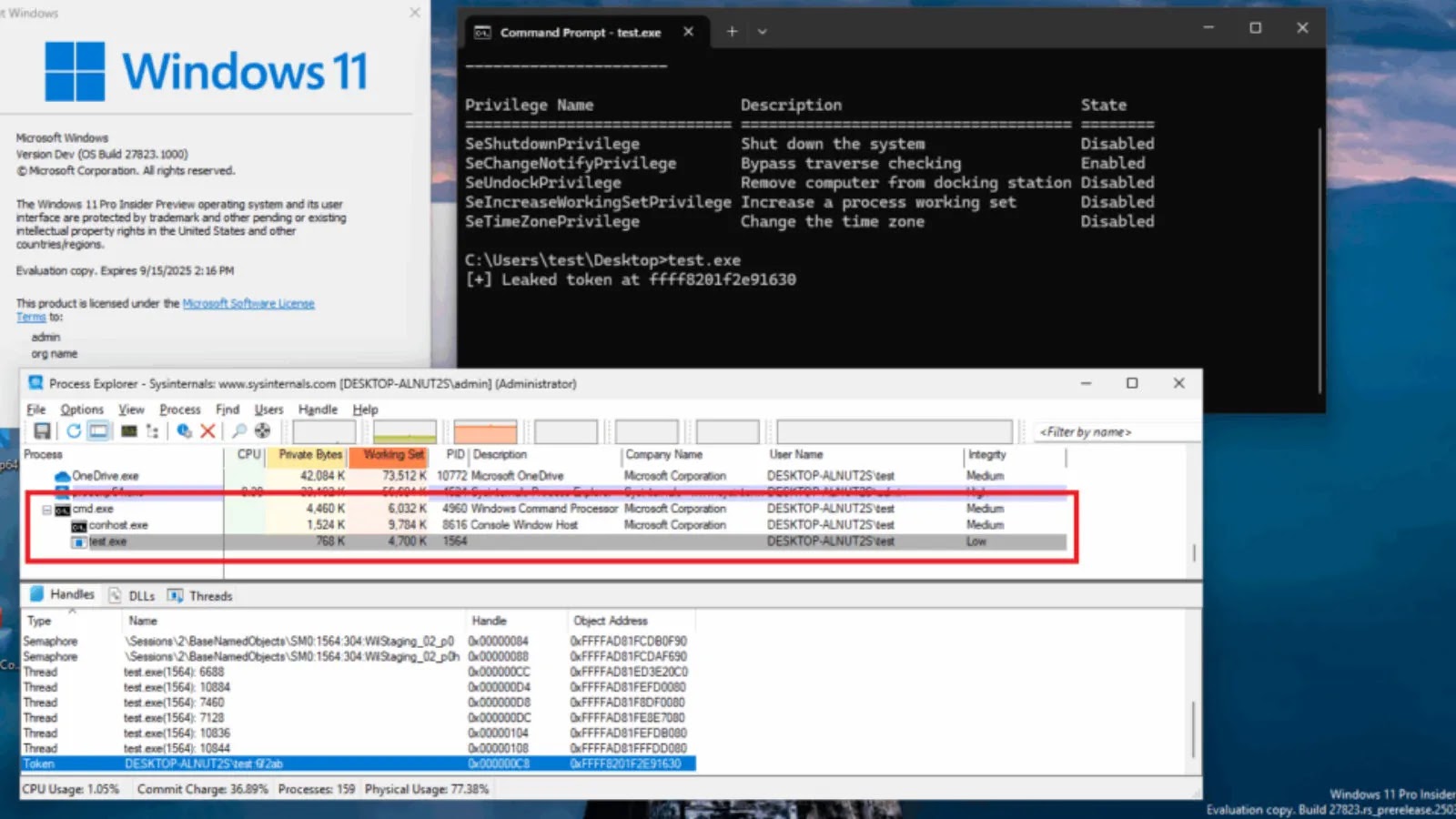
In fixing the unique bug, builders modified the RtlSidHashInitialize() operate. The brand new code briefly writes a delicate kernel pointer from the TOKEN construction right into a user-controlled buffer.
Though the pointer is shortly eliminated, it creates a small however exploitable time window for an attacker to learn it.
Exploiting The Race Situation
An attacker can set off this vulnerability by making a particular system name (NtQueryInformationToken() with the TokenAccessInformation class) whereas concurrently working a separate thread to learn the reminiscence location the place the kernel deal with is briefly leaked.
Regardless of being a race situation, the time window is reportedly vast sufficient to make the exploit extremely dependable. A proof-of-concept demonstrates that the leaked TOKEN deal with might be obtained nearly each time the exploit is run, Crowdfense added.
The impression is important as a result of this leak works on the newest, absolutely patched variations of Home windows 11 and might be executed from low-privilege environments, together with sandboxed AppContainer functions. Whereas the vulnerability itself solely leaks data, it serves as a robust primitive.
When chained with a separate bug, reminiscent of a “write-what-where” situation, an attacker might obtain a full Native Privilege Escalation (LPE) by overwriting the Privileges discipline of the TOKEN object.
This discovery highlights a typical problem in software program safety: fixing one vulnerability can generally inadvertently create one other. The researcher who found the flaw adopted a accountable disclosure course of, which started on April 8, 2025.
After some preliminary confusion the place the report was mistakenly closed as a reproduction, Microsoft finally acknowledged the brand new, legitimate bug on April 25 and assigned it CVE-2025-53136 in August.
Discover this Story Attention-grabbing! Comply with us on Google Information, LinkedIn, and X to Get Extra Instantaneous Updates.