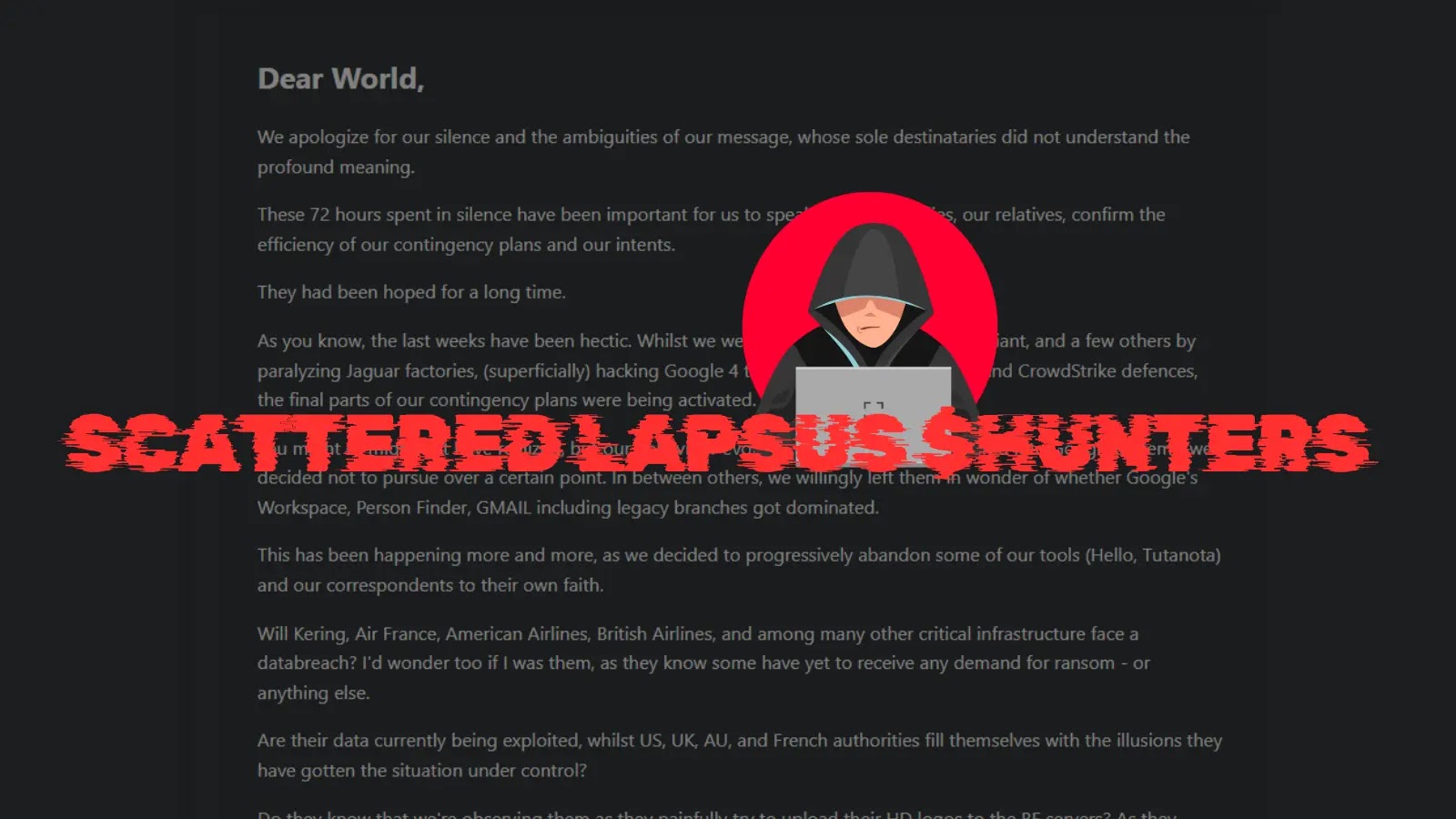
The well-known group of cybercriminals known as Scattered Lapsus$ Hunters launched a shocking farewell assertion on BreachForums.
This manifesto, a mixture of confession and strategic deception, provides very important insights into the altering panorama of contemporary cybercrime and the growing strain from international legislation enforcement companies.
The assertion reveals subtle operational safety practices that reach far past typical cybercriminal conduct.
The group claims their 72-hour silence was intentionally orchestrated to “converse with our households, our family members, and to verify the effectivity of our contingency plans and our intents”.
This calculated strategy demonstrates a stage of strategic planning usually related to nation-state actors relatively than financially motivated cybercriminals.
They describe these spectacular breaches as tactical misdirection designed to “divert the FBI, Mandiant, and some others” whereas their precise contingency plans have been being activated.
This reveals a classy understanding of how legislation enforcement and incident response groups allocate sources, suggesting the group has studied defensive methodologies as fastidiously as assault vectors.
The group’s declare that they “willingly left them in surprise” after penetrating Google’s programs is especially important.
Scattered LAPSUS $Hunters Assertion
Scattered LAPSUS $Hunters Assertion
The restraint proven in Google’s Workspace, Individual Finder, and Gmail legacy branches means that the group could have had extra entry than they revealed however selected to not use it totally. This determination goes in opposition to what’s typical for ransomware teams, which normally attempt to trigger as a lot injury and make as a lot cash as attainable.
Infrastructure Focusing on And Unrealized Threats
Maybe most regarding are the group’s implications relating to crucial infrastructure vulnerabilities.
Their assertion suggests information from corporations together with Kering, Air France, American Airways, and British Airways could also be compromised, with some organizations unaware they face potential exploitation.
This aligns with documented assaults all through 2025, the place Air France and KLM confirmed breaches in August, and a number of aviation sector incidents have been attributed to associated teams.
The group’s query, “Are their information presently being exploited, while US, UK, AU, and French authorities fill themselves with the illusions considering they’ve gotten the state of affairs beneath management?” reveals deep cynicism about worldwide legislation enforcement coordination.
This assertion features explicit significance given the latest arrests and the group’s obvious skill to watch investigative actions, together with their declare of “observing them as they painfully attempt to add their HD logos to the BF servers”.
The assertion immediately addresses the human value of their operations, acknowledging eight arrests linked to Scattered Spider and ShinyHunters operations since April 2024, with 4 people presently in French custody.
These arrests embody the June 2025 detention of 4 alleged ShinyHunters members in France, highlighting the effectiveness of worldwide cooperation between French authorities, the FBI, and different companies.
The group’s expression of remorse “to the 4 who at the moment are in custody in France” and their assertion that investigations will “progressively collapse” suggests they consider the arrested people have been sacrificial.
Their declare to have “manipulated proof to mislead investigators” signifies subtle counterintelligence capabilities designed to guard core operators whereas permitting peripheral members to face authorized penalties.
Collaborations
The emergence of Scattered Lapsus$ Hunters represents an unprecedented consolidation inside cybercrime, combining the techniques of Scattered Spider, Lapsus$, and ShinyHunters.
This merger introduced collectively complementary talent units: Scattered Spider’s social engineering experience, Lapsus$’s brazen publicity techniques, and ShinyHunters’ information theft capabilities.
Their operations all through 2025 demonstrated exceptional technical sophistication, together with OAuth token abuse in Salesforce environments, AI-enhanced voice cloning for vishing assaults, and customized tooling for accelerated information extraction.
The Google Risk Intelligence Group confirmed these actors deployed specialised instruments for Salesforce information extraction whereas concurrently concentrating on a number of organizations by way of social engineering campaigns.
The group’s announcement of retirement must be seen skeptically, given historic precedent. Their assertion that “LAPSUS$, Trihash, Yurosh, Kurosh, Clown, IntelBroker, Scattered Spider, Yukari, and amongst many others” are “going darkish” reads extra like a strategic reorganization than a real cessation of actions.
The timing coincides with unprecedented legislation enforcement strain. The FBI and CISA’s July 2025 advisory warned of Scattered Spider’s “critical and ongoing menace”, whereas coordinated worldwide operations all through 2025 disrupted quite a few cybercrime infrastructures.
The group’s determination to withdraw possible displays recognition that their operational safety has been compromised relatively than real regret.
Cybersecurity Panorama
The Scattered Lapsus$ assertion offers a number of crucial takeaways for cybersecurity professionals and legislation enforcement:
Operational Evolution: Fashionable cybercriminal teams more and more function with nation-state stage sophistication, using strategic deception, counterintelligence, and long-term planning.
Human-Centric Threats: Their success stemmed primarily from social engineering and identity-based assaults relatively than technical exploits, highlighting the continued vulnerability of human components in safety.
Worldwide Coordination Effectiveness: The strain evidenced of their farewell assertion validates the impression of coordinated worldwide legislation enforcement efforts, significantly the Franco-American cooperation that led to a number of arrests.
Infrastructure Vulnerabilities: Their concentrating on of third-party distributors and cloud companies underscores the crucial significance of provide chain safety and OAuth token administration.
The Scattered Lapsus$ farewell represents not the tip of an period, however possible a metamorphosis.
Whereas these particular actors could have withdrawn, their methods, instruments, and tactical improvements will undoubtedly affect the following era of cybercriminal operations.
Their assertion serves as each a warning in regards to the sophistication of contemporary threats and validation that sustained worldwide strain can drive even probably the most brazen actors to rethink their actions.
Discover this Story Attention-grabbing! Comply with us on Google Information, LinkedIn, and X to Get Extra Immediate Updates.