Sep 16, 2025Ravie LakshmananMalware / Social Engineering
Cybersecurity researchers have warned of a brand new marketing campaign that is leveraging a variant of the FileFix social engineering tactic to ship the StealC data stealer malware.
“The noticed marketing campaign makes use of a extremely convincing, multilingual phishing web site (e.g., pretend Fb Safety web page), with anti-analysis strategies and superior obfuscation to evade detection,” Acronis safety researcher Eliad Kimhy stated in a report shared with The Hacker Information.
At a excessive stage, the assault chain includes the usage of FileFix to entice customers into launching an preliminary payload that then proceeds to obtain seemingly innocuous photographs containing the malicious elements from a Bitbucket repository. This permits the attackers to abuse the belief related to a reliable supply code internet hosting platform to bypass detection.
FileFix, first documented by safety researcher mrd0x as a proof-of-concept (PoC) in June 2025, is a little bit completely different from ClickFix in that it eschews the necessity for customers to launch the Home windows Run dialog and paste an already copied obfuscated command to finish bogus CAPTCHA verification checks on phishing pages arrange for this function.
As a substitute, it leverages an internet browser’s file add characteristic to deceive customers into copying and pasting a command on the File Explorer’s tackle bar, inflicting it to be executed domestically on the sufferer’s machine.
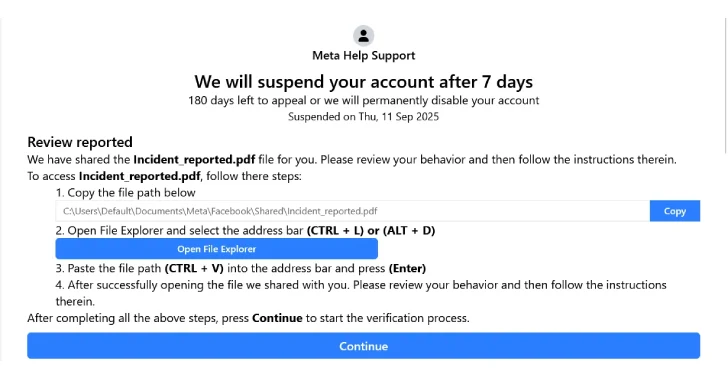
The assault commences with a phishing web site to which the sufferer is probably going redirected from an electronic mail message that warns recipients of potential suspension of their Fb accounts after every week, claiming the shared posts or messages violate its insurance policies. Customers are then requested to attraction the choice by clicking on a button.
The phishing web page will not be solely closely obfuscated, but additionally resorts to strategies like junk code and fragmentation to hinder evaluation efforts.
The FileFix assault comes into play as soon as the button is clicked, at which level the sufferer is displayed a message stating they’ll entry a PDF model of the supposed coverage violation by copying and pasting a path to the doc within the File Explorer’s tackle bar.
Whereas the trail offered within the instruction is totally innocent, a malicious command is surreptitiously copied to the person’s clipboard once they click on on the button within the web page to open File Explorer. This command is a multi-stage PowerShell script that downloads the aforementioned picture, decodes it into the next-stage payload, and finally runs a Go-based loader that unpacks shellcode accountable for launching StealC.
FileFix additionally affords an important benefit over ClickFix, because it abuses a broadly used browser characteristic versus opening the Run dialog (or the Terminal app in case of Apple macOS), which may very well be blocked by a system administrator as a safety measure.
“However, one of many issues that makes ClickFix so difficult to detect within the first place is that it’s spawned from Explorer.exe by way of the run dialog, or instantly from a terminal, whereas with FileFix, the payload is executed by the net browser utilized by the sufferer, which is much extra more likely to stand out in an investigation or to a safety product,” Acronis stated.
“The adversary behind this assault demonstrated important funding in tradecraft, rigorously engineering the phishing infrastructure, payload supply and supporting parts to maximise each evasion and impression.”
The disclosure comes as Doppel detailed one other marketing campaign that has been noticed utilizing a mix of pretend assist portals, Cloudflare CAPTCHA error pages, and clipboard hijacking — i.e., ClickFix — to socially engineer victims into working malicious PowerShell code that downloads and runs an AutoHotkey (AHK) script.
The script is designed to profile the compromised host and ship extra payloads, together with AnyDesk, TeamViewer, data stealers, and clipper malware.
The cybersecurity firm stated it additionally noticed different variants of the exercise the place victims are guided to run an MSHTA command pointing to a lookalike Google area (“wl.google-587262[.]com”), which then retrieves and executes a distant malicious script.
“AHK is a Home windows-based scripting language initially designed for automating repetitive duties like keystrokes and mouse clicks,” Doppel safety researcher Aarsh Jawa famous.
“Whereas it is lengthy been well-liked amongst energy customers and system admins for its simplicity and suppleness, risk actors started weaponizing AHK round 2019 to create light-weight malware droppers and info-stealers. These malicious scripts typically masquerade as benign automation instruments or assist utilities.”