RevengeHotels, a financially motivated risk group energetic since 2015, has escalated its operations in opposition to hospitality organizations by integrating giant language mannequin–generated code into its an infection chain.
Initially recognized for deploying bespoke RAT households reminiscent of RevengeRAT and NanoCoreRAT by way of phishing emails focusing on lodge front-desk programs, the group’s newest campaigns pivot on delivering VenomRAT implants by dynamically generated JavaScript loaders and PowerShell downloaders.
These refined preliminary infectors mimic skilled improvement requirements, embedding detailed feedback and variable placeholders that counsel automated code technology.
A phishing e mail a couple of reserving affirmation (Supply – Securelist)
In current months, operators have particularly focused Brazilian hospitality networks, although Spanish-language lures have expanded the scope to Spanish-speaking markets in Latin America.
Emails masquerading as overdue bill notifications or faux job purposes entice recipients to go to malicious domains, which host scripts named in a rotating “Fats{NUMBER}.js” format—Portuguese for “bill”—to provoke the obtain course of.
Upon execution, the loader decodes an obfuscated buffer and writes a PowerShell file with a timestamped filename, guaranteeing every pattern stays distinctive and evades signature-based detections.
Securelist analysts famous that these rotating filenames and the coherence of the generated code mark a departure from the group’s prior handbook obfuscation efforts.
As soon as the PowerShell stub executes, it retrieves two Base64-encoded payloads—venumentrada.txt and runpe.txt—from distant servers.
The primary file serves as a light-weight loader, whereas the second executes the VenomRAT payload straight in reminiscence.
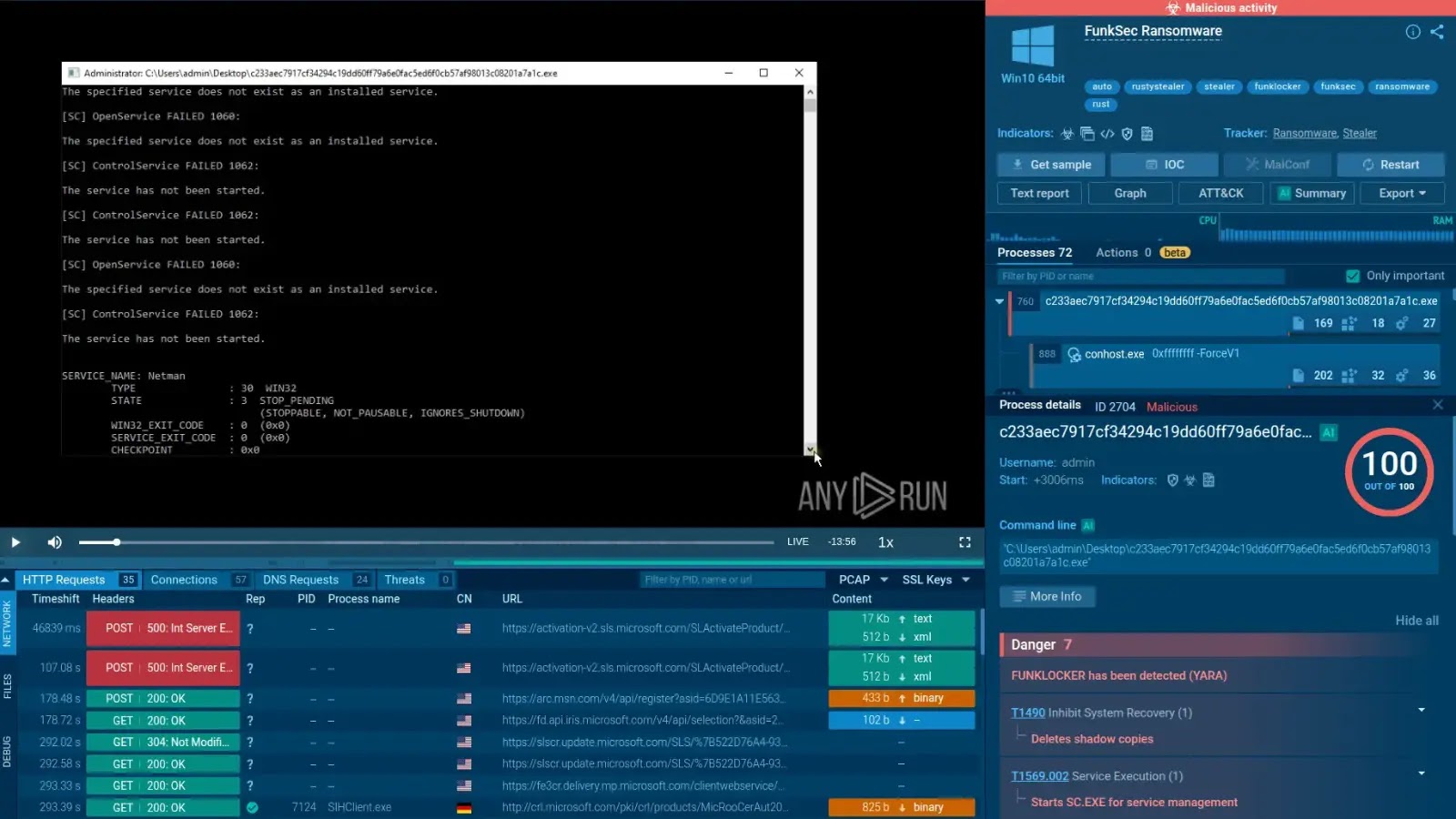
Securelist researchers recognized that the loader employs a easy deobfuscation routine, as proven in Determine 1, to decode and invoke the implant with out ever writing the ultimate executable to disk.
AI generated code in a malicious implant as in comparison with customized code (Supply – Securelist)
The VenomRAT implant itself builds upon the open-source QuasarRAT codebase, augmenting it with hidden desktop (HVNC), file-stealing modules, and UAC bypass primitives.
Configuration information is encrypted with AES-CBC and authenticated by way of HMAC-SHA256, utilizing distinct keys for decryption and integrity verification.
Networking routines serialize action-specific packets, compress them with LZMA, and encrypt with AES-128 earlier than transmission to the command-and-control server.
VenomRAT packages on the darkish internet (Supply – Securelist)
Notably, VenomRAT integrates ngrok-based tunneling to reveal RDP and VNC companies, enhancing distant entry capabilities even by NAT or firewall constraints.
An infection Mechanism
The an infection chain’s success hinges on the preliminary JavaScript loader’s capacity to orchestrate multi-stage payload supply whereas mixing AI-generated readability with handbook obfuscation.
After the phishing e mail’s person clicks the malicious hyperlink, the sufferer’s browser fetches a WScript JS file—Fat146571.js—which instantly decodes an embedded blob:-
var decoded = atob(“SGDoHBZQWpL…”);
// Write decoded PowerShell to disk
var fso = new ActiveXObject(“Scripting.FileSystemObject”);
var ps1 = fso.CreateTextFile(“SGDoHBZQWpLKXCAoTHXdBGlnQJLZCGBOVGLH_” + Date.now() + “.ps1”, true);
ps1.WriteLine(decoded);
ps1.Shut();
// Execute the PowerShell script silently
WScript.CreateObject(“WScript.Shell”).Run(“powershell -ExecutionPolicy Bypass -File ” + ps1.Identify, 0, false);
This section exemplifies the AI’s function in producing clear, maintainable code that nonetheless performs malicious actions.
By producing distinctive filenames based mostly on timestamps and avoiding persistent artifacts, the loader evades standard antivirus and forensic instruments.
The three-phase execution—decode, write, and execute—ensures that every an infection occasion differs, complicating detection signature updates.
By means of this mix of AI-driven scripting and superior RAT capabilities, RevengeHotels continues to refine its arsenal in opposition to Home windows environments, posing a rising problem to cybersecurity defenders.
Free reside webinar on new malware techniques from our analysts! Study superior detection methods -> Register for Free