Microsoft’s Digital Crimes Unit stated it teamed up with Cloudflare to coordinate the seizure of 338 domains utilized by RaccoonO365, a financially motivated risk group that was behind a phishing-as-a-service (Phaas) toolkit used to steal greater than 5,000 Microsoft 365 credentials from 94 nations since July 2024.
“Utilizing a courtroom order granted by the Southern District of New York, the DCU seized 338 web sites related to the favored service, disrupting the operation’s technical infrastructure and slicing off criminals’ entry to victims,” Steven Masada, assistant basic counsel at DCU, stated.
“This case exhibits that cybercriminals do not must be refined to trigger widespread hurt – easy instruments like RaccoonO365 make cybercrime accessible to just about anybody, placing thousands and thousands of customers in danger.”
The preliminary part of the Cloudflare takedown commenced on September 2, 2025, with extra actions occurring on September 3 and September 4. This included banning all recognized domains, putting interstitial “phish warning” pages in entrance of them, terminating the related Employees scripts, and suspending the consumer accounts. The efforts have been accomplished on September 8.
Tracked by the Home windows maker beneath the identify Storm-2246, RaccoonO365 is marketed to different cybercriminals beneath a subscription mannequin, permitting them to mount phishing and credential harvesting assaults at scale with little to no technical experience. A 30-day plan prices $355, and a 90-day plan is priced at $999.
The operators additionally declare that the software is hosted on bulletproof digital non-public servers with no hidden backdoors (in contrast to, say, BulletProofLink), and that it is “constructed for severe gamers solely – no low-budget freeloaders.”
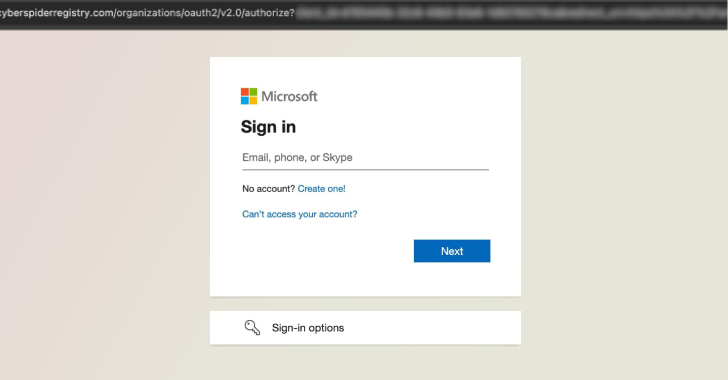
Based on Morado, campaigns utilizing RaccoonO365 have been energetic since September 2024. These assaults sometimes mimic trusted manufacturers like Microsoft, DocuSign, SharePoint, Adobe, and Maersk in fraudulent emails, tricking them into clicking on lookalike pages which can be designed to seize victims’ Microsoft 365 usernames and passwords. The phishing emails are sometimes a precursor to malware and ransomware.
Probably the most troubling facet, from a defender’s standpoint, is using reliable instruments like Cloudflare Turnstile as a CAPTCHA, in addition to implementing bot and automation detection utilizing a Cloudflare Employees script to guard their phishing pages, thereby ensuring that solely supposed targets of the assault can entry and work together with them.
Earlier this April, the Redmond-based firm warned of a number of phishing campaigns leveraging tax-related themes to deploy malware corresponding to Latrodectus, AHKBot, GuLoader, and BruteRatel C4 (BRc4). The phishing pages, it added, have been delivered by way of RaccoonO365, with one such marketing campaign attributed to an preliminary entry dealer referred to as Storm-0249.
The phishing campaigns have focused over 2,300 organizations in the US, together with not less than 20 U.S. healthcare entities.
“Utilizing RaccoonO365’s companies, clients can enter as much as 9,000 goal e mail addresses per day and make use of refined strategies to avoid multi-factor authentication protections to steal consumer credentials and acquire persistent entry to victims’ programs,” Microsoft stated.
“Most not too long ago, the group began promoting a brand new AI-powered service, RaccoonO365 AI-MailCheck, designed to scale operations and enhance the sophistication – and effectiveness – of assaults.”
The mastermind behind RaccoonO365 is assessed to be Joshua Ogundipe, a person primarily based in Nigeria, who, alongside along with his associates, has marketed the software on an 850-member sturdy Telegram channel, receiving at least $100,000 in cryptocurrency funds. The e-crime group is believed to have offered about 100-200 subscriptions, though Microsoft cautioned it is probably an underestimate.
The tech big stated it was capable of make the attribution courtesy of an operational safety lapse that inadvertently uncovered a secret cryptocurrency pockets. Ogundipe and 4 different co-conspirators at present stay at massive, however Microsoft famous {that a} felony referral for Ogundipe has been despatched to worldwide legislation enforcement.
Cloudflare, in its personal evaluation of the PhaaS service, stated the takedown of lots of of domains and Employee accounts is geared toward rising operational prices and sending a warning to different malicious actors who might abuse its infrastructure for malicious functions.
For the reason that disruption, the risk actors have introduced that they’re “scrapping all legacy RaccoonO365 hyperlinks,” urging their clients who paid for a 1-month subscription to change to a brand new plan. The group additionally stated it should compensate these affected by providing “one further week of subscription” following the improve.
The “response represents a strategic shift from reactive, single-domain takedowns to a proactive, large-scale disruption geared toward dismantling the actor’s operational infrastructure on our platform,” Cloudflare stated.