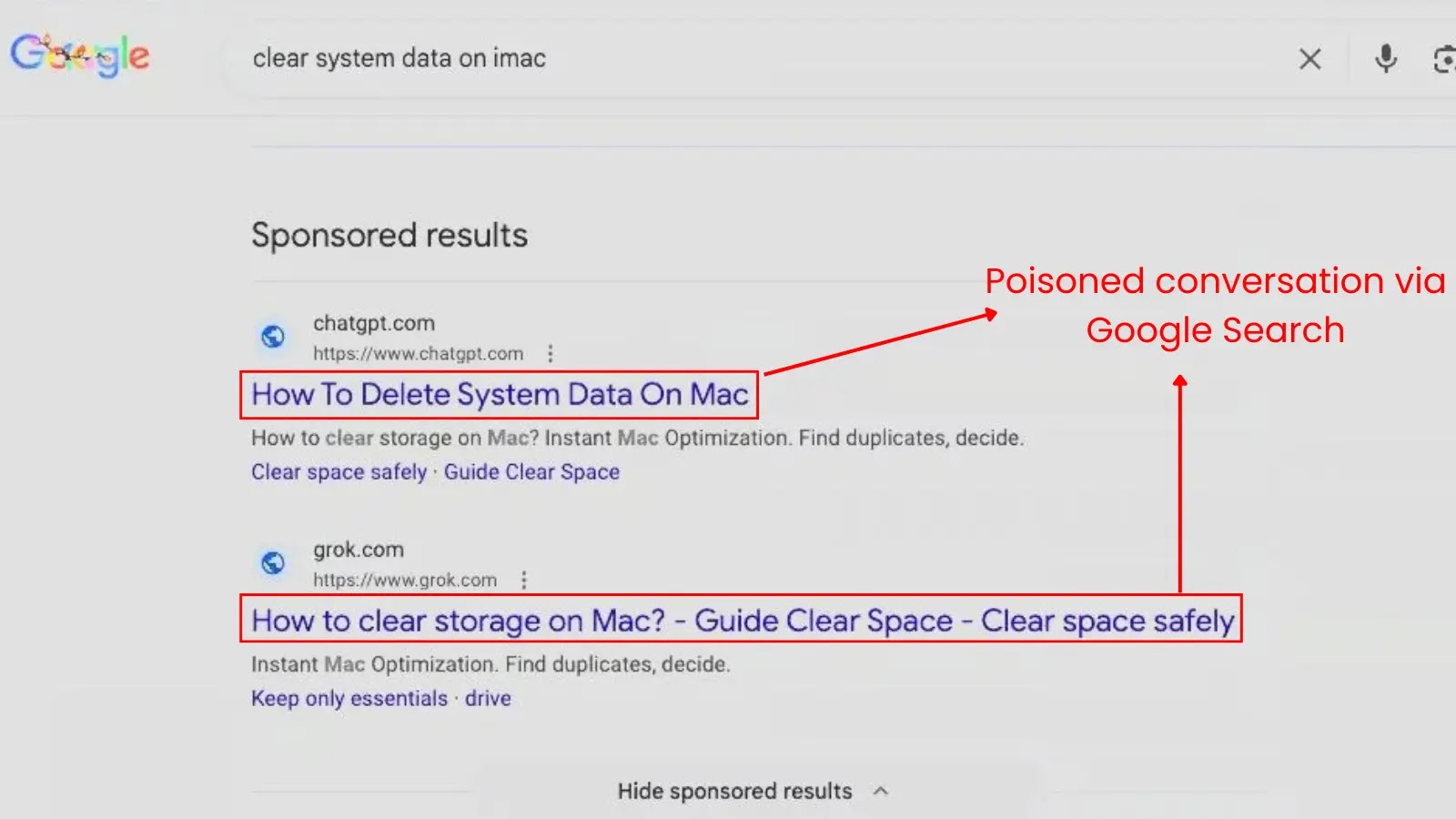
The digital promoting ecosystem has change into a major looking floor for cybercriminals, who’re more and more exploiting promoting know-how corporations to distribute malware and conduct malicious campaigns.
Fairly than merely abusing legit platforms, risk actors at the moment are working because the platforms themselves, creating a classy net of deception that leverages the inherent complexity and fragmentation of the adtech provide chain to keep away from accountability.
Latest investigations have uncovered a large operation involving Vane Viper, a risk actor that has appeared in roughly half of buyer networks monitored by safety researchers, producing about one trillion DNS queries over the previous 12 months.
This operation advantages from a whole lot of 1000’s of compromised web sites and strategically positioned commercials throughout gaming, procuring, and weblog websites worldwide.
The actor’s infrastructure spans roughly 60,000 domains, representing solely a fraction of the broader malicious ecosystem they management.
The sophistication of this marketing campaign lies in its rigorously constructed company construction designed for believable deniability.
Company filings hint Vane Viper to AdTech Holding, a Cyprus-based firm whose flagship subsidiary, PropellerAds, operates as each an promoting community and site visitors dealer.
Key firm relationships (Supply – Infoblox)
Infoblox researchers recognized compelling proof suggesting that PropellerAds has moved past merely turning a blind eye to prison abuse of their platform, with indicators pointing to a number of ad-fraud campaigns originating immediately from infrastructure attributed to the corporate.
The malvertising operation employs a fancy site visitors distribution system (TDS) that routes customers by means of a number of layers of redirection earlier than delivering malicious payloads.
This strategy permits the actors to serve legit content material to automated safety instruments whereas directing human customers to malicious locations.
The marketing campaign’s attain extends past conventional malware distribution, encompassing faux procuring websites, fraudulent browser extensions, survey scams, and grownup content material designed to maximise revenue from compromised site visitors.
Push Notification Persistence Mechanism
Probably the most insidious side of Vane Viper’s operation includes the abuse of browser push notifications to realize persistent entry to sufferer units.
The marketing campaign makes use of malicious service staff, JavaScript recordsdata that intercept community requests between net purposes and servers, to control browser conduct and preserve long-term entry to compromised programs.
PropellerAds displaying the place they sit within the digital promoting ecosystem (Supply – Infoblox)
These service staff make use of script chaining strategies to abuse push notifications, with probably the most regarding factor being their use of the eval() operate to execute arbitrary content material fetched from distant URLs.
The distant URL is decided by hardcoded domains inside the service employee, making a dynamic command and management mechanism that may adapt to altering operational necessities.
As soon as customers settle for push notifications, their units change into a part of a persistent malvertising community, enabling a steady stream of malicious commercials.
The operation demonstrates outstanding resilience by means of its area administration technique, biking by means of 1000’s of newly registered domains every month whereas sustaining key push notification domains for years.
Evaluation reveals that almost all operational domains stay energetic for lower than a month, with registration counts reaching 3,500 domains in peak months, whereas core infrastructure domains like omnatuor.com, propeller-tracking.com, and numerous push notification providers together with in-page-push.com and pushimg.com have maintained operations for over 1,200 days, making certain operational continuity regardless of takedown makes an attempt.
Free reside webinar on new malware ways from our analysts! Be taught superior detection strategies -> Register for Free