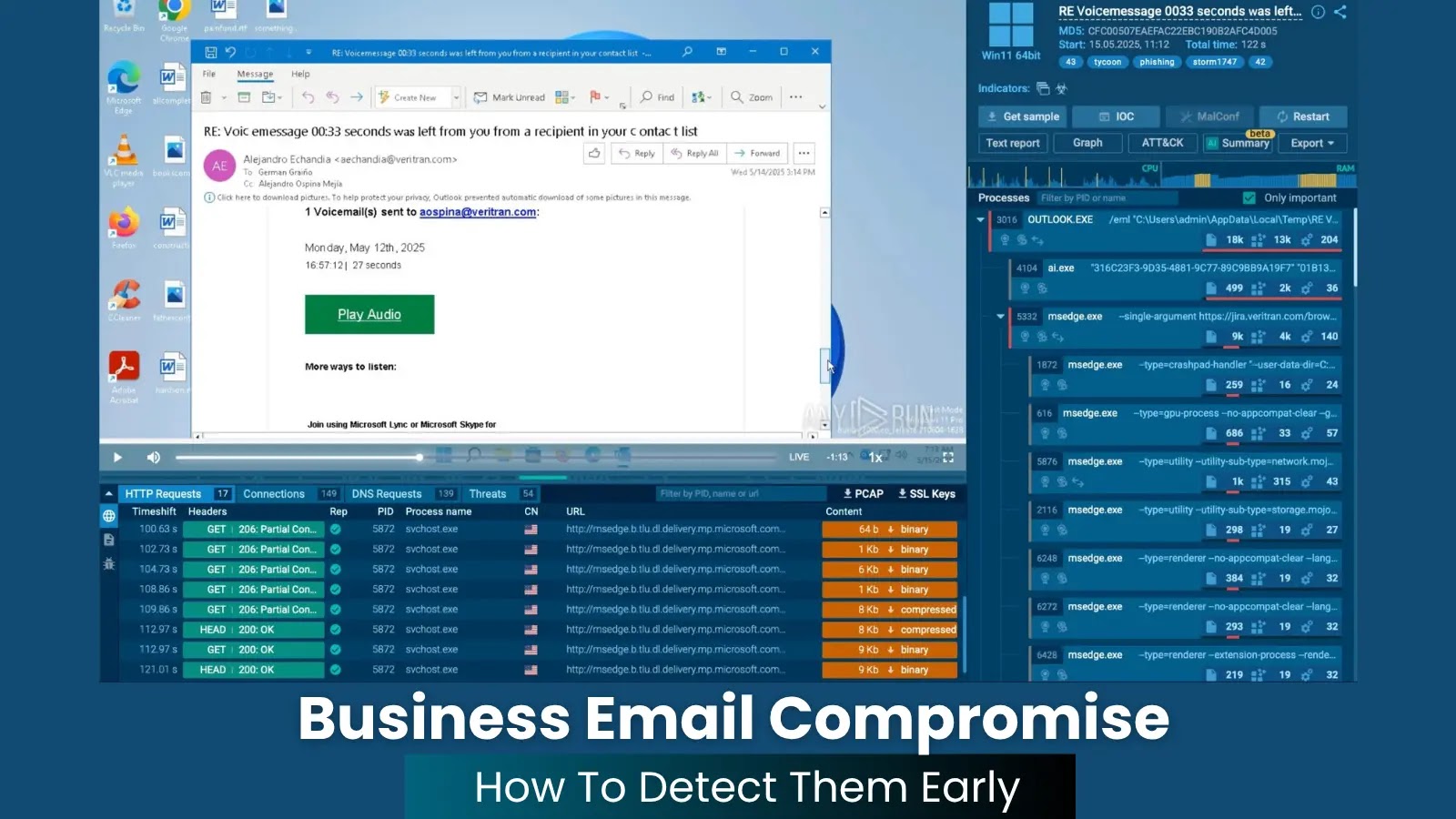
As organizations more and more undertake multi-cloud environments to leverage flexibility, scalability, and cost-efficiency, securing these advanced infrastructures has grow to be a high precedence.
By 2025, 99% of cloud safety failures will stem from buyer misconfigurations or oversights, underscoring the pressing want for sturdy protection mechanisms.
With 80% of organizations experiencing no less than one cloud safety incident previously yr, and 82% of breaches involving cloud-stored knowledge, the stakes have by no means been increased.
This text explores the evolving challenges of multi-cloud safety and descriptions actionable methods to mitigate dangers in an period of decentralized digital ecosystems.
The Increasing Assault Floor of Multi-Cloud Environments
Multi-cloud architectures, whereas advantageous, introduce fragmented visibility and inconsistent safety controls.
Every cloud provider-whether AWS, Azure, or Google Cloud-operates with distinct APIs, compliance frameworks, and id administration techniques, creating silos that complicate oversight.
As an example, AWS helps over 15,000 IAM actions, whereas Azure provides almost 19,000, making uniform coverage enforcement nearly unattainable with out specialised instruments.
For instance, a storage bucket left publicly accessible in AWS would possibly adjust to inside insurance policies however violate compliance requirements if replicated with out changes in Azure.
Legacy monitoring instruments typically fail to offer unified insights throughout clouds, leaving safety groups unaware of vulnerabilities like over-permissioned service accounts or unpatched digital machines.
Misconfigurations stay the main reason behind cloud breaches, accounting for 88% of incidents. In multi-cloud setups, the danger escalates as groups juggle divergent settings for storage permissions, community entry, and encryption throughout platforms.
A 2024 survey discovered 82% of organizations lack ample visibility into their multi-cloud environments, delaying menace detection and response.
Managing identities throughout clouds amplifies dangers, as attackers more and more exploit poorly configured roles or stale credentials. Whereas Zero Belief frameworks advocate for least-privilege entry, inconsistent IAM insurance policies between suppliers typically go away gaps.
For instance, a developer granted broad permissions in GCP for testing would possibly inadvertently retain these privileges when accessing Azure sources, creating lateral motion alternatives for attackers.
Navigating GDPR, HIPAA, and PCI-DSS necessities throughout jurisdictions turns into daunting when knowledge resides in a number of clouds. Encryption requirements and audit trails differ by supplier, complicating compliance reporting.
A healthcare group utilizing AWS within the U.S. and Azure within the EU, as an illustration, should guarantee each platforms meet region-specific knowledge safety laws- a job requiring steady validation.
Constructing a Resilient Multi-Cloud Safety Posture
Undertake Cloud Safety Posture Administration (CSPM) ToolsCSPM options like Prowler automate misconfiguration detection and compliance checks throughout clouds. By integrating with AWS, Azure, GCP, and Kubernetes APIs, these instruments present real-time alerts for points reminiscent of uncovered storage nodes or non-compliant encryption settings.
For instance, Prowler’s open-source platform scans 50,000+ sources hourly, figuring out dangers like unsecured S3 buckets or overly permissive firewall guidelines.
Zero Belief rules, reminiscent of micro-segmentation and steady authentication, restrict lateral motion. As an example, AccuKnox’s Zero Belief CNAPP enforces role-based entry controls (RBAC) and multi-factor authentication (MFA) throughout clouds, guaranteeing {that a} compromised Azure account doesn’t grant entry to AWS workloads.
IaC instruments like Terraform standardize safety configurations, decreasing human error. Groups can outline encryption requirements, community insurance policies, and IAM roles in reusable templates, guaranteeing consistency when deploying sources throughout clouds
Encrypting knowledge at relaxation and in transit is non-negotiable. Centralized key administration techniques allow uniform encryption insurance policies, reminiscent of AWS KMS or Azure Key Vault. TLS 1.3 and quantum-resistant algorithms have gotten trade norms for cross-cloud knowledge transfers.
AI-driven platforms like SentinelOne’s Singularity Cloud analyze logs from a number of suppliers to detect anomalies, reminiscent of uncommon API calls or knowledge exfiltration patterns. Machine studying fashions educated on multi-cloud datasets can establish zero-day exploits 60% quicker than conventional strategies.
The Way forward for Multi-Cloud Safety
Gartner predicts that 40% of enterprises will deploy AI-powered cloud safety instruments to remediate threats autonomously by 2026.
Rising applied sciences like confidential computing, encrypting knowledge throughout processing, and blockchain-based audit trails will additional harden multi-cloud environments.
In the meantime, regulatory pressures drive adoption of unified frameworks like ISO 27001:2025, which mandates cross-cloud threat assessments.
As multi-cloud adoption accelerates, organizations should abandon fragmented safety methods in favor of holistic, automated approaches.
Companies can remodel their cloud ecosystems from vulnerabilities into belongings by integrating CSPM instruments, Zero Belief rules, and AI-driven analytics.
The trail ahead calls for collaboration between DevOps, SecOps, and compliance groups to make sure that agility by no means comes at the price of resilience. Within the multi-cloud period, safety isn’t only a technical problem; it’s a aggressive crucial.
Discover this Information Attention-grabbing! Comply with us on Google Information, LinkedIn, & X to Get Immediate Updates!