The emergence of a brand new marketing campaign weaponizing official distant monitoring and administration software program has alarmed safety groups worldwide.
Attackers are distributing trojanized installers for ConnectWise ScreenConnect—now often called ConnectWise Management—to ship twin payloads: the broadly used AsyncRAT and a customized PowerShell-based RAT.
By leveraging trusted software program footprints and open directories, adversaries bypass signature-based defenses and preserve long-term entry to compromised networks.
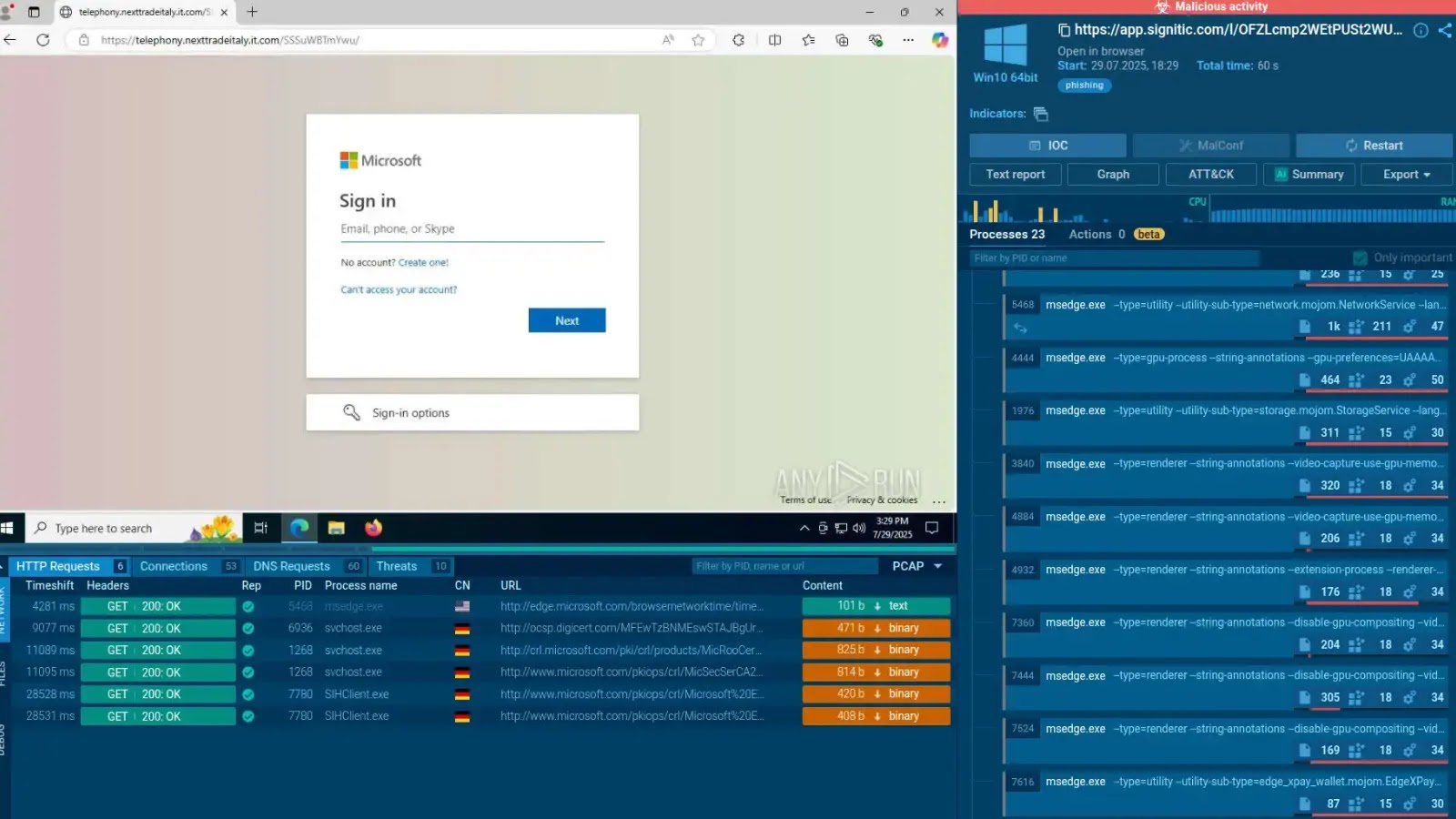
Preliminary incidents surfaced in Could 2025, when analysts noticed anomalous ScreenConnect installers hosted on uncovered file servers.
These installers contained ClickOnce loaders that, upon execution, fetched malicious elements at runtime slightly than embedding payloads straight.
In a single occasion, a compromised installer silently launched a VBS script that executed a weaponized shortcut, triggering PowerShell with execution-policy bypass to run a loader script.
Hunt.io Cyber Crew researchers recognized this tactic after correlating telemetry from a number of uncovered hosts and correlating IOCs throughout open directories.
Assault chain (Supply – Hunt.io)
Subsequent evaluation revealed a repeatable infrastructure sample. Contaminated installers pivoted to repositories internet hosting .zip archives named logs.ldk, logs.idk, and logs.idr, which unpacked into dropper scripts (Ab.vbs or Ab.js), the PowerShell loader (Skype.ps1), a local injector DLL (libPK.dll), and a shortcut file (Microsoft.lnk).
The VBS launcher makes use of WScript.Shell to invoke the shortcut, which in flip runs PowerShell with hidden home windows to launch Skype.ps1.
This script reconstructs an embedded payload blob, invokes the DLL’s exported Execute operate for in-memory native staging, and creates a scheduled job named SystemInstallTask for persistence.
An infection Mechanism
The an infection chain begins with a seemingly benign ScreenConnect consumer installer.
As soon as executed, it drops the VBS loader (Ab.vbs) right into a public folder and registers a Home windows shortcut. The shortcut’s goal is crafted to launch PowerShell with -ExecutionPolicy Bypass -WindowStyle Hidden, calling a small script file named Skype.ps1.
Skype.ps1 accommodates base64-encoded payload segments that it decodes right into a .NET meeting or native shellcode, relying on detected safety merchandise.
If the script detects antivirus like TotalAV or Avast, it performs in-memory meeting loading by way of System.Reflection.Meeting.Load; in any other case it dynamically imports libPK.dll utilizing PowerShell’s Add-Sort and calls Execute to inject payloads into official host processes.
To take care of resilience, the loader additionally schedules recurring duties (each 2–10 minutes) making certain speedy re-execution if terminated.
Moreover, using open directories for preliminary staging permits attackers to rotate information and domains steadily, complicating detection.
The mixture of modular scripts, scheduled duties, and twin execution paths exemplifies a classy multi-stage supply framework that blends official RMM software program abuse with bespoke RAT payloads.
Discover this Story Fascinating! Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates.