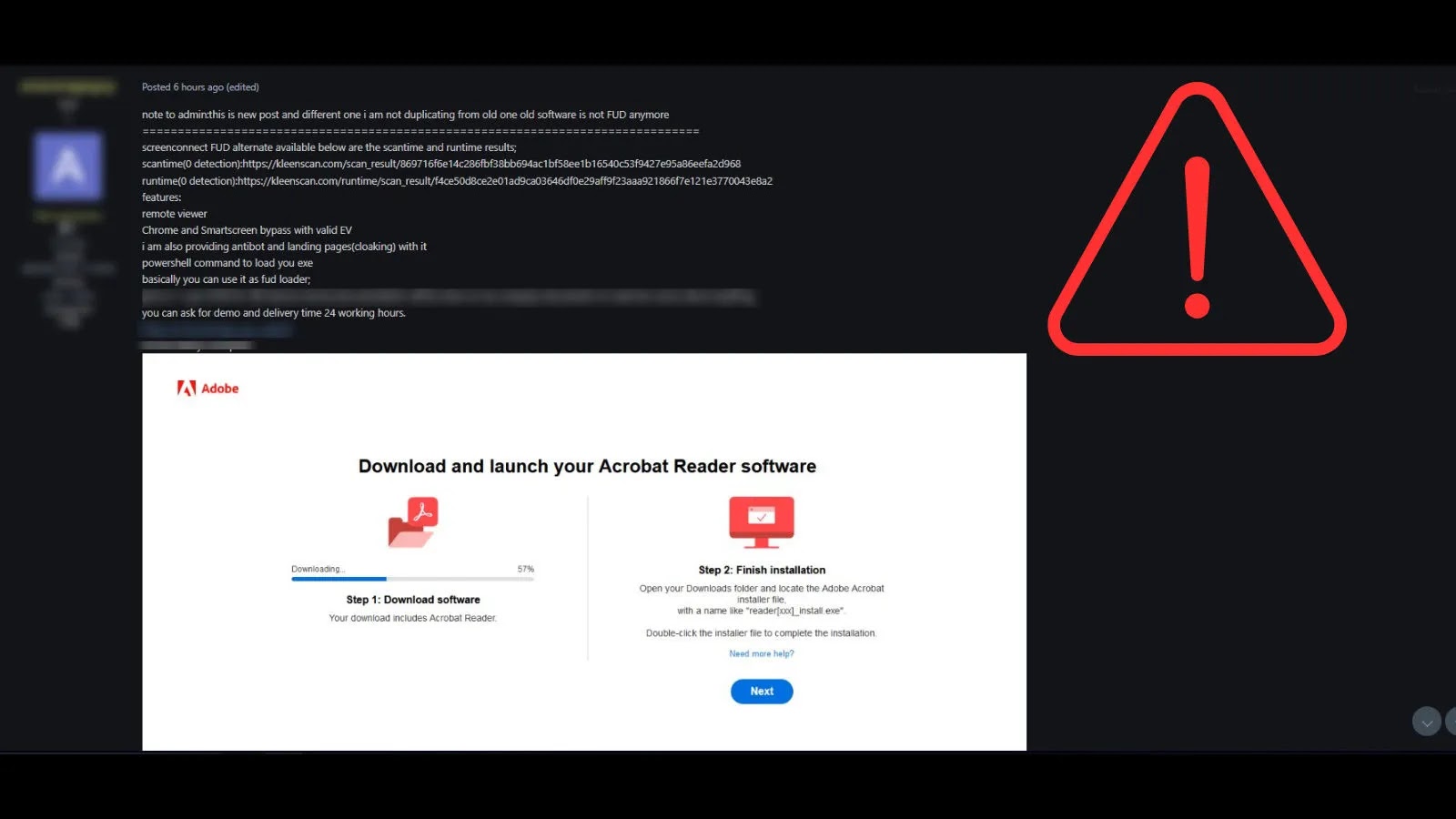
A menace actor has been noticed promoting a brand new Distant Entry Trojan (RAT) on underground boards, advertising and marketing it as a totally undetectable (FUD) different to the authentic distant entry software, ScreenConnect.
The malware is being offered with a set of superior options designed to bypass trendy safety defenses, signaling a rising pattern in subtle, ready-to-use cybercrime instruments.
The vendor claims the software achieves zero detections throughout each static and runtime evaluation, making it a potent menace for preliminary entry and payload supply operations.
This growth underscores the continuing efforts by malicious actors to take advantage of belief and evade detection by mimicking authentic software program and processes.
Bypassing Safety With Superior Evasion
The first promoting level of this new RAT is its skill to bypass safety warnings from each Google Chrome and Home windows SmartScreen.
FUD Malware Declare
The menace actor claims that is achieved by bundling the malware with a sound Prolonged Validation (EV) certificates.
EV certificates are a high-assurance digital identification commonplace that usually causes browsers to show a inexperienced bar or the corporate’s identify, instilling a false sense of safety within the sufferer.
The bundle additionally contains antibot mechanisms and cloaked touchdown pages. These options enable the malware to current benign content material to safety scanners and sandboxes whereas delivering the malicious payload to real targets, a standard tactic for evading automated evaluation.
The offered commercial showcases a convincing however fraudulent Adobe Acrobat Reader obtain web page, demonstrating a typical social engineering scheme for supply.
Based on the vendor’s submit, the RAT is supplied with a distant viewer, granting the attacker direct visible management over a compromised machine’s desktop.
This functionality permits for real-time monitoring, information exfiltration, and interactive system manipulation. Moreover, the software makes use of a PowerShell-based command to load its executable. This fileless method helps it stay hidden from conventional antivirus options that primarily give attention to scanning information on disk.
The actor explicitly states the software can be utilized as a “FUD loader,” indicating its main operate could also be to ascertain a persistent and stealthy foothold on a goal system earlier than deploying secondary payloads, comparable to ransomware, spy ware, or banking trojans.
The vendor gives a demo and guarantees supply inside 24 working hours, suggesting an expert and operationalized service.
Discover this Story Fascinating! Comply with us on Google Information, LinkedIn, and X to Get Extra On the spot Updates.