Large corporations are getting smaller, and their CEOs need everybody to comprehend it. Wells Fargo has reduce its workforce by 23% over 5 years, Financial institution of America has shed 88,000 workers since 2010, and Verizon’s CEO just lately boasted that headcount is “happening on a regular basis.” What was as soon as an indication of company misery has change into a badge of honor, with executives celebrating lean operations and AI-driven effectivity.
However whereas C-suite leaders tout “doing extra with much less,” CISOs are left with fewer assets, whereas each preventable safety incident turns into exponentially costlier. With safety groups already stretched skinny and developer-to-security ratios reaching unsustainable ranges, these workforce reductions push already distressed groups previous their breaking level. Towards this backdrop of workforce optimization, hardcoded secrets and techniques signify a very harmful blind spot that may not be managed by handbook processes and reactive firefighting.
The Numbers Do not Lie
The credential disaster is already right here. In accordance with IBM’s newest analysis, 86% of breaches contain stolen or compromised credentials, with the common time to establish and comprise these incidents stretching to a staggering 292 days.
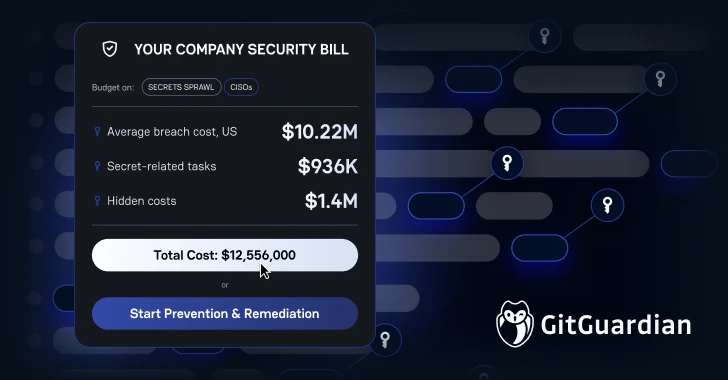
The monetary stakes have by no means been larger. In the USA, breach prices surged to an all-time excessive of $10.22 million, pushed by larger regulatory fines and detection prices. For credential-based incidents particularly, HashiCorp’s analysis exhibits these breaches carry a $750,000 premium, that means US organizations face potential prices exceeding $11 million when hardcoded secrets and techniques are concerned.
However the hidden prices could also be much more devastating. Organizations waste almost $1.4 million yearly on managing secrets and techniques manually. This consists of developer time spent on credential rotation and publicity investigation ($936,000) and safety analysts triaging false positives and chasing down leaked credentials (>$500,000).
The actual-world impression is already seen. Canva skilled days of downtime throughout a number of groups as a consequence of a single leaked secret, consuming engineering assets that ought to have been centered on product improvement.
Why Lean Groups Amplify the Danger
Workforce reductions imply longer mean-time-to-remediate incidents, and the 292-day common containment window turns into much more harmful. Every safety incident pulls already-stretched groups away from core enterprise features, creating expensive context-switching overhead that lean organizations cannot afford.
The scope of the issue continues increasing whilst groups shrink. Massive organizations harbor 1000’s of unmanaged secrets and techniques scattered throughout code repositories, CI/CD pipelines, Slack channels, Jira tickets, and collaboration platforms.
HashiCorp’s analysis signifies that as much as 40% of those secrets and techniques fall into high-risk classes, usually offering direct manufacturing entry.
This creates a multiplication impact: one hardcoded API key can allow lateral motion, provide chain compromise, and large-scale ransomware deployment. The current s1ngularity assault demonstrates this completely: what started as a GitHub Motion token-stealing pull request compromised Nx packages, stealing 2,349 credentials, and cascaded into attackers exposing 82,901 further secrets and techniques by making over 10,000 personal repositories public.
The Strategic Response: Precision Over Quantity
GitGuardian’s strategy to secrets and techniques safety acknowledges a basic reality: detection alone is not sufficient. With out efficient remediation, alerts change into costly noise that overwhelms already-stretched groups. For CISOs managing learner safety operations, this distinction is vital.
Secrets and techniques current a basically totally different problem than conventional vulnerabilities. Whereas a developer can usually patch a code vulnerability independently, remediating uncovered secrets and techniques requires understanding the broader infrastructure context—the place the key is used throughout a number of providers, which techniques rely on it, and who has the authority to rotate it. This usually calls for coordination between improvement, platform, and DevOps groups, every with its personal priorities and workflows. Gathering this context manually turns into prohibitively costly when safety groups are already working at capability, turning what needs to be fast fixes into complicated, multi-team investigations that may stretch for weeks.
Superior platforms now shift focus from “What’s uncovered?” to “What’s the magnitude of publicity?” by offering contextual data, together with roles, permissions, possession, and risk scope. This holistic strategy instantly addresses the false optimistic burden that prices organizations over $500,000 yearly in wasted analyst time.
Reducing Remediation Time from Weeks to Hours
Efficient remediation frameworks align completely with lean workforce constraints:
Proactive Detection: Platforms that implement each preventive scanning throughout commits and reactive scanning for present leaks catch points earlier than they attain the 292-day common containment window.
Clear Possession: As an alternative of broadcasting obscure alerts, trendy instruments assign possession for each secret, making certain accountable builders obtain notifications with full context. This eliminates time waste looking down secret house owners.
Knowledgeable Choice Making: Groups obtain exact location knowledge, perceive what every secret unlocks, and know whether or not it is nonetheless energetic. In accordance with the Hashicorp analysis talked about above, this focused strategy prevents the $936,000 annual productiveness drain from handbook investigation duties.
Workflow Integration: Builders get clear remediation steerage instantly inside their present instruments, decreasing the context switching prices that plague smaller groups. Superior platforms now supply automated secret revocation capabilities and might generate code-fixing pull requests instantly inside model management techniques, assembly builders precisely the place they work fairly than forcing them into separate safety instruments.
The ROI of Good Remediation
By pinpointing particular recordsdata and features of code the place secrets and techniques are hardcoded, GitGuardian’s strategy transforms the economics of incident response. As an alternative of builders spending hours looking out codebases, they focus their efforts precisely the place wanted. Actual-time remediation monitoring gives safety groups with visibility with out handbook oversight.
This precision strategy instantly tackles the core problem going through downsized safety groups: doing extra with much less whereas sustaining safety posture.
Discovered this text fascinating? This text is a contributed piece from certainly one of our valued companions. Comply with us on Google Information, Twitter and LinkedIn to learn extra unique content material we publish.