MCP has turn into an integral a part of the enlargement of agentic AI however comes with its personal vulnerabilities.
Mannequin Context Protocol (MCP), developed by Anthropic and launched as an open customary in 2024, is the de facto (not absolute) customary methodology of making certain a constant and secure interface between an AI agent (or brokers) and the info supply (or sources). It specifies how AI brokers work together with instruments, different brokers, knowledge, and context in a secure and auditable method every time required. It’s consequently a basic requirement for efficient Agentic AI.
However like all software program, MCP has areas that may be abused by malicious actors. This month a possible assault on ChatGPT’s calendar integration was described, permitting an e mail calendar invite to ship a jailbreak to ChatGPT, with no person interplay required.
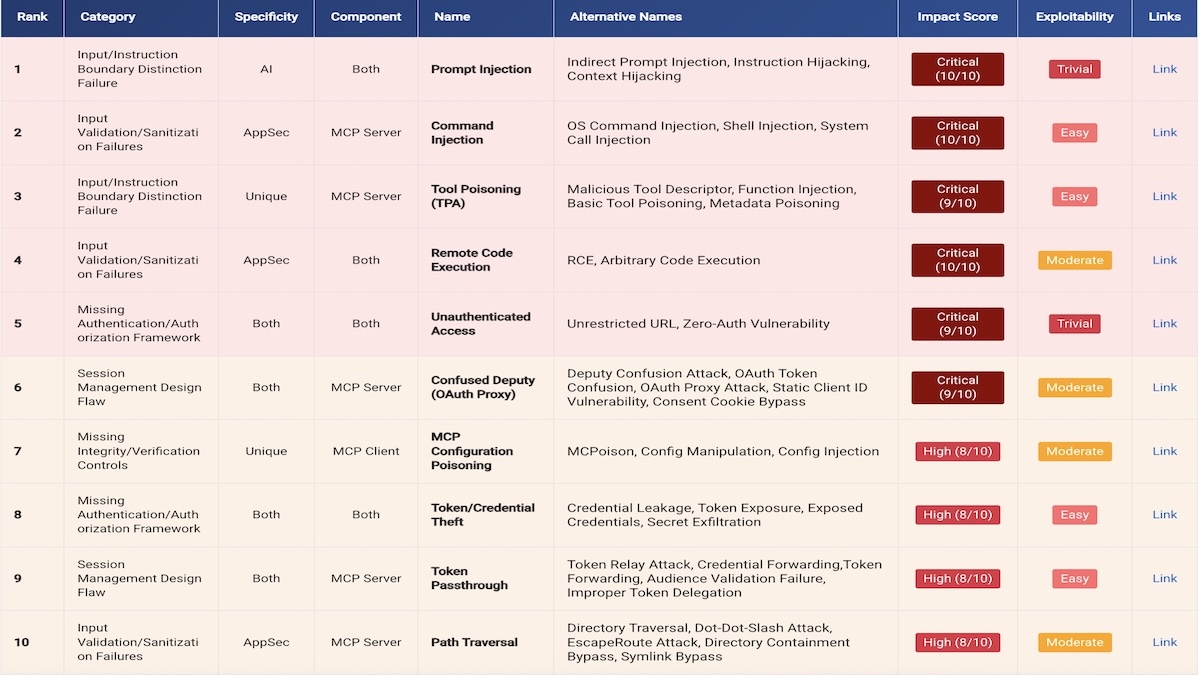
AI-specialist agency Adversa has now printed an evaluation of the Prime 25 MCP vulnerabilities, described as ‘probably the most complete thus far evaluation of MCP vulnerabilities’.
OWASP is thought to be planning its personal Prime Ten for MCP, however this isn’t but accessible and can (most likely) be restricted to 10 vulnerabilities. Adversa is just not attempting to compete with OWASP, however to supply speedy help for firms creating and implementing agentic AI options immediately. “We are going to map to OWASP/CSA/NIST the place related, and plan to contribute this work to the OWASP MCP effort because it formalizes,” Alex Polyakov (co-founder and CTO of Adversa AI) advised SecurityWeek.
The essential Adversa desk of vulnerabilities features a advisable ‘official’ identify (plus frequent AKAs), an influence rating, an exploitability score, and a hyperlink to further third get together explanatory data. The influence classification rating ranges from Vital (full system compromise or RCE) to low (data disclosure solely); whereas the exploitability degree ranges from trivial (may be exploited with simply primary information – no particular abilities aside from entry to a browser), to very complicated (theoretical solely, or requires nation state assets).
The rating determine is developed by a weighting algorithm: 40% influence + 30% exploitability + 20% prevalence + 10% remediation complexity. It can shock no-one that immediate injection stays the proper storm: combining crucial influence with trivial exploitability and ranked because the #1 vulnerability. Much less well-known is the MCP Choice Manipulation Assault (MPMA) with low influence and really complicated exploitability ranked at #24 – however nonetheless a vulnerability.
“We plan to replace the doc month-to-month, or every time new incidents or CVEs happen requiring a right away replace,” defined Polyakov. For the hyperlinks to additional studying, the doc defaults to the primary description of a vulnerability. However, he added, these hyperlinks will not be everlasting. “We’ll replace and broaden ‘additional studying’ when a clearer or extra rigorous supply emerges, and report it within the changelog.”
However the doc isn’t only a catalog of threats – it additionally supplies a sensible safety and mitigation guidelines together with ‘speedy’; a ‘protection in-depth technique’, and a ‘mitigation timeline’. Commercial. Scroll to proceed studying.
Quick steps embody: “Enter Validation is Necessary – 43% of MCP servers susceptible to command injection is inexcusable. Validate and sanitize ALL inputs.”
The protection technique contains 4 layers: protocol degree, software degree, AI-specific defenses, and infrastructure. Examples embody ‘implement TLS for all communications’ (protocol degree), and ‘use parameterized queries for database operations’ (software degree).
The mitigation timeline spreads over a three-month interval, beginning with ‘implement authentication on all uncovered endpoints’ (speedy) and together with ‘redesign structure for zero-trust mannequin’ (in month three).
Adversa has produced the primary full information to MCP vulnerabilities affecting probably the most popular space of IT immediately – the change from handbook human intelligence to automated synthetic intelligence. This information is designed to assist IT and safety departments perceive the complete complexity concerned.
Associated: Scalekit Raises $5.5 Million to Safe AI Agent Authentication
Associated: The Wild West of Agentic AI – An Assault Floor CISOs Can’t Afford to Ignore
Associated: Past GenAI: Why Agentic AI Was the Actual Dialog at RSA 2025
Associated: How Hackers Manipulate Agentic AI With Immediate Engineering