Cybersecurity professionals are dealing with an unprecedented acceleration in risk actor capabilities as the common breakout time—the interval from preliminary entry to lateral motion—has plummeted to a mere 18 minutes in the course of the June-August 2025 reporting interval.
This alarming statistic represents a dramatic discount from earlier timeframes, with the quickest recorded incident clocking in at simply six minutes when Akira ransomware operators compromised a SonicWall VPN and initiated lateral motion in file time.
The pace at which trendy risk actors function leaves defenders with extraordinarily slim home windows for detection and response.
ReliaQuest analysts have recognized that this acceleration stems from refined automation methods and the weaponization of authentic system instruments that evade conventional safety controls.
The convergence of drive-by compromises, USB-based malware distribution, and superior evasion methods creates an ideal storm for speedy community infiltration and compromise.
Drive-by compromises proceed to dominate preliminary entry vectors, accounting for 34% of incidents throughout this reporting interval.
Nevertheless, ReliaQuest researchers famous a regarding surge in USB-based assaults linked to Gamarue malware, which exploits the implicit belief organizations place in detachable media units.
The malware’s refined strategy includes hiding malicious Dynamic Hyperlink Libraries so successfully that the majority customers stay unaware of an infection, whereas malicious LNK recordsdata disguise themselves as authentic recordsdata already current on USB units.
Organizations listed on ransomware data-leak websites, by sector, throughout this reporting interval vs. the final reporting interval (Supply – Reliaquest)
The emergence of Oyster malware because the dominant risk has essentially altered the cybersecurity panorama.
Via refined search engine marketing poisoning campaigns powered by synthetic intelligence and automation, Oyster operators have scaled their operations to focus on IT directors particularly—recognizing that compromising these high-value accounts gives golden ticket entry to whole organizational infrastructures.
The malware leverages malvertising to distribute trojanized variations of authentic IT instruments like PuTTY via convincing pretend web sites reminiscent of puttysystems[.]com.
Superior Evasion Via System Binary Exploitation
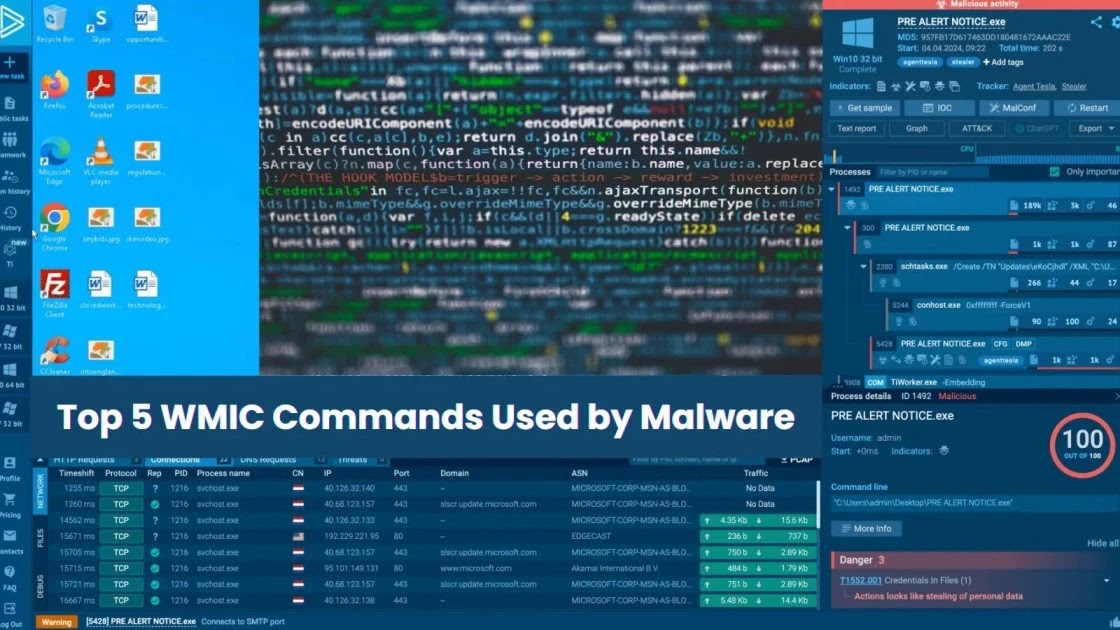
Oyster’s technical sophistication extends far past conventional malware capabilities via its strategic abuse of trusted Home windows system binaries, significantly rundll32.exe.
This authentic Home windows part has develop into the cornerstone of the malware’s evasion technique, enabling it to execute malicious DLLs whereas bypassing file-based detection mechanisms that safety options rely on.
The malware deploys a particular DLL named “twain_96.dll” via rigorously orchestrated scheduled duties that mimic authentic system exercise.
This strategy represents a basic shift in assault methodology, because it exploits the implicit belief that safety programs place in signed system binaries.
The scheduled duties are designed to look as routine upkeep operations, making detection via behavioral evaluation considerably tougher.
rundll32.exe twain_96.dll,DllRegisterServer
The persistence mechanism employed by Oyster demonstrates outstanding technical sophistication. Quite than counting on conventional registry modifications or startup folder entries that trendy endpoint detection programs actively monitor, the malware establishes scheduled duties that execute at seemingly random intervals.
These duties invoke rundll32.exe with particular parameters that load the malicious payload whereas sustaining the looks of authentic system processes.
ReliaQuest analysts recognized that Oyster alone accounts for 48% of incidents involving the “Match Legit Identify or Location” sub-technique, highlighting how the malware’s naming conventions and file placement methods efficiently deceive each automated safety instruments and human analysts.
The malware’s means to masquerade as trusted system recordsdata represents a essential evolution in evasion methods that organizations should handle via enhanced behavioral monitoring and anomaly detection capabilities.
Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates, Set CSN as a Most well-liked Supply in Google.