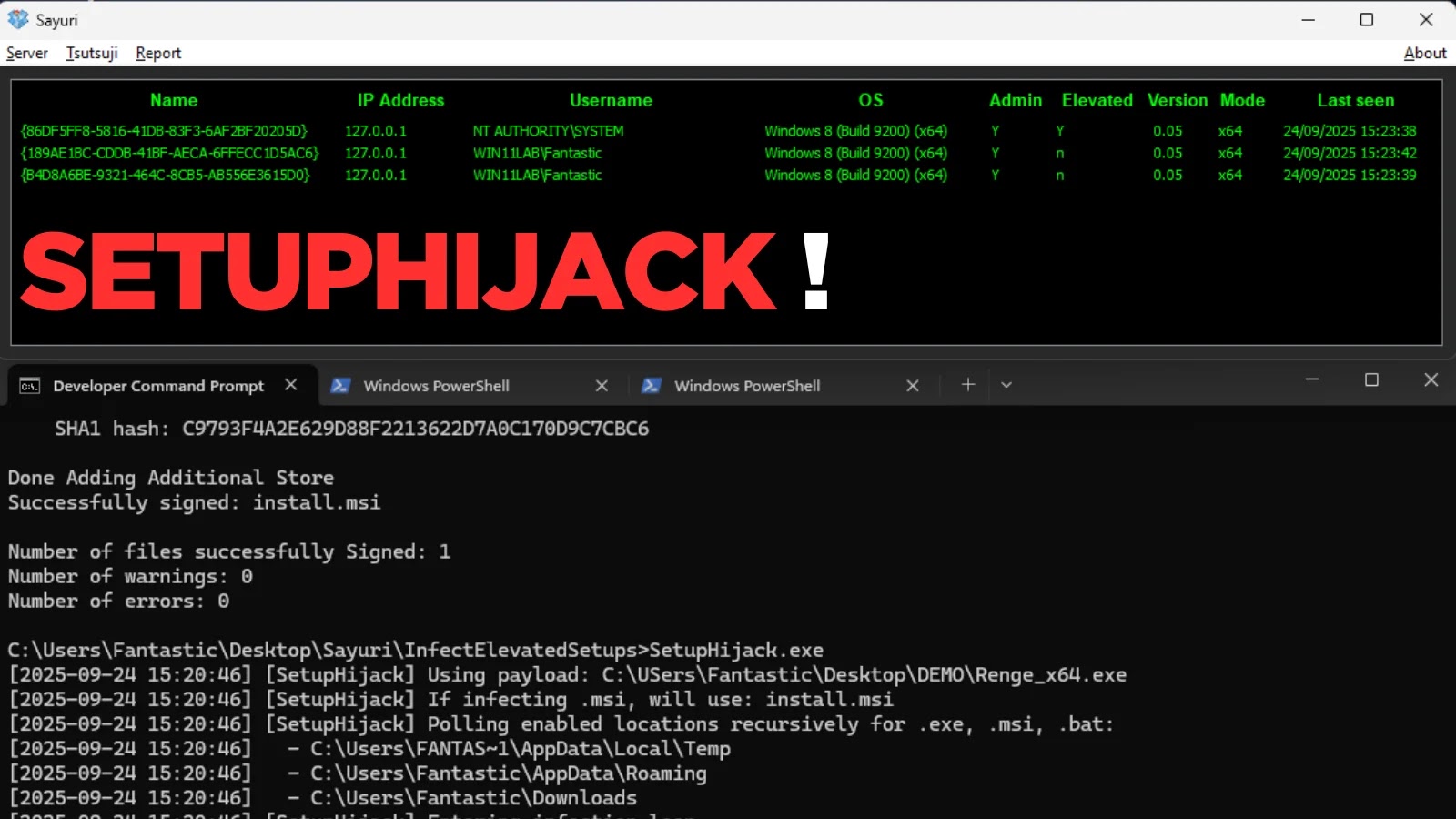
SetupHijack, an open-source analysis utility, has emerged as a strong technique for crimson teaming and safety analysis by concentrating on race situations and insecure file dealing with inside Home windows installer and replace mechanisms.
By polling world-writable directories equivalent to %TEMP%, %APPDATA%, and %USERPROFILEpercentDownloads, the instrument intercepts installer‐dropped payloads earlier than they execute with elevated privileges, enabling full SYSTEM or Administrator compromise with out requiring elevated permissions to run.
SetupHijack repeatedly scans specified directories for brand spanking new or modified installer recordsdata with extensions .exe, .msi, and .bat. When a goal file seems, the instrument atomically replaces it with a user-supplied payload, optionally preserving the unique file as a .bak backup.
If the privileged course of executes the substituted payload earlier than performing integrity checks, the attacker’s code runs beneath elevated rights.
Not like file system notification-based strategies, SetupHijack depends on high-frequency polling to reduce race-window durations.
SetupHijack Exploits Race Circumstances
Hacker Home acknowledged that the framework additionally subverts Authenticode code-signing and installer belief fashions by integrating a hacked signing course of utilizing SignToolEx.exe and SignToolExHook.dll, permitting payloads to bear legitimate certificates and Authenticode timestamps.
This strategy will increase the chance of bypassing digital signature verifications employed by many installers and OS protections.
Constructing the instrument is simple with Microsoft’s construct utilities:
The default execution scans widespread drop places, SetupHijack.exe. Flags permit fine-tuning of scan targets:
Further modes embody:
clear: Restores .bak backups throughout enabled directories.
verbose: Logs all actions, together with profitable payload substitutions.
For distant escalation on multi-user methods, SetupHijack can run alongside instruments like shadow.exe beneath a compromised person account, standing by till an administrative installer course of is launched.
In observe, safety researchers have noticed profitable infections of widespread functions equivalent to Zoom (model 6.6.1), the place the replace binary residing in %AppData% was hijacked to inject a customized implant.
Throughout demonstration runs, SetupHijack output logs present detailed an infection occasions:
Deploy an Implant
Safety Implications
Whereas SetupHijack is meant solely for approved testing and analysis, it underscores a vital weak point in lots of Home windows installer processes that belief recordsdata in world-writable directories.
Organizations ought to implement stricter file-drop places, implement sturdy integrity checks, and leverage safe coding practices to forestall time-of-creation/time-of-use (TOCTOU) assaults.
Moreover, signing installers with hardware-protected certificates and performing runtime signature validations can mitigate this class of exploitation.
As supply-chain and installer safety turn out to be more and more focused, instruments like SetupHijack function each a warning and a possibility to harden deployment workflows in opposition to subtle race-condition exploits.
Comply with us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.