Delegated Managed Service Accounts (dMSAs), launched in Home windows Server 2025, symbolize Microsoft’s newest innovation in safe service account administration.
Whereas designed to reinforce safety by stopping conventional credential theft assaults like Kerberoasting, safety researchers have uncovered potential abuse vectors that would enable attackers to determine persistent entry in Energetic Listing environments.
dMSAs had been created to unravel long-standing issues with conventional service accounts. In contrast to normal accounts that require handbook password administration, dMSAs present computerized credential administration and hyperlink authentication on to machine identities.
Based on Microsoft documentation, “dMSA is a safer and manageable strategy to service account administration in comparison with conventional service accounts”.
The know-how permits directors emigrate from typical service accounts whereas disabling the unique account’s password authentication, redirecting all requests by the Native Safety Authority (LSA) utilizing the brand new dMSA mechanism.
This function was particularly designed to get rid of credential theft dangers.
The Persistence Vector
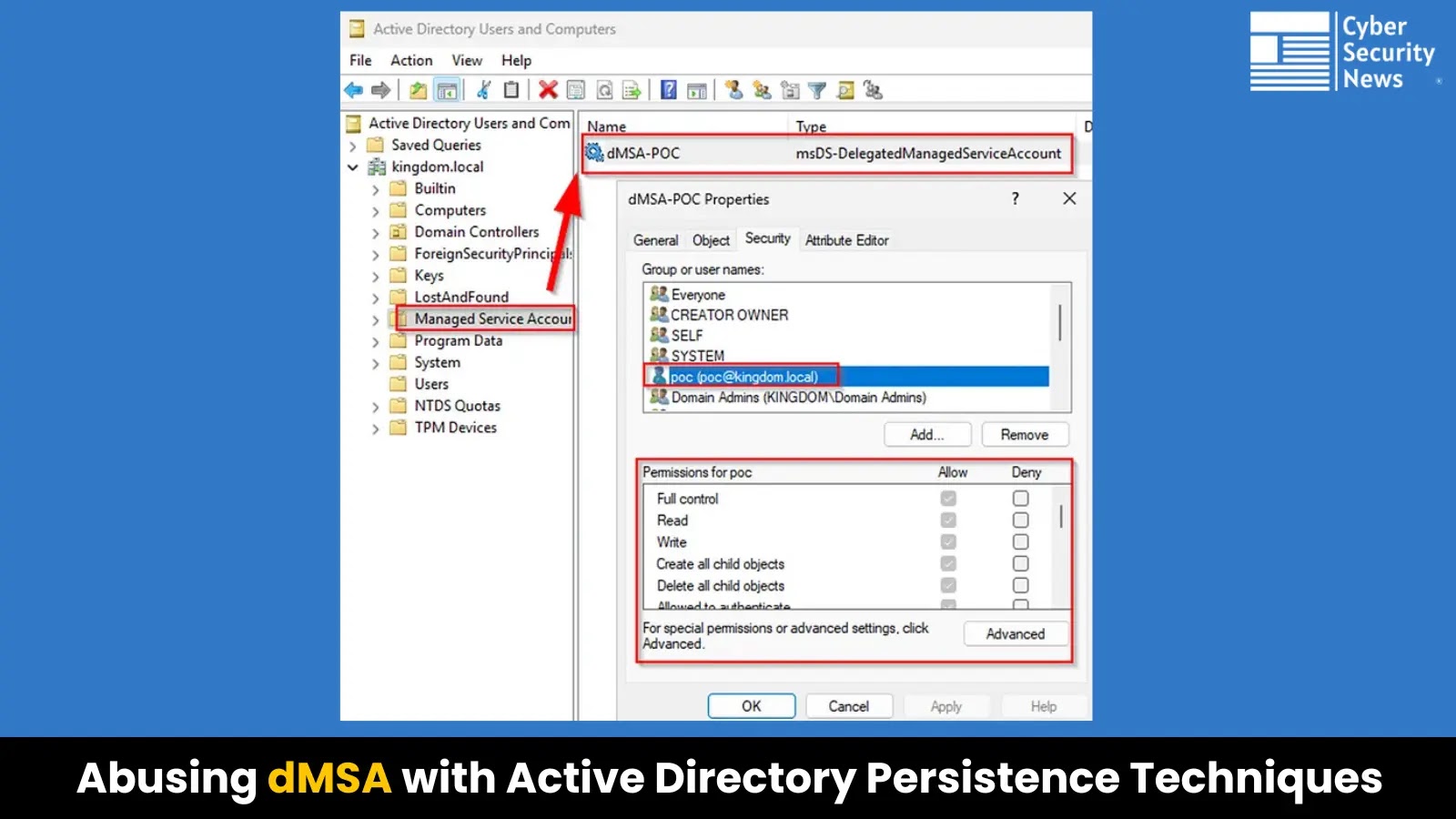
Based on Matan Bahar, regardless of enhanced safety controls, dMSAs can doubtlessly be abused by attackers who’ve quickly gained elevated privileges. The assault targets the Entry Management Lists (ACLs) of the dMSA objects themselves.
The important thing vulnerability lies within the “Managed Service Accounts” container and its permission inheritance construction.
An attacker with area administrator entry, even quickly, can modify ACLs to keep up entry to dMSA accounts after their privileged entry is revoked.
The assault begins by gaining “GenericAll” permissions on the Managed Service Accounts container:
Whereas having “GenericAll” permissions on the container doesn’t robotically grant entry to youngster objects, attackers can power inheritance right down to all dMSA objects:
These instructions set up persistent management over all present and future dMSA objects. The attacker can then:
Change possession of dMSA objects.
Create new dMSA accounts below their management.
Modify the PrincipalsAllowedToRetrieveManagedPassword property to incorporate their compromised accounts.
Mitigation
Organizations deploying Home windows Server 2025 ought to implement these protections:
Intently monitor modifications to the “Managed Service Accounts” container ACLs
Allow the Group Coverage setting: “Laptop ConfigurationAdministrative TemplatesSystemKerberosEnable Delegated Managed Service Account logons” solely on approved methods
Monitor for Occasion ID 4662, which signifies “Write” entry to dMSA objects.
Implement least privilege entry to Energetic Listing administrative teams.
Frequently audit ACL modifications on essential containers utilizing instruments like PingCastle or BloodHound.
Whereas dMSAs considerably enhance service account safety over conventional accounts, organizations should stay vigilant about potential abuse vectors.
Based on the Report, the safety enhancements supplied by dMSAs nonetheless outweigh the dangers, notably when correct monitoring and entry controls are applied.
As Microsoft continues to develop Home windows Server 2025, further safety controls round dMSA administration will probably emerge to deal with these newly found persistence strategies.
Vulnerability Assault Simulation on How Hackers Quickly Probe Web sites for Entry Factors – Free Webinar