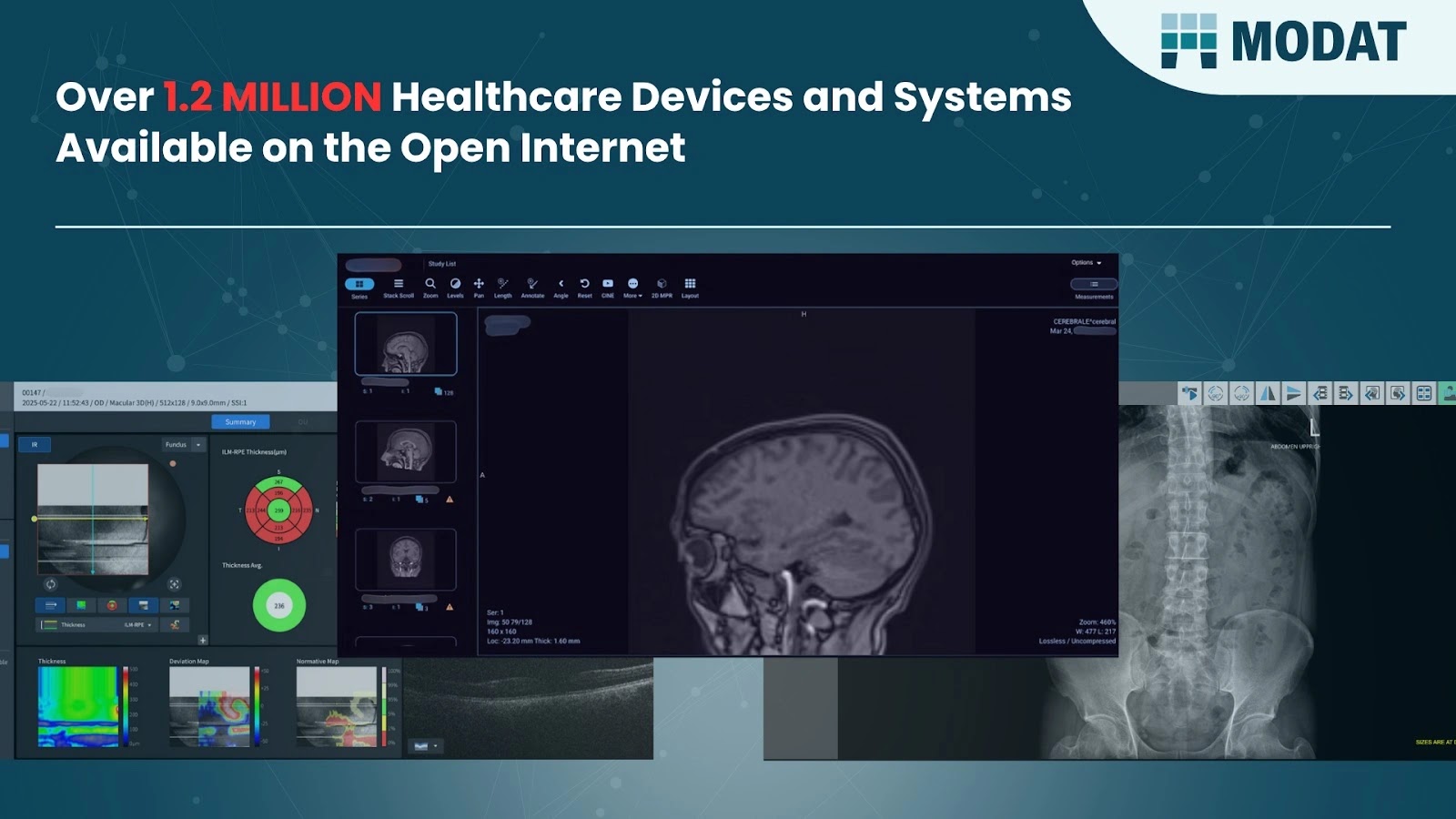
Over 1.2 million internet-connected healthcare gadgets and methods with publicity that endanger affected person information proven in new analysis by European cybersecurity firm Modat.
World findings displaying Prime 10 Areas (most outcomes are throughout Europe, the USA, and South Africa):
United States (174K+)
South Africa (172K+)
Australia (111K+)
Brazil (82K+)
Germany (81K+)
Eire (81K+)
Nice Britain (77K+)
France (75K+)
Sweden (74K+)
Japan (48K+)
Analysis was performed utilizing Modat’s distinctive web scanning platform, Modat Enlarge. Findings vary throughout greater than 70 various kinds of medical gadgets and methods together with: MRI, CT, X-rays, DICOM viewers, Blood check methods, hospital administration methods, and different accessible medical methods.
A number of Causes for Susceptible Units embrace misconfigurations and insecure administration settings, default or weak passwords, and unpatched vulnerabilities in firmware or software program.
Researchers found that many methods lacked even fundamental authentication, and a few used factory-default or weak passwords like, “admin” or “123456.”
In different circumstances, outdated or unpatched software program left crucial gadgets weak to exploitation. These oversights not solely compromise affected person confidentiality however can also open a path for cybercriminals to hold out fraud, extortion, or community infiltration.
One scan, as an illustration, uncovered a affected person’s chest and mind MRI outcomes, full with names and medical historical past. Data embrace extremely delicate data equivalent to Private Well being Data (PHI) and Private Figuring out Data (PII).
Their researchers have uncovered and recognized mind scan photos, full with sufferers’ names and scan dates.
Utilizing the identical methodology, they accessed a spread of different medical photos: eye exams from opticians, dental X-rays, blood check outcomes, and even detailed lung MRIs generally used to assist sufferers affected by lung most cancers.
A large variety of uncovered medical paperwork. All accessible by way of the open web – and in some circumstances, courting again to earlier years.
Modat labored with worldwide companions Well being-ISAC and Dutch CERT Z-CERT to make sure accountable disclosure.
The findings emphasize that cybersecurity in healthcare will not be solely an IT concern, but it surely’s a matter of affected person security.
They instantly initiated the method of Accountable Disclosure by reaching out to affected organisations to help them in fixing these safety breaches by organizations like Z-CERT and Well being-ISAC.
Here’s a hyperlink to the Well being-ISAC publish for his or her Month-to-month Menace Briefing (Month-to-month Menace Briefing)
These methods ought to by no means be uncovered to the web within the first place. Soufian El Yadmani, Modat CEO acknowledged, “The query we ought to be asking is: Why are there MRI scanners with web connectivity that lack correct safety measures?” El Yadmani went on to say, “The first danger is pointless community publicity.
These medical methods ought to solely be linked to safe, correctly configured networks when there’s a official scientific want for distant entry.
Whereas distant MRI operations have gotten extra frequent to handle staffing shortages and supply specialised experience, many methods stay uncovered to the web with out enough cybersecurity measures.”
Suggestions within the analysis embrace the necessity for organizations to implement common safety assessments and keep complete asset inventories, as personnel modifications and operational modifications can introduce configuration drift and safety gaps.
Steady monitoring of network-connected gadgets is crucial for figuring out potential exposures, misconfigurations, or rising vulnerabilities.
By doing that, healthcare services can considerably scale back their cybersecurity danger profile. As distant medical companies broaden and linked gadgets change into extra frequent, securing digital infrastructure is crucial.
The complete weblog publish, together with information visualizations and an in depth breakdown of findings, is out there right here.
About Modat
Based in 2024, Modat is a European research-driven cybersecurity firm targeted on strengthening cyber resilience for people, firms, and governments.
Our flagship platform, Modat Enlarge, leverages the world’s largest Web “Machine DNA” dataset to fingerprint and catalogue each internet-connected machine, creating a novel profile, enabling quicker menace intelligence.
Modat was created by researching, listening to, and instantly experiencing the wants and challenges of safety professionals.
Our merchandise allow the safety neighborhood by giving entry to unparalleled pace, contextualized information, and predictive insights.
We’re actively becoming a member of the combat to get forward of cyber-attacks by narrowing the rising hole between digital threats and resilience. Be a part of us to outpace and outlast.
Customers can study extra by visiting modat.io, and to entry the platform, go to amplify.modat.io
Go to: LinkedIn, X , BSky.
Contact
Head of MarketingBessie SchenkModat[email protected]