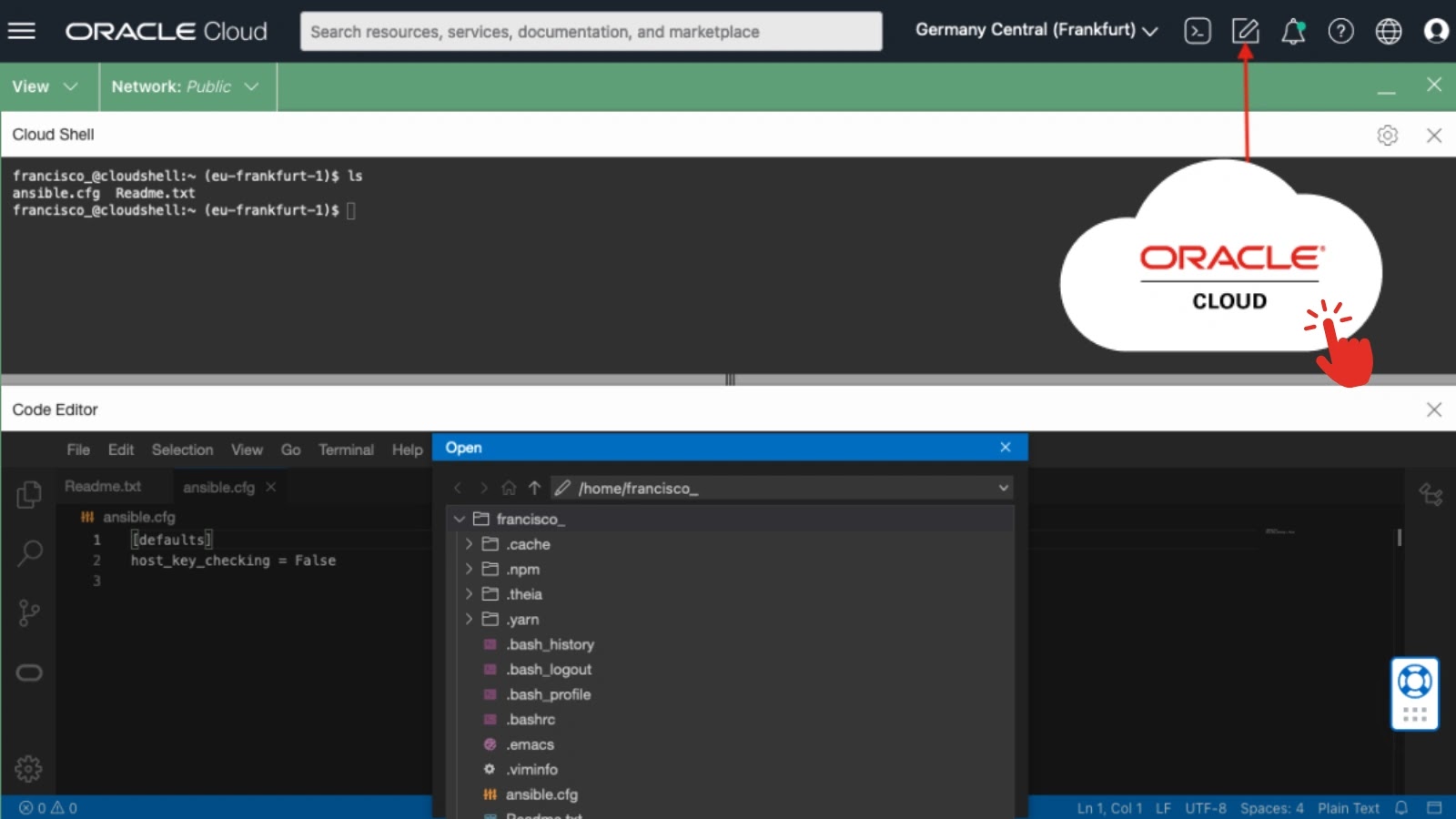
A crucial Distant Code Execution (RCE) vulnerability in Oracle Cloud Infrastructure (OCI) Code Editor that allowed attackers to silently hijack sufferer Cloud Shell environments via a single click on.
The vulnerability, now remediated, affected Code Editor’s built-in providers, together with Useful resource Supervisor, Capabilities, and Knowledge Science, demonstrating how seemingly remoted cloud growth instruments can change into assault vectors.
Key Takeaways1. Oracle Cloud Code Editor’s file add lacked CSRF safety, permitting 1-click malicious file uploads.2. Enabled Distant Code Execution and potential compromise of built-in OCI providers.3. Oracle added obligatory X-CSRF-Token headers to forestall cross-origin assaults.
Oracle Code Editor Vulnerability
The vulnerability stemmed from Oracle Code Editor’s deep integration with Cloud Shell, the place each providers share the identical underlying file system and person session context.
Whereas this tight coupling was designed to supply a seamless developer expertise, it created an sudden assault floor that researchers exploited.
Tenable’s investigation started with a easy query: if builders can add information simply via Code Editor, might attackers do the identical? This led to the invention of a /file-upload endpoint in Code Editor that lacked Cross-Web site Request Forgery (CSRF) defenses, not like Cloud Shell’s correctly secured add mechanism.
The crucial part on the coronary heart of this vulnerability was the Cloud Shell router (router.cloudshell.us-ashburn-1.oci.oraclecloud.com), which accepted HTTP POST requests containing multipart/form-data payloads.
The router used a CS-ProxyChallenge cookie configured with SameSite=None attribute, providing no safety towards cross-site requests from authenticated customers.
The exploitation path was remarkably easy. Attackers might create malicious HTML pages that, when visited by authenticated OCI customers, would routinely add malicious information to the sufferer’s Cloud Shell setting with out their data.
The assault utilized a crafted HTTP request:
Researchers demonstrated how attackers might override .bashrc information to ascertain reverse shells, gaining interactive entry to Cloud Shell and leveraging sufferer credentials for lateral motion throughout OCI providers utilizing the OCI CLI.
Safety Measures
Oracle responded to the vulnerability by implementing further safety measures, particularly requiring a customized HTTP header x-csrf-token with worth csrf-value for all related requests.
This transformation successfully mitigates CSRF assaults since browsers can’t routinely embody customized headers in cross-origin requests with out correct CORS configuration. The vulnerability’s affect prolonged past Cloud Shell to Code Editor’s built-in providers.
Since these providers function on the identical shared file system, malicious payloads might compromise Useful resource Supervisor workspaces, Capabilities deployments, and Knowledge Science environments, making a multi-surface risk throughout OCI’s developer toolkit.
This incident highlights the safety challenges inherent in cloud service integrations, the place comfort options can inadvertently broaden assault surfaces past their meant scope.
Enhance detection, cut back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Attempt ANY.RUN Now