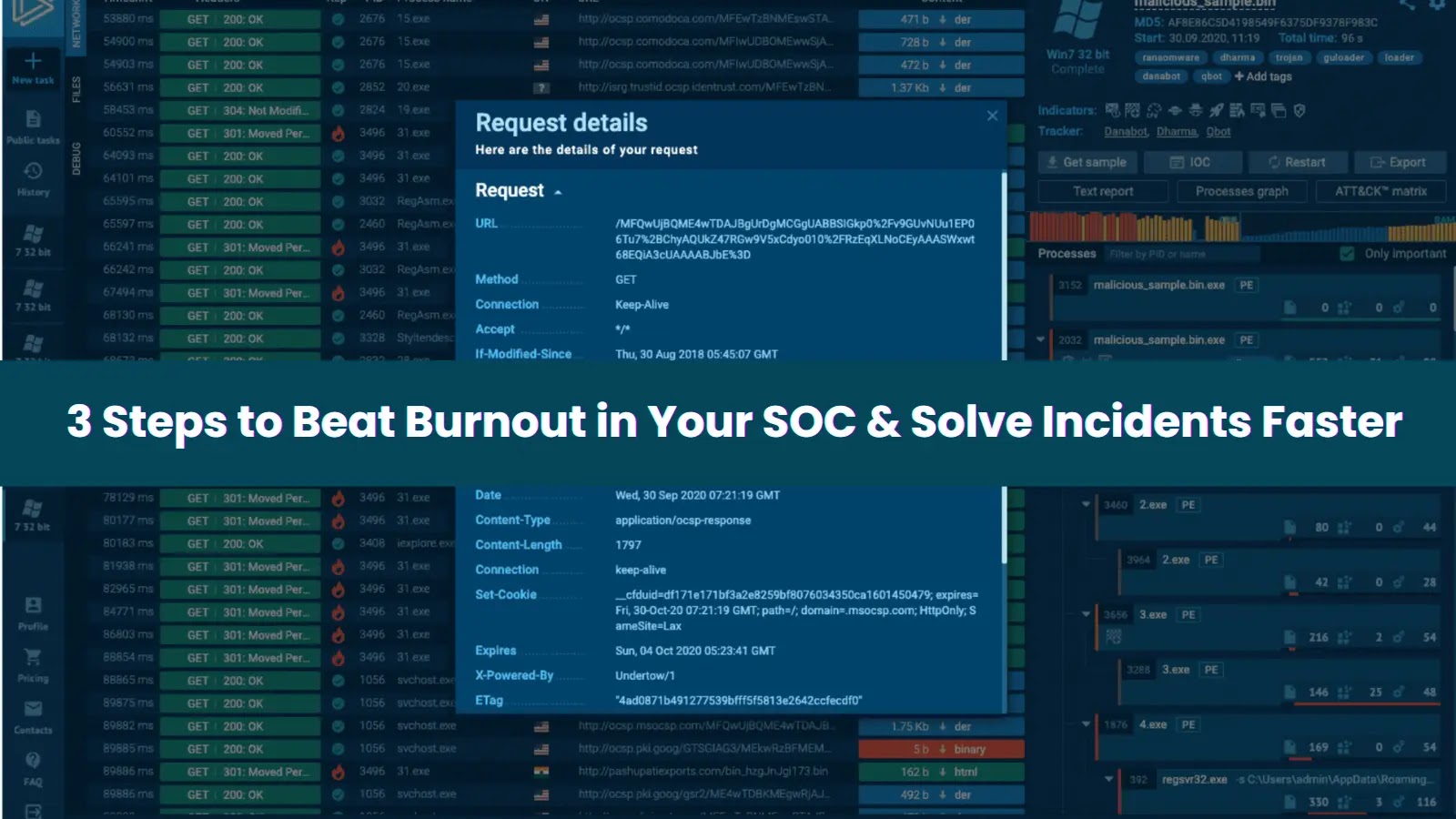
Safety groups are always on the transfer. Alerts by no means cease coming in, workloads preserve piling up, and the stress to react quick can put on anybody down. Add lengthy investigations and a maze of instruments on high of that, and burnout turns into virtually inevitable.
Nonetheless, it doesn’t should be this manner. With the suitable strategy, combining interactive sandboxing and good automation, SOCs can take the stress off, resolve incidents sooner, and preserve analysts centered on what issues most: catching threats earlier than they unfold.
Listed below are 3 ways to make that occur:
1. See and Discover Full Assault Chain in Actual Time
One huge cause analysts burn out is the fixed ready. Conventional instruments typically take hours to substantiate whether or not an alert is actual, forcing groups to chase uncertainty whereas the clock retains ticking. By the point a risk is verified, it could already be shifting via the community, and the workload has doubled.
Interactive sandboxes, reminiscent of ANY.RUN change that. As a substitute of counting on static reviews, analysts can watch an assault unfold reside inside a safe digital machine. Suspicious information, URLs, or scripts are detonated immediately, revealing each step of the habits chain, from preliminary dropper to payload, with out risking manufacturing methods.
That visibility turns sluggish, fragmented investigations into quick, assured choices. Analysts know precisely what they’re coping with and the best way to cease it, typically inside seconds.
For example, this evaluation session gave remaining verdict and full assault chain of LockBit 5.0 assault in simply 33 seconds:
View real-world assault uncovered in 33 secs
LockBit assault totally uncovered inside ANY.RUN sandbox in 33 seconds
In line with the latest analysis carried out by ANY.RUN workforce, firms utilizing interactive sandboxing had the next real-world outcomes:
88% of assaults change into seen throughout the 60 seconds of study.
Groups report as much as a 36% greater detection price on common.
See how your SOC can lower investigation time and deal with extra threats with much less stress. -> Speak to ANY.RUN Specialists
2. Discover Evasive Threats Earlier than They Drain Your Staff’s Time
Some assaults are constructed to remain hidden. They watch for the suitable person motion, a click on, a CAPTCHA, a file obtain, earlier than revealing their true habits. Conventional instruments can’t at all times simulate these steps, which implies analysts typically spend hours attempting to manually set off and analyze the assault chain.
ANY.RUN’s interactive sandbox modifications that. Its Automated Interactivity characteristic mimics actual person habits inside a safe digital machine, clicking hyperlinks, fixing CAPTCHAs, opening attachments, and following redirects, to show even essentially the most evasive threats routinely.
Meaning analysts now not have to repeat the identical guide steps for each case. What as soon as took hours, like uncovering a malicious hyperlink hidden in a QR code or a payload buried behind a number of redirects, can now be carried out in seconds.
Right here’s an instance of Automated Interactivity contained in the ANY.RUN sandbox:
View evaluation session with malicious QR code
ANY.RUN sandbox fixing CAPTCHA routinely
As proven within the session, the sandbox performs person actions by itself, uncovering the malicious hyperlink hidden in a QR code, fixing the CAPTCHA, and accumulating all behavioral indicators for fast evaluate. Analysts get a full report, full with IOCs and TTPs, with out spending an excessive amount of effort and time.
Nicely-structured report generated by ANY.RUN sandbox
Actual-world outcomes:
As much as 58% extra hidden threats recognized in comparison with conventional instruments.
30% fewer Tier 1 → Tier 2 escalations, as junior analysts can deal with extra incidents independently.
By automating the tedious components of study, SOCs discover evasive threats sooner, lower down investigation time, and free analysts to concentrate on higher-value work.
Even essentially the most expert workforce can lose momentum when instruments don’t work collectively. Leaping between dashboards, copying IOCs, and updating a number of methods manually eats away at beneficial investigation time, and provides to analyst frustration.
With ANY.RUN’s connectors, your sandbox, risk intelligence, and automation instruments all work in sync. The platform connects with fashionable SOC methods like QRadar, Cortex XSOAR, OpenCTI, and Microsoft Sentinel, letting analysts entry risk knowledge, behavioral insights, and enrichment straight from their fundamental workspace.
As a substitute of switching tabs, the context travels with you. Each alert is enriched with recent IOCs and actual behavioral knowledge, serving to groups make sooner and extra assured response choices.
Actual-world outcomes:
As much as 3× sooner response occasions due to a linked, zero-delay workflow.
Entry to 24× extra IOCs per case, powered by knowledge from over 15,000 SOCs worldwide.
By maintaining each system in sync, SOCs save time, get rid of repetitive work, and preserve a transparent, unified image of what’s taking place, all with out including further complexity.
Flip Overload into Quicker, Assured Response
SOC burnout doesn’t occur in a single day. It builds up via infinite alerts, guide work, and instruments that don’t match collectively. However when groups achieve real-time visibility, automate repetitive duties, and work inside one linked system, the stress begins to fade, and effectivity takes its place.
Analysts can concentrate on significant investigations as a substitute of chasing noise. Collaboration improves, and incidents get solved sooner, typically in a fraction of the time it used to take.
With interactive sandboxing, automation, and integrations that carry the whole lot collectively, ANY.RUN helps SOCs lower response time by a median of 21 minutes per case, turning each day overload into quick, assured motion.
Contact the ANY.RUN Enterprise workforce to see how your SOC can do the identical.